Abstract
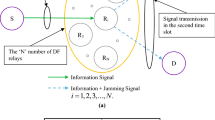
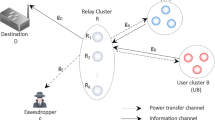
This paper presents a novel energy-efficient Radio Frequency (RF) Energy Harvesting (EH) scheme for secrecy performance in Internet of Things (IoT) network using cooperative communication approach under dissimilar faded channel environments. We have combined the concept of Destination Based Jamming (DBJ) with power beacon aided EH in our model. This paper provides three scenarios when the links undergo rayleigh fading, weibull fading, and nakagami-q (hoyt) fading where the effect of fading on the secrecy performance has been examined. Closed-form expressions for Secrecy Rate (SR) and System Energy Efficiency (SEE) are derived for the given scenarios. Analytical expressions have been well substantiated through extensive simulation results. The comparative analysis of system performance in terms of SR with respect to some important system parameters has been shown for various conventional protocols i.e., Decode-and-Forward (DF), Amplify-and-Forward (AF) and Hybrid-Decode-Amplify-Forward (HDAF). Furthermore, our scheme has been compared with benchmark techniques such as Cooperative Relaying (CR) and Cooperative Jamming (CJ) to quantify the performance improvement. Theoretical analysis and simulated results reveal the improvement of our proposed Signal-to-Noise (SNR) based hybrid decode-amplify forward Cooperative IoT (CIoT) scheme over existing relaying schemes which are further validated through statistical analysis. Results also depict the impact of eavesdropper position on secrecy performance at different channel mean power values. Finally, the SEE has been addressed and the impact of power splitting factor and transmit beacon power on the secrecy performance on the proposed model has also been analyzed with respect to change in fading parameters.











Similar content being viewed by others
Data availability
Not applicable.
Code availability
Not applicable.
References
Ali H, Tariq UU, Zheng Y, Zhai X, Liu L (2018) Contention & energy-aware real-time task mapping on NOC based heterogeneous MPSOCs. IEEE Access 6:75110–75123
Ali H, Tariq UU, Hussain M, Lu L, Panneerselvam J, Zhai X (2020) ARSH-FATI a novel metaheuristic for cluster head selection in wireless sensor networks. IEEE Syst J 15(2):2386–2397. https://doi.org/10.1109/jsyst.2020.2986811
Ali H, Tariq UU, Liu L, Panneerselvam J, Zhai X (2019) Energy optimization of streaming applications in IoT on NoC based heterogeneous MPSoCs using re-timing and DVFs. In: 2019 IEEE smart world, ubiquitous intelligence & computing, advanced & trusted computing, scalable computing & communications, cloud & big data computing, internet of people and smart city innovation (SMART WORLD /SCALCOM/UIC/ATC/CBD Com/IOP/SCI), pp 1297–1304
Bai Z, Jia J, Wang CX, Yuan D (2015) Performance analysis of SNR-based incremental hybrid decode-amplify-forward cooperative relaying protocol. IEEE Trans Commun 63(6):2094–2106. https://doi.org/10.1109/jsyst.2020.2986811
Chen X, Lei L, Zhang H, Yuen C (2015) Large-scale mimo relaying techniques for physical layer security: AF or DF? IEEE Trans Wirel Commun 14(9):5135–5146
Chen RC, Hsieh CF, Chang WL (2016) Using ambient intelligence to extend network lifetime in wireless sensor networks. J Ambient Intell Human Comput 7(6):777–788
Chen H, Liu J, Zhai C, Zheng L (2010) Performance analysis of SNR based hybrid decode amplify-forward cooperative diversity networks over rayleigh fading channels. In: 2010 IEEE wireless communication and networking conference (WCNC), pp 1–6
Gradshteyn IS, Ryzhik IM (2007) Tables of integrals, series, and products. Academic Press, London, UK
Gurrala KK, Das S (2017) Performance study of hybrid decode–amplify–forward (HDAF) relaying scheme for physical layer security in wireless cooperative network. Int J Commun Syst. https://doi.org/10.1002/dac.3182
He X, Yener A (2009) Two-hop secure communication using an untrusted relay. J Wirel Commun Netw. https://doi.org/10.1155/2009/305146
Hossain E, Rasti M, Tabassum H, Abdelnasser A (2014) Evolution toward 5g multi-tier cellular wireless networks: an interference management perspective. IEEE Wirel Commun 21(3):118–127
Hu L et al (2017) Cooperative jamming for physical layer security enhancement in internet of things. IEEE Internet Things J 5(1):219–228. https://doi.org/10.1109/JIOT.2017.2778185
Huang J, Mukherjee A, Swindlehurst, (2015) Secure communication via an untrusted non-regenerative relay in fading channels. IEEE Trans Signal Process 61(10):2536–2550
Huang Z, Niu Q, Xiao S, Li T (2020) Energy harvesting algorithm considering max flow problem in wireless sensor networks. Comput Commun 150:626–633
Jameel F, Javed MA, Jayakody DN, Hassan SA (2018) On secrecy performance of industrial internet of things. Internet Technol Lett 1(2):e32
Lei H, Dai Z, Park K, Lei W, Pan G, Alouini M (2018) Secrecy outage analysis of mixed RF-FSO downlink SWIPT systems. IEEE Trans Commun 66(12):6384–6395. https://doi.org/10.1109/TCOMM.2018.2865944
Mamaghani MT, Kuhestani A, Wong K (2018) Secure two-way transmission via wireless-powered untrusted relay and external jammer. IEEE Trans Veh Technol 67(9):8451–8465. https://doi.org/10.1109/TVT.2018.2848648
Nguyen TN, Tran M, Nguyen TL, Ha DH, Voznak M (2019) Performance analysis of a user selection protocol in cooperative networks with power splitting protocol-based energy harvesting over nakagami-m/rayleigh channels. Electronics 8(4):448
Niyato D, Kim DI, Maso M, Han Z (2017) Wireless powered communication networks: research directions and technological approaches. IEEE Wirel Commun 24(6):88–97
Ouyang N, Jiang X, Bai E, Wang H (2017) Destination assisted jamming and beamforming for improving the security of AF relay systems. IEEE Access 5:4125–4131
Phan VD, Nguyen TN, Tran M, Trang TT, Voznak M, Ha DH, Nguyen TL (2019) Power beacon-assisted energy harvesting in a half-duplex communication network under co-channel interference over a rayleigh fading environment: energy efficiency and outage probability analysis. Energies. https://doi.org/10.3390/en12132579
Pourmohammad AM, Musevi NJ, Mohassel FM (2021) On the outage performance of energy harvesting NOMA-based simultaneous cooperate and transmit IoT networks. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-021-03520-2
Sharma S, Roy SD, Kundu S (2017) Two-way secure communication with two half-duplex DF relay. In: 2017 IEEE region 10 conference (TENCON) 869–874
Sheng Z, Yang S, Yu Y, Vasilakos AV, Mccann JA, Leung KK (2013) A survey on the IETF protocol suite for the internet of things: standards, challenges, and opportunities. Wirel Commun 20(6):91–98. https://doi.org/10.1109/MWC.2013.6704479
Singh R, Soni S, Rao RS, Kumar S (2017) A new closed form distribution and performance analysis of a composite weibull/log-normal fading channel. Wirel Pers Commun 92(3):883–900
Sinha R, Jindal P (2017) A study of physical layer security with energy harvesting in single hop relaying environment. In: 4th IEEE international conference on signal processing and integrated networks (SPIN), pp 530–533
Srinivasan M, Kalyani S (2018) Secrecy capacity of κ-μ shadowed fading channels. IEEE Commun Lett 22(8):1728–1731
Tariq UU, Ali H, Lu L, John P, Xiaojun Z (2019) Energy-efficient static task scheduling on VFI-based NoC-HMPSoCs for intelligent edge devices in cyber-physical systems. ACM Trans Int Syst Technol. https://doi.org/10.1145/3336121
Vermesan O, Friess P (2014) Internet of things-from research and innovation to market deployment. River publishers, Denmark, pp 7–142
Yang J, Wu X, Peppas KP, Mathiopoulos PT (2021) Capacity analysis of power beacon-assisted energy harvesting MIMO system over shadowed fading channels. IEEE Trans Veh Technol. https://doi.org/10.1109/TVT.2021.3116190
Yao R, Xu F, Mekkawy T, Xu J (2016) Optimised power allocation to maximise secure rate in energy harvesting relay network. Electron Lett 52(22):1879–1881
Yu H, Lee H, Jeon H (2017) What is 5G? emerging 5G mobile services and network requirements. Sustainability 9(10):1848. https://doi.org/10.3390/su9101848
Zhang Y, Feng S, Tang W (2020) Performance analysis and optimization for power beacon-assisted wireless powered cooperative NOMA systems. IEEE Access 8:198436–198450
Zou Y, Zhu J, Wang X, Leung VC (2015) Improving physical-layer security in wireless communications using diversity techniques. IEEE Netw 29(1):42–48. https://arxiv.org/abs/1405.3725
Acknowledgements
We wish to express our appreciation to all the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflicts of interest to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix
Proof of proposition 1
The Cumulative Distribution Function (CDF) of the S-R link is given as:
where.
\(\psi_{X} = \frac{{\rho_{D} }}{{\rho_{S} }}\frac{{m_{x} }}{{m_{y} }}\); \(\rho_{S} = \frac{{P_{S} }}{{N_{O} }}\);\(\rho_{D} = \frac{{P_{D} }}{{N_{O} }}\)
where \(X_{AF} = \frac{{(1 - \beta )(\rho P_{S} )g_{SR} }}{{N_{O} }}\) and \(Y_{AF} = \mu^{2} g_{RD}\) are exponential random variables with mean \(\lambda_{{X_{AF} }} = \frac{{(1 - \beta )(\rho P_{S} )\Omega_{SR} }}{{N_{O} }}\) and \(\lambda_{{Y_{AF} }} = \mu^{2} \Omega_{RD}\); Using Eq. (4.352.1) and Eq. (4.331.2) in Gradshteyn and Ryzhik (2007), \(\varphi_{1}\) and \(\varphi_{2}\) can be calculated, respectively as.
where \(\Phi\) is the Euler’s constant [9.73].
Putting the value of \(\varphi_{1}\) and \(\varphi_{2}\) from (48) to (47) we have,
where \(Ei(.)\) is the exponential integral.
Capacity of EAV channel is given as:
After some simplification and manipulation:
The secrecy capacity of HDAF relay when operating in AF mode is given as:
The secrecy capacity of HDAF relay when operating in DF mode is given as:
where \(X_{DF} = \frac{{(1 - \beta )(\rho P_{S} )g_{SR} }}{{N_{O} }}\) and \(Y_{DF} = \frac{{\eta \beta g_{rd} }}{(1 - \beta )}\) are exponential random variables with means \(\lambda_{{X_{DF} }} = \frac{{(1 - \beta )(\rho P_{S} )\Omega_{SR} }}{{N_{O} }}\) and \(\lambda_{{Y_{DF} }} = \frac{{\eta \beta \Omega_{rd} }}{(1 - \beta )}\).
Capacity of EAV channel is given as:
After some simplification and manipulation:
Similarly, the secrecy capacity of HDAF relay when operating in DF mode is given as:
Thus substituting Eq. (48) and Eq. (51) in Eq. (31) we obtain Eq. (36). Putting Eq. (36) in Eq. (41) gives us the closed form equation for SEE.
Proof of proposition 2.
The pdf of main and wiretap links for weibull fading takes the following form:
where \(v_{m}\) is the fading factor of the main channel and \(\Gamma (.)\) is the gamma function, defined as:
\(v_{e}\) is the fading factor of the EAV channel.
Corresponding to (55) and (56), the CDF takes the following form:
The SR of the channel is defined as follows:
Substituting (20), (22), (55) and (56) into (59), we have:
After converting to single integral form, we have,
According to probability theory, we have:
Accordingly, the CDF is formulated as:
With several transformations, we obtain:
Thus
Thus, secrecy capacity of HDAF relay when operating in AF mode is given as:
Similarly, the secrecy capacity of HDAF relay when operating in DF mode is given as:
Thus substituting Eq. (63) and Eq. (64) in Eq. (31) we obtain Eq. (37) and thereafter the closed form equation for SEE.
Proof of proposition 3.
The pdf of S-R link for hoyt fading takes the following form:
where \(I_{O} (.)\) is the modified bessel function of the first kind and zero order, \(\overline{\gamma }_{RD} = {\rm E}\{ \gamma_{RD} \}\) and \(q \in [0,1]\)
For rayleigh faded channel, the capacity per unit bandwidth using optimum rate adaptation (ORA) policy is calculated as:
Now, for a hoyt faded channel, the capacity per unit bandwidth is calculated as:
where \(\gamma (\theta ,q) \triangleq \overline{\gamma }(1 - \frac{{1 - q^{2} }}{{1 + q^{2} }}\cos \theta )\)
where \(q_{m}\) and \(q_{e}\) represent the hoyt shape parameters for the desired and EAV links. Eccentricities associated with both hoyt distributions as \(\in_{RD} = \frac{{1 - q_{m}^{2} }}{{1 + q_{m}^{2} }}\) and \(\in_{RE} = \frac{{1 - q_{e}^{2} }}{{1 + q_{e}^{2} }}\)
Thus, secrecy capacity of HDAF relay when operating in AF mode is given as:
Similarly, the secrecy capacity of HDAF relay when operating in DF mode is given as:
Thus substituting Eq. (70) and Eq. (71) in Eq. (31) we obtain Eq. (38) followed by the closed form equation for SEE.
Rights and permissions
About this article
Cite this article
Thakur, C., Chattopadhyay, S. Secrecy performance of a novel energy efficient hybrid CIoT network with beacon-aided RF energy harvesting under dissimilar fading environments. J Ambient Intell Human Comput 13, 4057–4075 (2022). https://doi.org/10.1007/s12652-021-03589-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-021-03589-9