Abstract
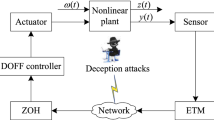
This paper addresses the problem of guaranteed cost output feedback control for a class of networked interval type-2 Takagi–Sugeno (IT2 T-S) fuzzy systems with adaptive event-triggered stochastic communication protocol (AETSCP) scheduling and hybrid attacks. A novel AETSCP scheduling is designed to judge whether or not data are triggered as well as to determine which node transmits data to the controller. Meanwhile, the security problem of hybrid attacks with respect to denial-of-service (DoS) attacks and deception attacks on the system is considered. The quadratic boundedness (QB) technique is employed to depict the closed-loop stability of the concerned networked control systems (NCSs). Two adequate theorems are given based on Lyapunov stability theory for designing the observer-based and dynamic output feedback-based controllers, which guarantee the stability and robust performance of the required system. In the end, a simulation example of the mass-spring-damping system is provided to confirm the effectiveness of the presented control strategy.








Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Hespanha, J.P., Naghshtabrizi, P., Xu, Y.: A survey of recent results in networked control systems. Proc. IEEE. 95(1), 138–162 (2007)
Peng, C., Ma, S., Xie, X.: Observer-based non-PDC control for networked T-S fuzzy systems with an event-triggered communication. IEEE Trans. Cybern. 47(8), 2279–2287 (2017)
Zhang, K., Gharesifard, B., Braverman, E.: Event-triggered control for nonlinear time-delay systems. IEEE Trans. Autom. Control 67(2), 1031–1037 (2021)
Zhu, L., Chen, Z., Hill, D.J., Du, S.: Event-triggered controllers based on the supremum norm of sampling-induced error. Automatica 128, 109532 (2021)
Senthilkumar, K., Roy, A.K., Srinivasan, K.: Event triggered estimator based controller design for networked control system. ISA Trans. 126, 80–93 (2022)
Lin, N., Ling, Q.: Bit-rate conditions for the consensus of quantized multiagent systems based on event triggering. IEEE Trans. Cybern. 52(1), 116–127 (2020)
Wang, W., Wen, C., Huang, J., Zhou, J.: Adaptive consensus of uncertain nonlinear systems with event triggered communication and intermittent actuator faults. Automatica 111, 108667 (2020)
Tang, X., Deng, L.: Multi-step output feedback predictive control for uncertain discrete-time T-S fuzzy system via event-triggered scheme. Automatica 107, 362–370 (2019)
Xing, M., Deng, F.: Tracking control for stochastic multi-agent systems based on hybrid event-triggered mechanism. Asian J. Control 21(5), 2352–2363 (2019)
Fei, Z., Guan, C., Gao, H.: Exponential synchronization of networked chaotic delayed neural network by a hybrid event trigger scheme. IEEE Trans. Neural Netw. Learn. Syst. 29(6), 2558–2567 (2017)
Behera, A.K., Bandyopadhyay, B., Yu, X.: Periodic event-triggered sliding mode control. Automatica 96, 61–72 (2018)
Li, F., Liu, Y.: Adaptive event-triggered output-feedback controller for uncertain nonlinear systems. Automatica 117, 109006 (2020)
Chen, Z., Niu, B., Zhao, X., Zhang, L., Xu, N.: Model-based adaptive event-triggered control of nonlinear continuous-time systems. Appl. Math. Comput. 408, 126330 (2021)
Tang, X., Li, Y., Yang, M., Wu, Y., Wen, Y.: Adaptive event-triggered model predictive load frequency control for power systems. IEEE Trans. Power Syst. 38(5), 4003–4014 (2023)
Wang, P.B., Ren, X.M., Zheng, D.D.: Robust nonlinear MPC with variable prediction horizon: an adaptive event-triggered approach. IEEE Trans. Autom. Control (2022). https://doi.org/10.1109/tac.2022.3200967
Tang, X., Su, X., Zhao, K., Qu, H., Cai, L.: Decay aggregation efficient output feedback MPC for networked interval type-2 T-S fuzzy systems with AET mechanism and deception attack. IEEE Trans. Fuzzy Syst. 3358352 (2024). https://doi.org/10.1109/tfuzz.2024.3358352.
Li, X., Sun, Z., Tang, Y., Karimi, H.R.: Adaptive event-triggered consensus of multiagent systems on directed graphs. IEEE Trans. Autom. Control 66(4), 1670–1685 (2020)
Mamduhi, M.H., Hirche, S.: Try-once-discard scheduling for stochastic networked control systems. Int. J. Control 92(11), 2532–2546 (2019)
Wang, J., Song, Y., Wei, G.: Dynamic output-feedback RMPC for systems with polytopic uncertainties under Round-Robin protocol. J. Franklin Inst. 356(4), 2421–2439 (2019)
Cheng, J., Park, J.H., Yan, H., Wu, Z.-G.: An event-triggered round-robin protocol to dynamic output feedback control for nonhomogeneous Markov switching systems. Automatica 145, 110525 (2020)
Song, J., Wang, Z., Niu, Y.: On H-infinity sliding mode control under stochastic communication protocol. IEEE Trans. Autom. Control 64(5), 2174–2181 (2019)
Zhang, Z., Niu, Y., Cao, Z., Song, J.: Security sliding mode control of interval type-2 fuzzy systems subject to cyber attacks: the stochastic communication protocol case. IEEE Trans. Fuzzy Syst. 29(2), 240–251 (2020)
Wan, X., Wang, Z., Han, Q.-L., Wu, M.: A recursive approach to quantized \(H_\infty\) state estimation for genetic regulatory networks under stochastic communication protocols. IEEE Trans. Neural Netw. Learn. Syst. 30(9), 2840–2852 (2019)
Ding, D., Wang, Z., Han, Q.L.: Neural-network-based output-feedback control with stochastic communication protocols. Automatica 106, 221–229 (2019)
Cao, Z., Niu, Y., Karimi, H.R.: Dynamic output feedback sliding mode control for Markovian jump systems under stochastic communication protocol and its application. Int. J. Robust Nonlinear Control 30(17), 7307–7325 (2020)
Sun, L., Zhang, Y., Sun, C.: Stochastic denial-of-service attack allocation in leader-following multiagent systems. IEEE Trans. Syst. Man Cybern. Syst. 52(5), 2848–2857 (2021)
Hu, Z., Deng, F., Su, Y., Zhang, J., Hu, S.: Security control of networked systems with deception attacks and packet dropouts: a discrete-time approach. J. Franklin Inst. 358(16), 8193–8206 (2021)
Lu, A.Y., Yang, G.H.: Stability analysis for cyber-physical systems under denial-of-service attacks. IEEE Trans. Cybern. 51(11), 5304–5313 (2020)
Liu, J., Yin, T., Shen, M., Xie, X., Cao, J.: State estimation for cyber-physical systems with limited communication resources, sensor saturation and denial-of-service attacks. ISA Trans. 104, 101–114 (2020)
Du, D., Zhang, C., Wang, H., Li, X., Hu, H., Yang, T.: Stability analysis of token-based wireless networked control systems under deception attacks. Inform. Sci 459, 168–182 (2018)
Zhao, L., Yang, G.H.: Cooperative adaptive fault-tolerant control for multi-agent systems with deception attacks. J. Franklin Inst. 357(6), 3419–3433 (2020)
Li, Z., Zhao, J.: Resilient adaptive control of switched nonlinear cyber-physical systems under uncertain deception attacks. Inform. Sci. 543, 398–409 (2021)
Liu, J., Zhang, N., Li, Y., Xie, X.: H\(\infty\) filter design for discrete-time networked systems with adaptive event-triggered mechanism and hybrid cyber attacks. J. Franklin Inst. 358(17), 9325–9345 (2021)
Xi, Z., Feng, G., Hesketh, T.: Piecewise sliding-mode control for T-S fuzzy systems. IEEE Trans. Fuzzy Syst. 19(4), 707–716 (2011)
Li, Y., Liu, L., Feng, G.: Finite-time stabilization of a class of T-S fuzzy systems. IEEE Trans. Fuzzy Syst. 25(6), 1824–1829 (2016)
Su, X., Zhou, H., Song, Y.-D.: An optimal divisioning technique to stabilization synthesis of T-S fuzzy delayed systems. IEEE Trans. Cybern. 47(5), 1147–1156 (2016)
Wang, Y., Hua, C., Park, P.: A generalized reciprocally convex inequality on stability and stabilization for T-S fuzzy systems with time-varying delay. IEEE Trans. Fuzzy Syst. 31(3), 722–733 (2022)
Visakamoorthi, B., Muthukumar, P., Trinh, H.: Reachable set estimation for T-S fuzzy markov jump systems with time-varying delays via membership function dependent performance. IEEE Trans. Fuzzy Syst. 30(11), 4980–4990 (2022)
Zhang, Z., Niu, Y., Lam, H.-K.: Sliding-mode control of T-S fuzzy systems under weighted try-once-discard protocol. IEEE Trans. Cybern. 50(12), 4972–4982 (2019)
Tang, X., Deng, L., Liu, N., Yang, S., Yu, J.: Observer-based output feedback MPC for T-S fuzzy system with data loss and bounded disturbance. IEEE Trans. Cybern. 49(6), 2119–2132 (2018)
Liu, Y., Guo, B.. -Z., Park, J.. H., Lee, S.: Event-based reliable dissipative filtering for T-S fuzzy systems with asynchronous constraints. IEEE Trans. Fuzzy Syst. 26(4), 2089–2098 (2017)
Guo, X.-G., Fan, X., Ahn, C.K.: Adaptive event-triggered fault detection for interval type-2 T-S fuzzy systems with sensor saturation. IEEE Trans. Fuzzy Syst. 29(8), 2310–2321 (2020)
Tang, X., Deng, L., Qu, H.: Predictive control for networked interval type-2 T-S fuzzy system via an event-triggered dynamic output feedback scheme. IEEE Trans. Fuzzy Syst. 27(8), 1573–1586 (2018)
Alessandri, A., Baglietto, M., Battistelli, G.: On estimation error bounds for receding-horizon filters using quadratic boundedness. IEEE Trans. Autom. Control 49(8), 1350–1355 (2004)
Ghaoui, L.E., Oustry, F., AitRami, M.: A cone complementarity linearization algorithm for static output-feedback and related problems. IEEE Trans. Autom. Control 42(8), 1171–1176 (1997)
Castelan, E.B., Tarbouriech, S., Queinnec, I.: Control design for a class of nonlinear continuous-time systems. Automatica 44(8), 2034–2039 (2008)
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China under Grant 62073053 and Grant 61871061; in part by the Research Project of Chongqing Science and Technology Commission under Grant cstc2021jcyjmsxmX0315; in part by the Project of Advanced Scientific Research Institute of CQUPT under Grant E011A2022329; and in part by the science and technology planning project of Chongqing market supervision and Administration Bureau under Grant CQSJKJDW2023028, and in part by the National Administration for Market Regulation Science and Technology Program Project under Grant 2023MK104.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A
Proof
Consider the performance index function \(J_h^1={\mathcal {E}}\{ \sum _{h=0}^{\infty }(\Vert {\tilde{x}}_{h_t} \Vert _{{\mathscr {Q}}}^2+\Vert u_h \Vert _{{\mathscr {R}}}^2 ) \}\), where \({\mathscr {Q}}\) and \({\mathscr {R}}\) are positive-definite matrices of appropriate dimensions. For the closed-loop system (17), we construct the Lyapunov function \(V(\aleph _h^1)=\Vert \aleph _h^1 \Vert _{\digamma _1}^2+\epsilon _h\), where \(\digamma _1=\textrm{diag}\{ P_1,\varrho N_e,S_1,M_1 \}\). If NCS (17) is quadratically stable, then \({\mathcal {E}}\{V(\aleph _h^1)\}\ge 1 \Longrightarrow {\mathcal {E}}\{ V(\aleph _h^1) \}-{\mathcal {E}}\{ V(\aleph _{h+1}^1 \}\ge \frac{1}{\gamma }{\mathcal {E}}\{ \Vert {\tilde{x}}_{h_t} \Vert _{{\mathscr {Q}}}^2+\Vert u_h \Vert _{{\mathscr {R}}}^2 \}\) holds, where \(\gamma\) is the upper bound of \(J_h^1\). Since \(\Vert \xi _h \Vert _H^2\le 1\), by the S-procedure method, there exists a scalar \(\phi _1\in (0,1)\), which makes
Besides, by (3) and (4), it is possible to obtain the inequality
Substituting (17) into (29), and combining (30), a new matrix inequality can be acquired by using the Schur complement. And then, since there is a non-convex optimization problem in this new matrix inequality, it can be handled by the cone complement linearization algorithm in Lemma 1, i.e., by making \(P^{-1}={\bar{P}}\), \(S^{-1}={\bar{S}}\), \(M^{-1}={\bar{M}}\), \(\Psi ^{-1}={\bar{\Psi }}\), such that \(P{\bar{P}}=I\), \(S{\bar{S}}=I\), \(M{\bar{M}}=I\), \(\Psi {\bar{\Psi }}=I\). Next, using a congruence transformation on the matrix inequality via \(\textrm{diag}\{ I,I,I,I,I,I,I,I,I,I,I,\varrho I,I,I,I,I,I,I,I,I,I,I,I \}\), (19) can be proved. Finally, we give the upper bound \(\gamma\) of \(J_h^1\) such that \(\gamma {\mathcal {E}}\{V(\aleph _0^1)\}\le \gamma\). Again using the Schur complement, (20) is confirmed. \(\square\)
Appendix B
Proof
Similarly, consider the performance index function \(J_h^2={\mathcal {E}}\{ \sum _{h=0}^{\infty }(\Vert {\tilde{y}}_{h_t} \Vert _{{\mathscr {Q}}}^2+\Vert u_h \Vert _{{\mathscr {R}}}^2 ) \}\). For the closed-loop system (23), we construct the Lyapunov function \(V(\aleph _h^2)=\Vert \aleph _h^2 \Vert _{\digamma _2}^2+\epsilon _h\), where \(\digamma _2=\textrm{diag}\{ P_2,S_2,M_2 \}\). If NCS (23) is quadratically stable, then there exists a scalar \(\phi _2\in (0,1)\) satisfying the following condition:
In addition, \(\Delta \epsilon _h \le \Vert y_h+{\bar{e}}_h \Vert _{\Psi }^2-{\tilde{\epsilon }}_h\Vert {\bar{e}}_h \Vert _{\Psi }^2\). By applying the Schur complement, the new matrix inequality is obtained. Define
with \(X=-W\). Make \({\mathcal {T}}_1=\begin{bmatrix} I &{} Y \\ 0 &{} K \end{bmatrix}\) and \({\mathcal {T}}_2=\begin{bmatrix} I &{} W \\ 0 &{} X \end{bmatrix}\). By pre- and post-multiplying \(\textrm{diag}\{{\mathcal {T}}_1^\textrm{T},I,I,I,I,I,{\mathcal {T}}_2^\textrm{T},I,I,I,I,I,I,I,I,I,I,I,I,I,I\}\) and its transpose for both the left and right sides of the matrix inequality, (25) is deduced. The rest of the proof procedure is similar to Appendix A. \(\square\)
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Su, X., Tang, X., Lv, X. et al. Guaranteed Cost Output Feedback Control for Nonlinear Systems via Networks with Adaptive Event-Triggered SCP and Hybrid Attacks. Int. J. Fuzzy Syst. 26, 2323–2336 (2024). https://doi.org/10.1007/s40815-024-01737-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40815-024-01737-9