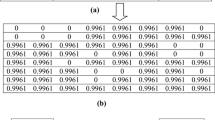
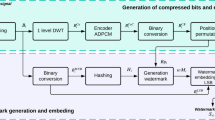
Abstract
When digital images are shared over an open access network such as the internet, facebook, WhatsApp, and other social media, then the security of these images are required. The digital watermarking is one approach for the security of images (e.g. copyright protection, ownership authentication). In most of the watermarking approaches, secret information such as owner binary logos and texts are used for protection of images. These days, biometric watermarks such as human speech signals are preferred for protection of images. In this paper, a watermarking technique based on various signal processing transforms is proposed and implemented for the security of image using human speech signal. In this technique, the first discrete cosine transform (DCT) and then singular value decomposition (SVD) are applied on the watermark speech signal to get its hybrid coefficients which are inserted into hybrid coefficients of the cover image to get a watermarked image. These hybrid coefficients of cover image are first generated using discrete wavelet transform (DWT) and then fast discrete curvelet transform (FDCuT) is applied on it. The performance of techniques is tested for standard speech database such as TIMIT in terms of imperceptibility, robustness and payload capacity. The experimental results and comparison show that the proposed watermarking technique performs better than the existing watermarking techniques available in the literature. This technique may also be used for security of speech signal against spoof attack.



















Similar content being viewed by others
References
Agarwal N, Singh AK, Singh PK (2019) Survey of robust and imperceptible watermarking. Multimedia Tools Appl. https://doi.org/10.1007/s11042-018-7128-5
Ali Z, Hossain MS, Muhammad GM, Aslam M (2018) New zero-watermarking algorithm using hurst exponent for protection of privacy in telemedicine. IEEE Access 6:7930–7940
Bhat V, Sengupta I, Das A (2010) An adaptive audio watermarking based on the singular value decomposition in the wavelet domain. Digit Signal Process 20(6):1547–1558
Borra S, Swamy GN (2013) Sensitive digital image watermarking for copyright protection. Int J Netw Secur (IJNS) 15(2):95–103
Borra S, Lakshmi HR, Dey N, Ashour A, Shi F (2017) Digital image watermarking tools: state-of-the-art. Front Artif Intell Appl 296:450–459
Candes E, Donoho D (2004) New tight frames of curvelets and optimal representations of objects with piecewise-C2 singularities. Commun Pure Appl Math 57:219–226
Candes E, Demanet L, Donoho D (2006) Fast discrete curvelet transforms. Multiscale Modell Simul 5(3):861–899
Cox IJ, Miller ML, Bloom JA (2000) Watermarking applications and their properties. In: Proceedings international conference on Information technology: coding and computing, 2000. IEEE. pp. 6–10
Edward S, Sumanthi S, Ranihemamalini R (2011) Person authentication using multimodal biometrics with watermarking. In: 2011 International conference on signal processing, communication, computing, and networking technologies, pp 100–104
El-Gazar S, Abbas AM, El-Dolil S, El-Dokany IM, Dessouky MI, El-Rabaie ESM, El-Samie FEA (2018) Efficient SVD speech watermarking with encrypted images. Int J Speech Technol 21(4):953–965
Feng G, Lin Q (2007) Iris feature based watermarking algorithm for personal identification. Int Symp Multispectral Image Process Pattern Recognit. https://doi.org/10.1117/12.748180
Golub GH, Reinsch C (1970) Singular value decomposition and least squares solutions. Numer Math 14(5):403–420
Inamdar V, Rege P (2014) Dual watermarking technique with multiple biometric watermarks. Sadhana 39(1):3–26
Inamdar V, Rege P, Arya M (2010) Offline handwritten signature based blind biometric watermarking and authentication technique using biorthogonal wavelet transform. Int J Comput Appl 11(1):19–27
Jain A (1989) Fundamentals of digital image processing. Prentice Hall Inc., New Jersey, pp 150–153
Jain A, Kumar A (2012) Second generation biometrics, the ethical, legal and social context. In: Mordini E, Tzovaras D (eds) Biometric recognition: an overview. Springer, Berlin, pp 49–79. https://doi.org/10.1007/978-94-007-3892-8_3
Jain A, Uludag U (2002) Hiding fingerprint minutiae in images. In: Proceedings of 3rd workshop on automatic identification advanced technologies, pp 97–102
Jain A, Uludag U (2003) Multimedia content protection via biometrics-based encryption. In: Proceedings of IEEE ICME’03, pp III-237
Jain A, Uludag U (2003b) Hiding biometric data. IEEE Trans Pattern Anal Mach Intell 25(11):1494–1498
Jain A, Uludag U, Hsu R (2002) Hiding a face in a fingerprint image. In: Proceedings of IEEE 16th international conference on pattern recognition, vol 3, pp 756–759
Jain A, Ross A, Prabhakar S (2004) An introduction to biometric recognition. IEEE Trans Circ Syst Video Technol 14(1):4–20
Jundale V, Patil S (2010) Biometric speech watermarking technique in images using wavelet transform. IOSR J Electr Commun Eng 33–39
Kaur M, Girdhar A, Kaur M (2010) Multimodal biometric system using speech and signature modalities. Int J Comput Appl 5(12):13–16
Ko T (2005) Multimodal biometric identification for large user population using fingerprint, face and iris recognition. In: Proceedings of the 34th workshop on applied imagery and pattern recognition. https://doi.org/10.1109/aipr.2005.35
Kumar C, Singh AK, Kumar P (2018) Improved wavelet-based image watermarking through SPIHT. Multimedia Tools Appl 15:1–14. https://doi.org/10.1007/s11042-018-6177-0
Kutter M, Petitcolas F (1999) A fair benchmark for image watermarking systems Electronic imaging’ 99. Secur Watermarking Multimedia Contents 3657:1–14
Langelaar G, Setyawan I, Lagendijk R (2000) Watermarking of digital image and video data—a state of art review. IEEE Signal Process Mag 20–46
Li S, Song S, Lu W, Sun D, Wei J (2017) Parameterization of LSB in self-recovery speech watermarking framework in big data mining. Secur Commun Netw 2017:1–12. https://doi.org/10.1155/2017/3847092
Mani M, Lakshmi T (2013) Speech watermarking using logarithmic approach. Int J Adv Res Electr Electr Instrum Eng 2(10):5007–5011
Merrad A, Saadi S (2018) Blind speech watermarking using hybrid scheme based on DWT/DCT and sub-sampling. Multimedia Tools Appl 77(20):27589–27615
Merrad A, Benziane A, Saadi S, Hafaifa A (2018a) Robust blind approach for digital speech watermarking. In: 2018 2nd international conference on natural language and speech processing (ICNLSP). IEEE, pp 1–5
Nematollahi M, Al-Haddad S, Zarafshan F (2015) Blind digital speech watermarking based on eigen-value quantization in DWT. J King Saud Univ Comput Inf Sci 27(1):58–67
Nematollahi M, Vorakulpipat C, Gamboa Rosales H (2017a) Semi fragile Speech watermarking based on least significant bit replacement of line spectral frequencies. Math Probl Eng 2017:1–9. https://doi.org/10.1155/2017/3597695
Nematollahi MA, Vorakulpipat C, Gamboa Rosales H (2017b) Optimization of a blind speech watermarking technique against amplitude scaling. Secur Commun Netw 2017:1–13. https://doi.org/10.1155/2017/5454768
Nguyen C, Tay D, Deng G (2006) A fast watermarking system for H.264/AVC video. In: Asia specific IEEE conference on circuits and systems, pp 81–84
Noore A, Singh R, Vatsa M, Houck M, Morris K (2006) Robust biometric image watermarking for fingerprint and face template protection. IEICE Electron Express 3(2):23–28
Noore A, Singh R, Vatsa M, Houck M (2007) Enhancing security of fingerprints through contextual biometric watermarking. Forensic Sci Int 169(2):188–194
Speech Signal database: http://freesound.org. Accessed 2017
Park K, Jeong D, Kang B, Lee E (2007) A study on iris feature watermarking on face data. In: Adaptive and natural computing algorithms, pp. 415–423. https://doi.org/10.1007/978-3-540-71629-7_47
Patel R, Sharwankar U, Thakare V (2011) Secure transmission of password using speech watermarking. Int J Comput Sci Technol 2(3):315–318
Ratha N, Connell J, Bolle R (2001) Enhancing security and privacy in biometric based authentication systems. IBM Syst J 40(3):614–634
Rege P (2012) Biometric watermarking. National Seminar on Computer Vision and Image Processing, Rajkot
Renza D, Dora L, Sanchez J (2016) Highly transparent steganography scheme of speech signals into color images using quantization index modulation. In: Mexican conference on pattern recognition. Springer, Champ, pp 241–250
Revathi A, Sasikaladevi N, Jeyalakshmi C (2018) Digital speech watermarking to enhance the security using speech as a biometric for person authentication. Int J Speech Technol 21(4):1021–1031
Saxena P, Khandelwal Y, Khandelwal R (2017) Haar transform for the numerical solutions of ordinary differential equations and boundary value problem with maple. Int J Eng Manag Sci 4(4):8–12
Singh AK (2019) Robust and distortion control dual watermarking in LWT domain using DCT and error correction code for color medical image. Multimedia Tools Appl. https://doi.org/10.1007/s11042-018-7115-x
Steinebach M, Petitcolas FA, Raynal F, Dittmann J, Fontaine C, Seibel S, Ferri LC (2001) StirMark benchmark: audio watermarking attacks. In: Proceedings international conference on information technology: coding and computing, 2001. IEEE, pp. 49–54
Talbi M, Fatima SB, Cherif A (2017) Speech modulation for image watermarking. In: 2017 International conference on control, automation and diagnosis (ICCAD). IEEE, pp 522–527
Thakkar F, Srivastava V (2017) A fast watermarking algorithm with enhanced security using compressive sensing and principle components and its performance analysis against a set of standard attacks. Multimedia Tools Appl 76(14):15191–15219
Thakur S, Singh AK, Ghrera SP, Elhoseny M (2018a) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimedia Tools Appl 78(3):3457–3470
Thakur S, Singh AK, Ghrera SP (2018b) NSCT domain–based secure multiple-watermarking technique through lightweight encryption for medical images. Concurr Comput Pract Exp 15:5108. https://doi.org/10.1002/cpe.5108
Thanki R, Borisagar K (2017) Watermarking scheme with CS encryption for security and piracy of digital audio signals. Int J Inf Syst Model Des (IJISMD) 8(4):38–60
Thanki RM, Kothari AM (2017) Digital watermarking: technical art of hiding a message. In: Intelligent analysis of multimedia information. IGI Global, pp 431–466
Thanki R, Borra S, Dwivedi V, Borisagar K (2017a) An efficient medical image watermarking scheme based on FDCuT–DCT. Eng Sci Technol Int J 20(4):1366–1379
Thanki R, Dwivedi V, Borisagar K, Borra S (2017b) A Watermarking algorithm for multiple watermarks protection using RDWT-SVD and compressive sensing. Inform Int J Comput Inf 41(4):479–493
Thanki R, Borra S, Brisagar K (2018a) A Hybrid watermarking technique for copyright protection of medical signals in teleradiology. handbook of research on information security in biomedical signal processing, pp. 320–349
Thanki R, Borisagar K, Borra S (2018b) Speech watermarking technique using the finite ridgelet transform, discrete wavelet transform, and singular value decomposition. In: Advance compression and watermarking techniques for speech signals. Springer, Cham, pp 27–45
Tsai SE, Yang SM (2018) An effective watermarking method based on energy averaging in audio signals. Math Probl Eng 2018:1–8. https://doi.org/10.1155/2018/6420314
University of South Carolina SIPI Image Database: http://sipi.usc.edu/database/database.php. Accessed 2017
Vatsa M, Singh R, Mitra R, Noore A (2004) Digital watermarking based secure multimodal biometric system. In: Proceedings of 2004 IEEE international conference on systems, man and cybernetics, pp. 2983–2987
Vatsa M, Singh R, Noore A (2009) Feature based RDWT watermarking for multimodal biometric system. Image Vis Comput 27(3):293–304
Vidakovic B (1999) Statistical modelling by wavelets. Wiley, Hoboken, pp 115–116
Yan J (2009) Wavelet matrix. Department of Electrical and Computer Engineering. University of Victoria, Victoria, BC, Canada, November, 1–2
Zhong J (2007) Watermark embedding and detection. arXiv preprint arXiv:0706.0427
Zue V, Seneff S, Glass J (1990) Speech database development at MIT: tIMIT and beyond. Speech Commun 9(4):351–356
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Thanki, R.M., Kothari, A.M. Hybrid domain watermarking technique for copyright protection of images using speech watermarks. J Ambient Intell Human Comput 11, 1835–1857 (2020). https://doi.org/10.1007/s12652-019-01295-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01295-1