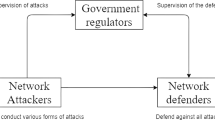
Abstract
In cyber security, balancing investment and risk has always been a dilemmatic problem since the threats often lurk in the shadows. Thus, timely and scientifically credible decision-making will have great significance in such an attack-defense game of incomplete information. To this end, an evolutionary game model of group decision-making is proposed to analyze the behavioral change process of the defender population. In particular, we first introduce the concept of observation error and short-term prediction in network communication and establish an improved selection–drift dynamics in which errors are automatically corrected to a certain extent and the convergence speed is faster than the prototype. By calculating the stable evolutionary equilibrium of the defender population, the optimal group decision-making approach is formulated. Case studies on big data vulnerabilities indicate that the proposed model and approach perform better in robustness and computational efficiency than the 3 typical models under jamming environments.






Similar content being viewed by others
Data Availability
The datasets generated during and/or analyzed during the current study are available in the National Vulnerability Database repository, https://nvd.nist.gov/vuln/search; AND. The datasets generated during and/or analyzed during the current study are available in the Common Weakness Enumeration (CWE) repository, http://cwe.mitre.org/index.html; AND. The datasets generated during and/or analyzed during the current study are available in the Common Attack Pattern Enumeration and Classification (CAPEC) repository, http://capec.mitre.org/; AND. The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request; AND all data generated or analyzed during this study are included in this published article (and its supplementary information files).
References
Akkarajitsakul K, Hossain E, Niyato D, Kim DI (2011) Game theoretic approaches for multiple access in wireless networks: a survey. IEEE Commun Surveys Tutorials 13(3):372–395. https://doi.org/10.1109/SURV.2011.122310.000119
Alpcan T, Başar T (2010) Network security: A decision and game-theoretic approach. Cambridge University Press. London, pp 3–13.
Alshamrani A, Myneni S, Chowdhary A, Dijiang H (2019) A survey on advanced persistent threats: Techniques, solutions, challenges, and research opportunities. IEEE Commun Surveys Tutorials 21(2):1851–1877. https://doi.org/10.1109/COMST.2019.2891891
Attiah A, Chatterjee M, Zou CC (2018) A game theoretic approach to model cyber attack and defense strategies. In: 2018 IEEE International Conference on Communications (ICC). pp 1–7. doi: https://doi.org/10.1109/ICC.2018.8422719
Boudko S, Aursand P, Abie H (2020) Evolutionary game for confidentiality in IoT-enabled smart grids. Information 11(12):582. https://doi.org/10.3390/info11120582
Chattopadhyay D (2004) A game theoretic model for strategic maintenance and dispatch decisions. IEEE Trans Power Syst 19(4):2014–2021. https://doi.org/10.1109/TPWRS.2004.836180
Do CT, Tran NH, Hong C, Kamhoua CA, Kwiat KA, Blasch E, Shaolei R, Pissinou N, Iyengar SS (2018) Game theory for cyber security and privacy. ACM Comput Surveys (CSUR) 50(2):1–37. https://doi.org/10.1145/3057268
Du J, Jiang C, Chen KC, Ren Y, Poor HV (2017) Community-structured evolutionary game for privacy protection in social networks. IEEE Trans Inf Forensics Secur 13(3):574–589. https://doi.org/10.1109/TIFS.2017.2758756
Galov N, (2022) "53 Cybersecurity Statistics from 2021: Stay Safe in the New Decade." Feb.18, 2022. Accessed: Feb.28, 2022. [Online]. Available: https://hostingtribunal.com/blog/cybersecurity-statistics/
Gordon LA, Loeb MP, Lucyshyn W, Richardson R (2005) CSI/FBI computer crime and security survey. Comput Secur J 21(3):1
Hu H, Liu Y, Chen C, Zhang H, Liu Y (2020) Optimal decision making approach for cyber security defense using evolutionary game. IEEE Trans Netw Serv Manage 17(3):1683–1700. https://doi.org/10.1109/TNSM.2020.2995713
Hu H, Liu Y, Zhang H, Pan R (2018) Optimal network defense strategy selection based on incomplete information evolutionary game. IEEE Access 6:29806–29821. https://doi.org/10.1109/ACCESS.2018.2841885
Hubbard DW, Seiersen R, (2016) How to measure anything in cybersecurity risk. John Wiley & Sons. pp 4–10.
Kamhoua CA, Pissinou N, Makki K (2011) Game theoretic modeling and evolution of trust in autonomous multi-hop networks: application to network security and privacy. In: 2011 IEEE International Conference on Communications (ICC). pp 1–6. doi: https://doi.org/10.1109/icc.2011.5962511
Komarova NL, Niyogi P, Nowak MA (2001) The evolutionary dynamics of grammar acquisition. J Theor Biol 209(1):43–59. https://doi.org/10.1006/jtbi.2000.2240
Leonard NE (2014) Multi-agent system dynamics: Bifurcation and behavior of animal groups. Annu Rev Control 38(2):171–183. https://doi.org/10.1016/j.arcontrol.2014.09.002
Li B, Chen Y, Huang S, Yao R, Xia Y, Mei S (2019) Graphical evolutionary game model of virus-based intrusion to power system for long-term cyber-security risk evaluation. IEEE Access 7:178605–178617. https://doi.org/10.1109/ACCESS.2019.2958856
Li Y, Deng Y, Xiao Y, Wu J (2019) Attack and defense strategies in complex networks based on game theory. J Syst Sci Complexity 32(6):1630–1640. https://doi.org/10.1007/s11424-019-7420-0
Manshaei MH, Zhu Q, Alpcan T, Başar T, Hubaux JP (2013) Game theory meets network security and privacy. ACM Comput Surveys (CSUR) 45(3):1–39. https://doi.org/10.1145/2480741.2480742
Massaquoi SG (1999) Modeling the function of the cerebellum in scheduled linear servo control of simple horizontal planar arm movements. Massachusetts Institute of Technology. uri: http://hdl.handle.net/1721.1/9083
Olfati SR (2007) Evolutionary dynamics of behavior in social networks. In: 2007 46th IEEE conference on decision and control. pp 4051–4056. doi: https://doi.org/10.1109/CDC.2007.4435009
Perc M, Szolnoki A (2010) Coevolutionary games—a mini review. BioSystems 99(2):109–125. https://doi.org/10.1016/j.biosystems.2009.10.003
Roy S, Ellis C, Shiva S, Dasgupta D, Shandilya V, Wu Q, (2010) A survey of game theory as applied to network security. In: 2010 43rd Hawaii International Conference on System Sciences. pp 1–10. https://doi.org/10.1109/HICSS.2010.35
Ruan N, Gao L, Zhu H, Jia W, Li X, Hu Q, (2016) Toward optimal dos-resistant authentication in crowdsensing networks via evolutionary game. In: 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS). pp 364–373. doi: https://doi.org/10.1109/ICDCS.2016.66
Sandholm WH (2020) Evolutionary game theory. Complex Social Behavioral Systems: Game Theory Agent-Based Models. https://doi.org/10.1007/978-1-0716-0368-0_188
Selten R (1980) A note on evolutionarily stable strategies in asymmetric animal conflicts. J Theoretical Biol 84(1):93–101. https://doi.org/10.1016/S0022-5193(80)81038-1
Shadmehr R (2017) Distinct neural circuits for control of movement vs. holding still. J Neurophys 117(4):1431–1460. https://doi.org/10.1152/jn.00840.2016
Tan S, Wang Y, Chen Y, Wang Z (2016) Evolutionary dynamics of collective behavior selection and drift: flocking, collapse, and oscillation. IEEE Trans Cyber 47(7):1694–1705. https://doi.org/10.1109/TCYB.2016.2555316
Tan, S., Wang, Y., Vasilakos, A.V., 2021. Distributed population dynamics for searching generalized nash equilibria of population games with graphical strategy interactions. IEEE Transactions on Systems, Man, and Cybernetics: Systems (Early Access). doi: https://doi.org/10.1109/TSMC.2021.3062827
Tanimoto J (2015) Fundamentals of evolutionary game theory and its applications. Springer, Japan, pp 69–90
Tenable®. (2022) "Nessus Vulnerability Scanner." Accessed Feb.22, 2022. [Online]. Available: https://www.tenable.com/downloads/nessus
Tian Z, Gao X, Su S, Qiu J, Du X, Guizani M (2019) Evaluating reputation management schemes of internet of vehicles based on evolutionary game theory. IEEE Trans Veh Technol 68(6):5971–5980. https://doi.org/10.1109/TVT.2019.2910217
Tosh D, Sengupta S, Kamhoua CA, Kwiat KA (2018) Establishing evolutionary game models for CYBer security information exchange (CYBEX). J Comput Syst Sci 98:27–52. https://doi.org/10.1016/j.jcss.2016.08.005
United States Department of Commerce, (2022) "National vulnerability database." https://nvd.nist.gov/vuln/search (accessed Feb.22, 2022)
United States Department of Homeland Security (DHS), (2022) "Common attack pattern enumeration and classification (CAPEC)." http://capec.mitre.org/ (accessed Feb.22, 2022)
United States Department of Homeland Security (DHS), (2022) "Common weakness enumeration (CWE)." http://cwe.mitre.org/index.html (accessed Feb.22, 2022)
Wang Y, Nakao A, Vasilakos AV, Ma J (2011) P2P soft security: On evolutionary dynamics of P2P incentive mechanism. Comput Commun 34(3):241–249. https://doi.org/10.1016/j.comcom.2010.01.021
Wang Z, Wang L, Szolnoki A, Perc M (2015) Evolutionary games on multilayer networks: a colloquium. Eur Phys J B 88(5):1–15. https://doi.org/10.1140/epjb/e2015-60270-7
Xu X, Chen Z, Si G, Hu X, Jiang Y, Xu X (2011) The chaotic dynamics of the social behavior selection networks in crowd simulation. Nonlinear Dyn 64(1):117–126. https://doi.org/10.1007/s11071-010-9850-z
Yang Y, Che B, Zeng Y, Cheng Y, Li C (2019) MAIAD: a multistage asymmetric information attack and defense model based on evolutionary game theory. Symmetry 11(2):215. https://doi.org/10.3390/sym11020215
Yang P, Gao F, Zhang H (2021) Multi-player evolutionary game of network attack and defense based on system dynamics. Mathematics 9(23):3014. https://doi.org/10.3390/math9233014
Acknowledgement
National Natural Science Foundation of China, Grant Number 61902426
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
We declare that we have no financial and personal relationships with other people or organizations that can inappropriately influence our work, there is no professional or other personal interest of any nature or kind in any product, service and/or company that could be construed as influencing the position presented in, or the review of, the manuscript entitled, “An Optimal Group Decision-Making Approach for Cyber Security Using Improved Selection-Drift Dynamics.”
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, E., Wang, G., Ma, R. et al. An Optimal Group Decision-Making Approach for Cyber Security Using Improved Selection-Drift Dynamics. Dyn Games Appl 13, 980–1004 (2023). https://doi.org/10.1007/s13235-022-00476-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13235-022-00476-6