Abstract
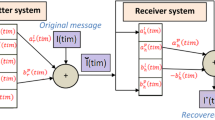
This research introduces a new method to tackle the issue of exchanging cryptographic keys in the Industrial Internet of Things (IIoT). This study focuses on the inefficiency and lengthy evaluation procedures of conventional cryptographic key exchange algorithms, which are not appropriate for the rapid and constantly changing IIoT device environment. In the solution domain, the proposed approach uses synchronization of neural networks with vector valued and Recurrent Neural Networks (RNNs), merging drive-response mechanisms to enhance speed and efficiency in crucial operations. The research examines the influence of postponements on the generating arbitrary inputs and coordination challenges in RNNs that incorporate drive-response mechanisms for synchronized input vector creation. This article explains an elementary evaluation of coordination in Artificial Neural Networks (ANNs) by utilizing an RNN framework to structure ANNs for sharing session keys. The study provides multiple contributions: (1) employing the polynomial coordination technique to generate coordinated inputs for the ANN synchronization process using RNNs, (2) using Lyapunov formulas and inequality assessment methods to identify required control parameters and time-varying conditions for achieving synchronization in the drive-response systems proposed with polynomial and non-polynomial functions, (3) demonstrating the connection between polynomial and non-polynomial synchronization with numerical illustrations, and (4) designing symmetric layouts of ANNs to create a session keys in the IIoT network. The suggested technique outperforms existing methods in the literature by offering a quicker, more dependable solution for cryptographic key exchange, paving the way for improved and secure industrial applications. This new method not only fixes current inefficiencies but also paves the way for future improvements in secure communication in the IIoT environment.















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availibility
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request
References
Bi B, Huang D, Mi B et al (2019) Efficient LBS security-preserving based on NTRU oblivious transfer. Wirel Pers Commun 108(4):2663–2674
Cao B, Wang X, Zhang W et al (2020) A many-objective optimization model of Industrial Internet of Things based on private blockchain. IEEE Netw 34(5):78–83
Chen C, Cui J, Qu G, Zhang J. WRITE+SYNC: Software Cache Write Covert Channels Exploiting Memory-disk Synchronization. In: IEEE Transactions on Information Forensics and Security. https://doi.org/10.1109/TIFS.2024.3414255
Chen J, Wang Q, Cheng HH et al (2022) A review of vision-based traffic semantic understanding in ITSs. IEEE Trans Intell Transp Syst 23(11):19954–19979
Chen J, Xu M, Xu W et al (2023) A flow feedback traffic prediction based on visual quantified features. IEEE Trans Intell Transp Syst 24(9):10067–10075
Dai W, Zhou X, Li D et al (2022) Hybrid parallel stochastic configuration networks for industrial data analytics. IEEE Trans Ind Inform 18(4):2331–2341
Ding Y, Zhang W, Zhou X et al (2021) FraudTrip: taxi fraudulent trip detection from corresponding trajectories. IEEE Internet Things J 8(16):12505–12517
Dolecki M, Kozera R (2015) The impact of the TPM weights distribution on network synchronization time. In: Computer information systems and industrial management, vol 9339. Springer, pp 451–460
Dong T, Huang T (2020) Neural cryptography based on complex-valued neural network. IEEE Trans Neural Netw Learn Syst 31(11):4999–5004. https://doi.org/10.1109/TNNLS.2019.2955165
Franois M, Grosges T, Barchiesi D (2014) Pseudo-random number generator based on mixing of three chaotic maps. Commun Nonlinear Sci Numer Simul 19(4):887–895
Guo R, Liu H, Liu D (2024) When Deep Learning-Based Soft Sensors Encounter Reliability Challenges: A Practical Knowledge-Guided Adversarial Attack and Its Defense. In: IEEE Transactions on Industrial Informatics 20(2):2702–2714. https://doi.org/10.1109/TII.2023.3297663
Hao J, Chen P, Chen J et al (2024) Multi-task federated learning-based system anomaly detection and multi-classification for microservices architecture. Future Gener Comput Syst 159:77–90
Jeong S, Park C, Hong D et al (2021) Neural cryptography based on generalized tree parity machine for real-life systems. Secur Commun Netw. https://doi.org/10.1155/2021/6680782
Jiang H, Wang M, Zhao P et al (2021) A utility-aware general framework with quantifiable privacy preservation for destination prediction in LBSs. IEEE/ACM Trans Netw 29(5):2228–2241
Jiang H, Xiao Z, Li Z et al (2022) An energy-efficient framework for Internet of Things underlaying heterogeneous small cell networks. IEEE Trans Mob Comput 21(1):31–43
Kumar A, Singh S, Das S et al (2023) Projective quasi-synchronization of complex-valued recurrent neural networks with proportional delay and mismatched parameters via matrix measure approach. Eng Appl Artifi Intell 126:106800. https://doi.org/10.1016/j.engappai.2023.106800
Li S, Chen J, Peng W et al (2023) A vehicle detection method based on disparity segmentation. Multimed Tools Appl 82(13):19643–19655
Li W, Susilo W, Xia C, Huang L, Guo F, Wang T, Li W et al (2024) Secure Data Integrity Check Based on Verified Public Key Encryption with Equality Test for Multi-Cloud Storage. In: IEEE Transactions on Dependable and Secure Computing 1:1–15. https://doi.org/10.1109/TDSC.2024.3375369
Li X, Lu Z, Yuan M et al (2024) Tradeoff of code estimation error rate and terminal gain in SCER attack. IEEE Trans Instrum Meas 73:1–12
Li Z, Zhou W, Zhou Z et al (2024) Self-supervised dynamic learning for long-term high-fidelity image transmission through unstabilized diffusive media. Nat Commun 15(1):1498
Liu D, Cao Z, Jiang H et al (2022) Concurrent low-power listening: a new design paradigm for duty-cycling communication. ACM Trans Sens Netw 19(1):1–24
Liu L, Miao S, Hu H et al (2016) Pseudo-random bit generator based on non-stationary logistic maps. IET Inf Secur 10:87–94
Liu L, Zhang S, Zhang L et al (2023) Multi-UUV maneuvering counter-game for dynamic target scenario based on fractional-order recurrent neural network. IEEE Trans Cybern 53(6):4015–4028
Liu Q, Yuan H, Hamzaoui R et al (2021) Reduced reference perceptual quality model with application to rate control for video-based point cloud compression. IEEE Trans Image Process 30:6623–6636
Liu Y, Jia Z, Jiang Z et al (2024) BFL-SA: blockchain-based federated learning via enhanced secure aggregation. J Syst Architect 152:103163
Luo J, Zhao C, Chen Q et al (2022) Using deep belief network to construct the agricultural information system based on Internet of Things. J Supercomput 78(1):379–405
Ma J, Hu J (2022) Safe consensus control of cooperative-competitive multi-agent systems via differential privacy. Kybernetika 58(3):426–439
Qi M, Cui S, Chang X, Xu Y, Meng H, Wang Y, Yin T, Arif M (2022) Multi-region Nonuniform Brightness Correction Algorithm Based on L-Channel Gamma Transform. Sec Commun Netw 2022. https://doi.org/10.1155/2022/2675950
Sarkar A (2021) Deep learning guided double hidden layer neural synchronization through mutual learning. Neural Process Lett 53:1355–1384. https://doi.org/10.1007/s11063-021-10443-8
Sarkar A (2022) Mutual learning-based efficient synchronization of neural networks to exchange the neural key. Complex Intell Syst 8:307–321
Sarkar A (2024) Recurrent neural networks-guided vector-valued synchronized key exchange for secure and privacy-preserving communication in Industrial Internet of Things. Appl Soft Comput 161:111731
Diah Septiyana, Mohamed Abd. Rahman, Tasnim Firdaus Mohamed Ariff, Nor Aiman Sukindar, Erry Yulian T. Adesta (2023). Enhancing Water Sustainability Index Assessment Through Risk Management, Iot, and Artificial Intelligence in Water Operation: A Review. Water Conservation & Management, 7(2): 97-106.
Shen X, Jiang H, Liu D et al (2022) PupilRec: leveraging pupil morphology for recommending on smartphones. IEEE Internet Things J 9(17):15538–15553
Song X, Wu N, Song S (2023) Switching-like event-triggered state estimation for reaction–diffusion neural networks against DoS attacks. Neural Process Lett 55:8997–9018
Song X, Wu N, Song S et al (2023) Bipartite synchronization for cooperative-competitive neural networks with reaction–diffusion terms via dual event-triggered mechanism. Neurocomputing 550:126498
Stojanovic V (2023) Fault-tolerant control of a hydraulic servo actuator via adaptive dynamic programming. J Math Model Control 2023(3):181–191
Stoyanov B, Kordov K (2015) Novel secure pseudo-random number generation scheme based on two tinkerbell maps. Adv Stud Theor Phys 9(9):411–421
Sun G, Li Y, Liao D et al (2018) Service function chain orchestration across multiple domains: a full mesh aggregation approach. IEEE Trans Netw Serv Manag 15(3):1175–1191
Sun G, Liao D, Zhao D et al (2018) Live migration for multiple correlated virtual machines in cloud-based data centers. IEEE Trans Serv Comput 11(2):279–291
Sun G, Zhu G, Liao D et al (2019) Cost-efficient service function chain orchestration for low-latency applications in NFV networks. IEEE Syst J 13(4):3877–3888
Sun G, Xu Z, Yu H et al (2020) Low-latency and resource-efficient service function chaining orchestration in network function virtualization. IEEE Internet Things J 7(7):5760–5772
Sun G, Xu Z, Yu H et al (2021) Dynamic network function provisioning to enable network in box for industrial applications. IEEE Trans Ind Inform 17(10):7155–7164
Teodoro A, Gomes O, Saadi M et al (2021) An FPGA-based performance evaluation of artificial neural network architecture algorithm for IoT. Wirel Pers Commun. https://doi.org/10.1007/s11277-021-08566-1
Tutueva AV, Nepomuceno EG, Karimov AI et al (2020) Adaptive chaotic maps and their application to pseudo-random numbers generation. Chaos Solitons Fractals 133:109615
Wang S, Sheng H, Yang D et al (2022) Extendable multiple nodes recurrent tracking framework with RTU++. IEEE Trans Image Process 31:5257–5271
Wang Y, Liu Z, Ma J et al (2016) A pseudorandom number generator based on piecewise logistic map. Nonlinear Dyn 83(4):2373–2391
Xie G, Hou G, Pei Q et al (2024) Lightweight privacy protection via adversarial sample. Electronics 13(7):1230
Xuemin Z, Haitao D, Zenggang X et al (2024) Self-organizing key security management algorithm in socially aware networking. J Signal Process Syst 96(6):369–383
Yang Y, Zhang Z, Zhou Y et al (2023) Design of a simultaneous information and power transfer system based on a modulating feature of magnetron. IEEE Trans Microw Theory Tech 71(2):907–915
Yin Y, Guo Y, Su Q et al (2022) Task allocation of multiple unmanned aerial vehicles based on deep transfer reinforcement learning. Drones 6(8):215
Yu F, Liu L, Shen H, Zhang Z, Huang Y, Shi C, Cai S, Wu X, Du S, Wan Q, Guo L (2020) Dynamic Analysis, Circuit Design, and Synchronization of a Novel 6D Memristive Four-Wing Hyperchaotic System with Multiple Coexisting Attractors. Complex. 2020. https://doi.org/10.1155/2020/5904607
Zhang M, Zhang Y, Cen Q et al (2022) Deep learning-based resource allocation for secure transmission in a non-orthogonal multiple access network. Int J Distrib Sens Netw 18(6):15501329221104330
Zhang R et al (2024) Differential Feature Awareness Network Within Antagonistic Learning for Infrared-Visible Object Detection. In: IEEE Transactions on Circuits and Systems for Video Technology 34(8):6735–6748. https://doi.org/10.1109/TCSVT.2023.3289142
Zhang X, Wang J, Xu J et al (2023) Detection of android malware based on deep forest and feature enhancement. IEEE Access 11:29344–29359
Zhao Y, Gao C, Liu J (2019) A self-perturbed pseudorandom sequence generator based on hyperchaos. Chaos Solitons Fractals 4:100023
Zheng W, Gong G, Tian J (2023) Design of a modified transformer architecture based on relative position coding. Int J Comput Intell Syst 16:168
Zhou P, Peng R, Xu M et al (2021) Path planning with automatic seam extraction over point cloud models for robotic arc welding. IEEE Robot Autom Lett 6(3):5002–5009
Zhuang Z, Tao H, Chen Y et al (2023) An optimal iterative learning control approach for linear systems with nonuniform trial lengths under input constraints. IEEE Trans Syst Man Cybern Syst 53:3461–3473
Acknowledgements
This work was supported by DBT STAR College scheme of Ramakrishna Mission Vidyamandira.
Funding
No funding received.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
No interests of a financial or personal nature.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sarkar, A., Singh, M.M. & Sharma, H.S. Artificial recurrent neural network coordinated secured transmission towards safeguarding confidentiality in smart Industrial Internet of Things. Int. J. Mach. Learn. & Cyber. 16, 891–917 (2025). https://doi.org/10.1007/s13042-024-02310-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13042-024-02310-4