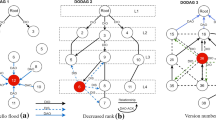
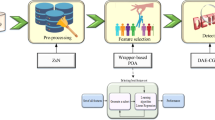
Abstract
The proliferation of connected devices under the Internet of things makes the adoption of Internet protocol version 6 (IPv6) is occurring faster and become more needed. It was designed and engineered to provide a much larger address space than its predecessor and provides better security. However, some newly introduced protocols in IPv6, such as neighbor discovery protocol (NDP), open up new vulnerabilities. NDP plays a vital role in IPv6 link-local communication. However, NDP is stateless and lacks messages authentication which exposes it to different types of attacks such as router advertisement (RA) flooding distributed denial of service attack. To address these issues, this paper proposes an approach based on deep learning to detect this kind of attack. In the proposed approach, two feature ranking algorithms, namely (1) one-rule and (2) Chi-squared are used to select the significant features that contribute to detect RA flooding attacks. The selected features are then used to feed Recurrent Neural Network which is used as the prediction model. The performance of the proposed approach is evaluated using a simulated IPv6 dataset and achieves an exceptional performance with 99.6% detection accuracy and a very low false-positive rate of 0.3%. In addition, the results reveal that the proposed approach outperforms the well-known state-of-the-art approach in terms of detection accuracy and false-positive rate.







Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abolhasanzadeh B (2015) Nonlinear dimensionality reduction for intrusion detection using auto-encoder bottleneck features. 2015 7th Conf Inf Knowl Technol IKT 2015 1–5. https://doi.org/10.1109/IKT.2015.7288799
Ahmed AA, Jabbar WA, Sadiq AS, Patel H (2020) Deep learning-based classification model for botnet attack detection. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-020-01848-9
Al Janabi KB, Kadhim R (2018) Data reduction techniques: a comparative study for attribute selection methods. Int J Adv Comput Sci Technol 8:1–13
Alamiedy TA, Anbar M, Al-Ani AK et al (2019a) Review on feature selection algorithms for anomaly-based intrusion detection system. Springer International Publishing, Cham
Alamiedy TA, Anbar M, Alqattan ZNM, Alzubi QM (2019b) Anomaly-based intrusion detection system using multi-objective grey wolf optimisation algorithm. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-019-01569-8
Alom MZ, Bontupalli V, Taha TM (2016) Intrusion detection using deep belief networks. Proc IEEE Natl Aerosp Electron Conf NAECON 2016-March, pp 339–344. https://doi.org/10.1109/NAECON.2015.7443094
Anbar M (2016) Review of security vulnerabilities in the IPv6 neighbor discovery protocol. Lect Notes Electr Eng 376:641–650. https://doi.org/10.1007/978-981-10-0557-2
Anbar M, Abdullah R, Hasbullah IH et al (2016) Comparative performance analysis of classification algorithms for intrusion detection system. 2016 14th Annu Conf Privacy. Secur Trust PST 2016:282–288. https://doi.org/10.1109/PST.2016.7906975
Anbar M, Abdullah R, Al-Tamimi BN, Hussain A (2018) A machine learning approach to detect router advertisement flooding attacks in next-generation IPv6 networks. Cognit Comput 10:201–214. https://doi.org/10.1007/s12559-017-9519-8
Drewek-Ossowicka A, Pietrołaj M, Rumiński J (2020) A survey of neural networks usage for intrusion detection systems. J Ambient Intell Humaniz Comput 12:497–514. https://doi.org/10.1007/s12652-020-02014-x
Elejla OE, Anbar M, Belaton B (2017) ICMPv6-based DoS and DDoS attacks and defense mechanisms: review. IETE Tech Rev (institution Electron Telecommun Eng India) 34:390–407. https://doi.org/10.1080/02564602.2016.1192964
Elejla OE, Anbar M, Belaton B, Alijla BO (2018) Flow-based IDS for ICMPv6-based DDoS attacks detection. Arab J Sci Eng 43:7757–7775. https://doi.org/10.1007/s13369-018-3149-7
Elejla OE, Anbar M, Belaton B, Hamouda S (2019) Labeled flow-based dataset of ICMPv6-based DDoS attacks. Neural Comput Appl 31:3629–3646. https://doi.org/10.1007/s00521-017-3319-7
Elsaeidy A, Munasinghe KS, Sharma D, Jamalipour A (2019) Intrusion detection in smart cities using restricted Boltzmann machines. J Netw Comput Appl 135:76–83. https://doi.org/10.1016/j.jnca.2019.02.026
Epishkina A, Finoshin M, Kogos K (2016) Information science and applications (ICISA) 2016. Lect Notes Electr Eng 376:641–650. https://doi.org/10.1007/978-981-10-0557-2
Farahnakian F, Heikkonen J (2018) A deep auto-encoder based approach for intrusion detection system. Int Conf Adv Commun Technol ICACT 2018-Febru, pp 178–183. https://doi.org/10.23919/ICACT.2018.8323688
Haider S, Akhunzada A, Ahmed G, Raza M (2019) Deep Learning based ensemble convolutional neural network solution for distributed denial of service detection in SDNs. 2019 UK/China Emerg Technol UCET 2019 1–4. https://doi.org/10.1109/UCET.2019.8881856
Hodo E, Bellekens X, Hamilton A et al (2017) Shallow and deep networks intrusion detection system: a taxonomy and survey. arXiv
Imamverdiyev Y, Abdullayeva F (2018) Deep learning method for denial of service attack detection based on restricted Boltzmann machine. Big Data 6:159–169. https://doi.org/10.1089/big.2018.0023
Kim J, Kim J, Thu HLT, Kim H (2016) Long short term memory recurrent neural network classifier for intrusion detection. 2016 Int Conf Platf Technol Serv PlatCon 2016-Proc. https://doi.org/10.1109/PlatCon.2016.7456805
Ko I, Chambers D, Barrett E (2020) Feature dynamic deep learning approach for DDoS mitigation within the ISP domain. Int J Inf Secur 19:53–70. https://doi.org/10.1007/s10207-019-00453-y
Li Q, Linhai M, Yuan YZ (2019) DDoS Attacks Detection Using Machine Learning Algorithms. Springer, Singapore
Liu Y, Liu S, Zhao X (2018) Intrusion detection algorithm based on convolutional neural network. Destech Trans Eng Technol Res. https://doi.org/10.12783/dtetr/iceta2017/19916
Liu H, Lang B, Liu M, Yan H (2019) CNN and RNN based payload classification methods for attack detection. Knowl Based Syst 163:332–341. https://doi.org/10.1016/j.knosys.2018.08.036
Mohammadpour L, Ling TC, Liew CS, Chong CY (2018) A convolutional neural network for network intrusion detection system. Proc Asia Pac Adv Netw 46:50–55
Ordabayeva GK, Othman M, Kirgizbayeva B et al (2020) A systematic review of transition from IPV4 to IPV6. ACM Int Conf Proc Ser. https://doi.org/10.1145/3410352.3410735
Sumathi S, Karthikeyan N (2020) Detection of distributed denial of service using deep learning neural network. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-020-02144-2
Tang TA, Mhamdi L, McLernon D et al (2018) Deep recurrent neural network for intrusion detection in SDN-based networks. 2018 4th IEEE Conf Netw Softwarization Work NetSoft 2018, pp 462–469. https://doi.org/10.1109/NETSOFT.2018.8460090
Ujjana RMA, Zeeshan Perveza KD (2019) Towards sFlow and adaptive polling sampling for deep learning based DDoS detection in SDN. Econ Lett. https://doi.org/10.1016/j.econlet.2019.108565
Yin C, Zhu Y, Fei J, He X (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5:21954–21961. https://doi.org/10.1109/ACCESS.2017.2762418
Zou Q, Ni L, Zhang T, Wang Q (2015) Deep learning based feature selection for remote sensing scene classification. IEEE Geosci Remote Sens Lett 12:2321–2325. https://doi.org/10.1109/LGRS.2015.2475299
Acknowledgements
This research was supported by Research University (RU) Grant, Universiti Sains Malaysia (USM) No: 1001.PNAV.8011107
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hasan, A.H., Anbar, M. & Alamiedy, T.A. Deep learning approach for detecting router advertisement flooding-based DDoS attacks. J Ambient Intell Human Comput 14, 7281–7295 (2023). https://doi.org/10.1007/s12652-022-04437-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-022-04437-0