Abstract
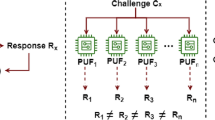
Internet of Things (IoT) refers to a network of embedded devices attached to everyday objects or things for facilitating remote monitoring and response. However, security is a major concern for IoT as traditional security approaches may not be suitable for IoT devices. Studies show that many of the IoT devices are vulnerable owing to weak passwords, insecure default security settings and lack of encryption when devices communicate over the network. In addition, most of these devices are often deployed in hostile environments making them inherently prone to physical and cloning attacks. Leveraging physically unclonable functions (PUFs) for device authentication is a promising approach to safeguard these devices against such attacks. However, the conventional strategy of storing challenge response pairs (CRPs) of the PUF explicitly in the database may make it vulnerable to machine learning or modeling attacks. Hence, we develop a novel lightweight and secure PUF based authentication protocol for IoT that leverages geometric threshold secret sharing to avoid explicit storage of CRPs for verification. Besides, we prototype the proposed protocol on Arduino Uno to analyze the memory requirements and thereby demonstrate the viability of the proposed protocol on resource-constrained devices. Further, we formally validate the security of the proposed scheme using the widely used AVISPA tool. Our security analysis reveals that the proposed protocol is resilient to cloning attacks, probing attacks, side-channel attacks and machine learning attacks by utilizing secret sharing. Finally, a comparison with existing schemes and security analysis of the proposed protocol reveals that our scheme is highly secure, lightweight, and suitable for IoT environments.











Similar content being viewed by others
References
Ali H, Tariq UU, Zheng Y, Zhai X, Liu L (2018a) Contention & energy-aware real-time task mapping on NoC based heterogeneous MPSoCs. IEEE Access 6:75110–75123
Ali H, Tariq UU, Zhai X, Liu L (2018b) Energy efficient task mapping & scheduling on heterogeneous NoC-MPSoCs in IoT based smart city. In: 2018 IEEE 20th international conference on high performance computing and communications, pp 1305–1313
Alladi T, Chamola V (2020) HARCI: a two-way authentication protocol for three entity healthcare IoT networks. IEEE J Sel Areas Commun 39(2):361–369
Aman MN, Sikdar B (2018) ATT-auth: a hybrid protocol for industrial IoT attestation with authentication. IEEE Internet Things J 5(6):5119–5131
Aman MN, Chua KC, Sikdar B (2017) Mutual authentication in IoT systems using physical unclonable functions. IEEE Internet Things J 4(5):1327–1340
Armando A, Basin D, Boichut Y, Chevalier Y, Compagna L, Cuéllar J, Hankes Drielsma P, Heám PC, Kouchnarenko O, Mantovani J, Mödersheim S, von Oheimb D, Rusinowitch M, Santiago J, Turuani M, Viganò L, Vigneron L (2005) The AVISPA tool for the automated validation of internet security protocols and applications. In: International conference on computer aided verification. Springer, Berlin, Heidelberg, pp 281–285
Armknecht F, Maes R, Sadeghi A-R, Sunar B, Tuyls P (2010) Memory leakage-resilient encryption based on physically unclonable functions. Towards hardware-intrinsic security. Springer, Berlin, pp 135–164
Blakley GR (1979) Safeguarding cryptographic keys. In: International workshop on managing requirements knowledge (MARK). IEEE Computer Society, pp 313–318
Boyd C, Mathuria A, Stebila D (2003) Protocols for authentication and key establishment, vol 1. Springer, Berlin
Braeken A (2018) PUF based authentication protocol for IoT. Symmetry 10(8):352
Byun JW (2019) End-to-end authenticated key exchange based on different physical unclonable functions. IEEE Access 7:102951–102965
Chatterjee U, Chakraborty RS, Mukhopadhyay D (2017) A PUF-based secure communication protocol for IoT. ACM Trans Embed Comput Syst TECS 16(3):1–25
Chatterjee U, Govindan V, Sadhukhan R, Mukhopadhyay D, Chakraborty RS, Mahata D, Prabhu MM (2018) Building PUF based authentication and key exchange protocol for IoT without explicit CRPS in verifier database. IEEE Trans Dependable Secure Comput 16(3):424–437
Che W, Martin M, Pocklassery G, Kajuluri VK, Saqib F, Plusquellic J (2017) A privacy-preserving, mutual PUF-based authentication protocol. Cryptography 1(1):3
Delvaux J, Peeters R, Gu D, Verbauwhede I (2015) A survey on lightweight entity authentication with strong PUFs. ACM Comput Surv CSUR 48(2):1–42
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Fakroon M, Gebali F, Mamun M (2021) Multifactor authentication scheme using physically unclonable functions. Internet Things 13:100343
Gassend B, Dijk MV, Clarke D, Torlak E, Devadas S, Tuyls P (2008) Controlled physical random functions and applications. ACM Trans Inf Syst Secur TISSEC 10(4):1–22
He D, Kumar N, Lee J-H, Sherratt RS (2014) Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans Consum Electron 60(1):30–37
Helfmeier C, Boit C, Nedospasov D, Seifert JP (2013) Cloning physically unclonable functions. In: 2013 IEEE international symposium on hardware-oriented security and trust (HOST). IEEE, pp 1–6
Herder C, Yu M-D, Koushanfar F, Devadas S (2014) Physical unclonable functions and applications: a tutorial. Proc IEEE 102(8):1126–1141
Khan MA, Salah K (2018) IoT security: review, blockchain solutions, and open challenges. Future Gener Comput Syst 82:395–411
Kim S, Lee I (2018) IoT device security based on proxy re-encryption. J Ambient Intell Humaniz Comput 9(4):1267–1273
Lee I, Lee K (2015) The internet of things (IoT): applications, investments, and challenges for enterprises. Bus Horiz 58(4):431–440
Liang W, Xie S, Long J, Li K-C, Zhang D, Li K (2019) A double PUF-based RFID identity authentication protocol in service-centric internet of things environments. Inf Sci 503:129–147
Majzoobi M, Rostami M, Koushanfar F, Wallach DS, Devadas S (2012) Slender PUF protocol: a lightweight, robust, and secure authentication by substring matching. In: 2012 IEEE symposium on security and privacy workshops. IEEE, pp 33–44
Merli D, Schuster D, Stumpf F, Sigl G (2011) Semiinvasive EM attack on FPGA RO PUFs and countermeasures. In: Proceedings of the workshop on embedded systems security, pp 1–9
Nimmy K, Sankaran S, Achuthan K (2018) A novel multi-factor authentication protocol for smart home environments. In: Ganapathy V, Jaeger T, Shyamasundar R (eds) Information systems security. Springer International Publishing, Cham, pp 44–63
Pappu R (2001) Physical one-way functions. Ph. D. thesis, Massachusetts Institute of Technology, Cambridge, Mass, USA
Patil AS, Hamza R, Hassan A, Jiang N, Yan H, Li J (2020) Efficient privacy-preserving authentication protocol using PUFs with blockchain smart contracts. Comput Secur 97:101958
Qureshi MA, Munir A (2019) PUF-RLA: a PUF-based reliable and lightweight authentication protocol employing binary string shuffling. In: 2019 IEEE 37th international conference on computer design (ICCD), pp 576–584
Ronan Saillard TG (n.d.) Cas+. Retrieved 2011. http://people.irisa.fr/Thomas.Genet/span/CAS_manual.pdf. Accessed 3 Feb 2017
Rührmair U, Sehnke F, Sölter J, Dror G, Devadas S, Schmidhuber J (2010) Modeling attacks on physical unclonable functions. In: Proceedings of the 17th ACM conference on computer and communications security, pp 237–249
Shakshuki EM, Malik H, Yasar AUH (2020) Special issue on ubiquitous computing in the IoT revolution. J Ambient Intell Human Comput 11:2203–2204
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Shamsoshoara A (2019) Overview of Blakley’s secret sharing scheme. arXiv preprint arXiv:1901.02802
Shivraj V, Rajan M, Singh M, Balamuralidhar P (2015) One time password authentication scheme based on elliptic curves for internet of things (IoT). In: 2015 5th National symposium on information technology: towards new smart world (NSITNSW), pp 1–6
Stergiou C, Psannis KE, Kim B-G, Gupta B (2018) Secure integration of IoT and cloud computing. Future Gener Comput Syst 78:964–975
Tariq UU, Ali H, Liu L, Panneerselvam J, Zhai X (2019) Energy-efficient static task scheduling on VFI-based NoC-HMPSoCS for intelligent edge devices in cyber-physical systems. ACM Trans Intell Syst Technol TIST 10(6):1–22
Zheng Y, Tariq UU, Ali H (2019) Big data security in internet of things. In: Security and privacy for big data, cloud computing and applications, pp 47–66
Acknowledgements
K. Nimmy would like to acknowledge the support under the Visvesvaraya PhD Scheme for Electronics and IT from the Ministry of Electronics and Information Technology (MeitY), Government of India.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Nimmy, K., Sankaran, S. & Achuthan, K. A novel lightweight PUF based authentication protocol for IoT without explicit CRPs in verifier database. J Ambient Intell Human Comput 14, 6227–6242 (2023). https://doi.org/10.1007/s12652-021-03421-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-021-03421-4