Abstract
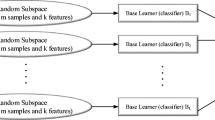
In this paper, we develop a new robust feature selection scheme and an evolving ensemble classifier for stego content classification in a steganalysis framework. Steganalysis vs. steganography is a classical competition between two opposing research areas. Steganography focuses on hiding data within any media source such that the modified content becomes statistically indistinguishable from the original non-modified media. On the other hand, steganalysis focuses on detecting modified media that contains hidden data. Steganalysis includes two major steps, viz., feature extraction and binary classification of the original vs. modified images. The proposed Robust Feature Selection Method along with a Cognitive Evolving Ensemble classifier (RFSM-CEE) uses a Robust Feature Selection Genetic Algorithm (RFSGA) for identifying the robust features. A new measure called Sample Hardness (H) is used to calculate the Classifier Cost and select those training samples with higher sample hardness to train a set of basic classifiers with the robust features. RFSGA uses a specially tailored classifier cost C as the fitness function, which indicates the importance of each basic classifier for further ensembling. The proposed Cognitive Evolving Ensemble classifier (CEE) uses a growing/deleting strategy along with a voting scheme coupled with an Adaptive Ensemble Genetic Algorithm to define the set of basic classifiers for efficient ensembling. CEE uses simple voting rules to make a decision about each sample. Detailed performance evaluation of RFSM-CEE has been carried out by conducting experiments using J-UNIWARD and heuristic Bose-Chaudhuri-Hocquenghem steganography. The data used in these experiments are from BOSSbase and BOWS2 databases, along with Cartesian calibration JPEG Rich Models features. Experimental results clearly indicate major improvements in detection compared to the JPEG steganalysis ensemble classifier proposed by Kodovsky. In this paper a Robust Feature Selection Method along with a Cognitive Evolving Ensemble classifier (RFSM-CEE) focusing on searching for robust features in steganalysis data is presented along with a more accurate classifier to build efficient steganalysis.




Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data Availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
Upham D. Steganographic algorithm JSteg. http://zooid.org/paul/crypto/jsteg.
Fridrich J. Feature-based steganalysis for JPEG images and its implications for future design of steganographic schemes. Lect Notes Comput Sci. 2004;3200:67–81.
Avcibus I, Kharrazi M, Memon ND, Sankur B. Image steganalysis with binary similarity measures. EURASIP J Adv Signal Process. 2005;17:2749–57.
Westfeld A. High capacity despite better steganalysis (F5: A steganographic algorithm). Lect Notes Comput Sci. 2001;2137:289–302.
Kodovsky J, Fridrich J, Dittman J, Craver S, Fridrich J. Calibration revisited. In: Proceeding of the 11th ACM Multimedia & Security Workshop, Princeton, NJ. 2009. pp. 63–74.
Fridrich J, Kodovsky J. Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur. 2012;7(3):868–82.
Zhang R, Sachnev V, Botnan MB, Kim HJ, Heo J. An efficient embedder for BCH coding for steganography. IEEE Trans Inf Theory. 2012;58(12):7272–9.
Schöfeld D, Winkler A. Reducing the complexity of syndrome coding for embedding. Lect Notes Comput Sci. 2008;4567:145–58.
Zhang R, Sachnev V, Kim HJ. Fast BCH syndrome coding for steganography. Lect Notes Comput Sci. 2009;5806:48–58.
Sachnev V, Kim HJ, Zhang R. Less detectable JPEG steganography method based on heuristic optimization and BCH syndrome coding. In: Proceedings of ACM Workshop on Multimedia and Security. 2009. pp. 131–139.
Filler T, Judas J, Fridrich J. Minimizing additive distortion in steganography using Syndrome-Trellis codes. IEEE Trans Inf Forensics Secur. 2011;6(3):920–35.
Chien RT. Cyclic decoding produce for the Bose-Chaudhuri-Hocquenghem codes. IEEE Trans Inf Theory. 1965;11:549–57.
Huang F, Huang J, Shi Y-Q. New channel selection rule for JPEG steganography. IEEE Trans Inf Forensics Secur. 2012;7(4):1181–91.
Guo L, Ni J, Shi YQ. Uniform embedding for efficient JPEG steganography. IEEE Trans Inf Forensics Secur. 2014;9(5):814–25.
Holub V, Fridrich J, Denemark T. Universal distortion function for steganography in an arbitrary domain. EURASIP J Inf Secur. 2014;2014:1.
Denemark T, Fridrich J. Side-informed steganography with additive distortion. Proceedings of the IEEE International Workshop on Information Forensics and Security. pp. 16–19. Nov. 2015.
Denemark T, Bas P, Fridrich J. Natural Steganography in JPEG Compressed Images. Proceedings of the IS&T, Electronic Imaging, Media Watermarking, Security, and Forensics 2018. Burlingame, CA; 2018.
Wang Y, Zhang W, Li W, Yu N. Non-additive cost functions for JPEG steganography based on block boundary maintenance. IEEE Trans Inf Forensics Secur. 2021;16:1117–30.
Goljan M, Fridrich J, Holotyak T. New blind steganalysis and its implications. In: Proceedings of the SPIE, Electronic Imaging, Security, Steganography, and Watermarking of Multimedia Contents VIII, vol. 6072. 2006. pp. 1–13.
Kodovsky J, Fridrich J. Steganalysis of JPEG images using rich models. Proceedings of SPIE, Electronic Imaging, Media Watermarking, Security, and Forensics XIV, San Francisco, CA January 23–25, 2012.
Kodovsky J, Fridrich J. Steganalysis in high dimensions: fusing classifiers built on random subspaces, Proceedings of SPIE, Electronic Imaging, Media, Watermarking, Security and Forensics XIII, San Francisco, CA, January 23-26, 2011.
Holub V, Fridrich J. Low complexity features for JPEG steganalysis using undecimated DCT. IEEE Trans Inf Forensics Secur. 2015;10(2).
Denemark T, Sedighi V, Holub V, Cogranne R, Fridrich J. Selection-channel-aware rich model for steganalysis of digital images. In: Proceedings of the IEEE International Workshop on Information Forensics and Security (WIFS). Dec. 2014. pp. 48–53.
Kodovsky J, Fridrich J, Holub V. Ensemble classifiers for steganalysis of digital media. IEEE Transactions on Information Security and Forensics. 2012;7(2):432–44.
Chen B, Feng GR, Zhang XP, Li FY. Mixing high-dimensional features for JPEG steganalysis with ensemble classifier. Signal, Image and Video Processing. https://doi.org/10.1007/s11760-012-0380-7.
Kodovsky J, Fridrich J. Quantitative steganalysis using rich models. SPIE, Electronic Imaging, Media Watermarking, Security, and Forensics XV, San Francisco, CA, February 3–7, 2013.
Hu D, Zhou S, Shen Q, Zheng S, Zhao Z, Fan Y. Digital image steganalysis based on visual attention and deep reinforcement learning. IEEE Access. 2019;7(1):25924–35.
Ma Y, Luo X, Li X, Bao Z, Zhao Z, Zhang Y. Selection of rich model steganalysis features based on decision rough set a-positive region reduction. IEEE Trans Circuits Syst Video Technol. 2019;29(2):336–50.
Friedman JH. Greedy function approximation: a gradient boosting machine. Ann Stat. 2000;29:1189–232.
Yousfi Y, Dworetzky E, Fridrich J. Detector-informed batch steganography and pooled steganalysis. Proceedings of the 2022 ACM Workshop on Information Hiding and Multimedia Security. 2022.
Butora J, Bas P. Fighting the reverse JPEG compatibility attack: pick your side. Proceedings of the 2022 ACM Workshop on Information Hiding and Multimedia Security. 2022.
Qian Y, Dong J, Wang W, Tan T. Deep learning for steganalysis via convolutional neural networks. In: Procedings of the SPIE, vol. 9409. 2015. p. 94090.
Xu G, Wu H-Z, Shi Y-Q. Structural design of convolutional neural networks for steganalysis. IEEE Signal Process Lett. 2016;23(5):708–12.
Ye J, Ni J, Yi Y. Deep learning hierarchical representations for image steganalysis. IEEE Trans Inf Forensics Secur. 2017;12(11):2545–57.
Boroumand M, Chen M, Fridrich J. Deep residual network for steganalysis of digital images. IEEE Trans Inf Forensics Secur. 2019;14(5):1181–93.
Yousfi Y, Butora J, Khvedchenya E, Fridrich JJ. ImageNet pre-trained CNNs for JPEG steganalysis. 2020 IEEE International Workshop on Information Forensics and Security (WIFS). 2020. pp. 1–6.
Yousfi Y, Butora J, Fridrich J, Clément FT. Improving EfficientNet for JPEG steganalysis. Proceedings of the 2021 ACM Workshop on Information Hiding and Multimedia Security. 2021. pp. 149–157.
Cogranne R, Giboulot Q, Bas P. The ALASKA steganalysis challenge: a first step towards steganalysis. Proceedings of the ACM Workshop on Information Hiding and Multimedia Security. 2019. pp. 125–137.
Yedroudj M, Chaumont M, Comby F, Ahmed OA, Bas P. Pixels-off: data-augmentation complementary solution for deep-learning steganalysis. Proceedings of the 2020 ACM Workshop on Information Hiding and Multimedia Security. 2020. pp. 39-48.
Butora J, Yousfi Y, Fridrich J. How to pretrain for steganalysis. Proceedings of the 2020 ACM Workshop on Information Hiding and Multimedia Security. 2021. pp. 143–148.
You W, Zhang H, Zhao X. A siamese CNN for image steganalysis. IEEE Trans Inf Forensics Secur. 2021;16(1):291–306.
Yousfi Y, Fridrich J. An intriguing struggle of CNNs in JPEG steganalysis and the OneHot solution. IEEE Signal Process Lett. 2020;27:830–4.
Sachnev V, Ramasamy S, Sundaram S, Kim HJ, Hwang HJ. A cognitive ensemble of extreme learning machines for steganalysis based on risk-sensitive hinge loss function. Cogn Comput. 2015;7(1):103–10.
Huang G-B. Learning capability and storage capacity of two-hidden layer feeforward networks. IEEE Trans Neural Netw. 2003;14(2):274–81.
Bass P, Filler T, Pevny T. Break Our Steganographic System - the ins and outs of organizing BOSS. In: Proceedings of 13th Information Hiding Conference, Prague, 2011.
Bass P, Furon T. Bows-2. Jul 2007. http://bows2.ec-lille.fr/BOWS2OrigEp3.tgz.
Holland IH. Adaptation in natural and artificial systems. University of Michigan: Press. Ann Arbor; 1975.
Goldberg DE. Genetic algorithms in search, optimization and machine learning. Addison-Wesley, New York; 1989. p 41.
Suresh S, Omkar SN, Mani V, Guru Prakash TN. Lift coefficient prediction at high angle of attack using recurrent neural network. Aerosp Sci Technol. 2003;7(8):595-602.
Acknowledgements
This work was supported by Catholic University of Korea, Research Fund 2020.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Research Involving Human Participants and/or Animals
This article does not contain any studies with human participants or animals performed by any of the authors.
Conflict of Interest
The authors declare no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sachnev, V., Sundararajan, N. & Suresh, S. A New Approach for JPEG Steganalysis with a Cognitive Evolving Ensembler and Robust Feature Selection. Cogn Comput 15, 751–764 (2023). https://doi.org/10.1007/s12559-022-10087-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12559-022-10087-3