Abstract
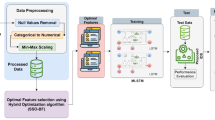
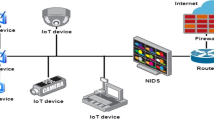
Internet of Things (IoT) has got more attention in the research field of computer science. The extreme increase in the IoT appliances across various factors, such as smart industries and health care appears with extensive security hazards. It is not only restricted to the attacks on confidentiality but also broadens to the attacks on performance and availability of the network. Hence, an intrusion detection mechanism is mandatory for identifying the attacks on IoT to offer effectual protection and security. Even though various intrusion detection methods are developed, achieving higher classification performance still results a challenging task. Therefore, an effective intrusion detection method is developed using the proposed Competitive Swarm Henry Optimization (CSHO)-based Deep Maxout network to find intruders in the IoT environment. The process of detection strategy is carried out with the information captured by nodes distributed in network. Routing plays an essential role in transferring data from IoT devices to the base station (BS) to accomplish the task of intrusion discovery. The proposed solution offers security as a service and provides evidence in terms of scalability. However, the proposed method offers better results using the metrics, like energy, F-measure, precision, and recall as 0.1610, 0.9001, 0.9052, and 0.8993, respectively.









Similar content being viewed by others
References
Al-Hadhrami, Y., Hussain, F.K.: Real time dataset generation framework for intrusion detection systems in IoT. Futur. Gener. Comput. Syst. 108, 414–423 (2020)
Anand, S., intrusion detection system for wireless mesh networks via improved whale optimization, J. Netw. Commun. Syst., vol.3, no.4, 2020.
Anthi, E., Williams, L., Słowińska, M., Theodorakopoulos, G., Burnap, P.: A supervised intrusion detection system for smart home IoT devices. IEEE Internet Things J. 6(5), 9042–9053 (2019)
BoT-IoT dataset https://ieee-dataport.org/documents/bot-iot-dataset. Accessed on Apr 2021.
Cesare, S. and Xiang, Y., “Software birthmark similarity”, In Software Similarity and Classification, Springer, London, pp. 63–70, 2012.
Chaabouni, N., Mosbah, M., Zemmari, A., Sauvignac, C., Faruki, P.: Network intrusion detection for IoT security based on learning techniques. IEEE Communications Surveys & Tutorials 21(3), 2671–2701 (2019)
Cheng, R., Jin, Y.: A competitive swarm optimizer for large scale optimization. IEEE Transactions on Cybernetics 45(2), 191–204 (2014)
Dhumane, A.V., Prasad, R.S.: Fractional gravitational Grey Wolf optimization to multi-path data transmission in IoT. Wireless Pers. Commun. 102(1), 411–436 (2018)
Dineva, K., and Atanasova, T., Machine learning solution for IoT big data, In the proceeding of International Multidisciplinary Scientific GeoConference SGEM 2020, vol. 20, no.2, pp. 207–214, 2020.
Dineva, K., and Atanasova, T., Design of Scalable IoT Architecture Based on AWS for Smart Livestock, Multidisciplinary Digital Publishing Institute, vol. 11, no. 9, 2021.
Eskandari, M., Janjua, Z.H., Vecchio, M., Antonelli, F.: Passban IDS: an intelligent anomaly-based intrusion detection system for IoT edge devices. IEEE Internet Things J. 7(8), 6882–6897 (2020)
Prasanalakshmi, B., and Kannammal, A., ECC Based Biometric Encryption of Compressed Image for Security over Network Channels, In the proceedings of the Fourth International Conference on Signal and Image Processing 2012 (ICSIP 2012), Springer, India, pp. 343–351, 2013.
Fu, Y., Yan, Z., Cao, J., Koné, O. and Cao, X., “An automata based intrusion detection method for internet of things”, Mobile Information Systems, 2017.
Ge, M., Fu, X., Syed, N., Baig, Z., Teo, G. and Robles-Kelly, A., “Deep learning-based intrusion detection for iot networks”, In IEEE 24th Pacific Rim International Symposium on Dependable Computing (PRDC) (pp. 256–25609, December 2019.
Hanif, S., Ilyas, T. and Zeeshan, M., “Intrusion detection in iot using artificial neural networks on unsw-15 dataset”, In IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), pp. 152–156, October 2019.
Hashim, F.A., Houssein, E.H., Mabrouk, M.S., Al-Atabany, W., Mirjalili, S.: Henry gas solubility optimization: a novel physics-based algorithm. Futur. Gener. Comput. Syst. 101, 646–667 (2019)
Jan, S.U., Ahmed, S., Shakhov, V., Koo, I.: Toward a lightweight intrusion detection system for the internet of things. IEEE Access 7, 42450–42471 (2019)
Kan, X., Fan, Y., Fang, Z., Cao, Le., Xiong, N.N., Yang, D., Li, X.: A novel IoT network intrusion detection approach based on adaptive particle swarm optimization convolutional neural network. Inf. Sci. 568, 147–162 (2021)
Khraisat, A., Gondal, I., Vamplew, P., Kamruzzaman, J., Alazab, A.: A novel ensemble of hybrid intrusion detection system for detecting internet of things attacks. Electronics 8(11), 1210 (2019)
Li, D., Deng, L., Lee, M., Wang, H.: IoT data feature extraction and intrusion detection system for smart cities based on deep migration learning. Int. J. Inf. Manage. 49, 533–545 (2019)
Lopez-Martin, M., Carro, B., Sanchez-Esguevillas, A., Lloret, J.: Conditional variational autoencoder for prediction and feature recovery applied to intrusion detection in iot. Sensors 17(9), 1967 (2017)
Moustafa, N., Turnbull, B., Choo, K.K.R.: An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of things. IEEE Internet Things J. 6(3), 4815–4830 (2018)
Raza, S., Wallgren, L., Voigt, T.: SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 11(8), 2661–2674 (2013)
Siddiqui, A.J., Boukerche, A.: TempoCode-IoT: temporal codebook-based encoding of flow features for intrusion detection in internet of things. Clust. Comput. 24(1), 17–35 (2021)
Smys, S., Basar, A., Wang, H.: Hybrid intrusion detection system for internet of Things (IoT). J. ISMAC 2(4), 190–199 (2020)
Sun, W., Su, F., Wang, L.: Improving deep neural networks with multi-layer maxout networks and a novel initialization method. Neurocomputing 278, 34–40 (2018)
Susilo, B., Sari, R.F.: Intrusion detection in IoT networks using deep learning algorithm. Information 11(5), 279 (2020)
Thamilarasu, G., Chawla, S.: Towards deep-learning-driven intrusion detection for the internet of things. Sensors 19(9), 1977 (2019)
Veeraiah, N., and Dr. Krishna, B.T. Intrusion detection based on piecewise fuzzy C-means clustering and fuzzy naïve bayes rule, vol. 1, no. 1, pp. 27–32, 2018b.
Neenavath Veeraiah and Dr.B.T.Krishna, "Intrusion Detection Based on Piecewise Fuzzy C-Means Clustering and Fuzzy Naive Bayes Rule", Multimedia Research, vol.1, no.1, pp.27–32, 2018a.
Verma, A., Ranga, V.: Machine learning based intrusion detection systems for IoT applications. Wireless Pers. Commun. 111(4), 2287–2310 (2020)
Yadav, A.K., Tripathi, S.: QMRPRNS: design of QoS multicast routing protocol using reliable node selection scheme for MANETs. Peer-to-Peer Networking and Applications 10(4), 897 (2017)
Yang, K., Ren, J., Zhu, Y., Zhang, W.: Active learning for wireless IoT intrusion detection. IEEE Wirel. Commun. 25(6), 19–25 (2018)
Zhang, Y., Li, P., Wang, X.: Intrusion detection for IoT based on improved genetic algorithm and deep belief network. IEEE Access 7, 31711–31722 (2019)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Boopathi, M. Henry MaxNet: tversky index based feature selection and competitive swarm henry gas solubility optimization integrated Deep Maxout network for intrusion detection in IoT. Int J Intell Robot Appl 6, 365–383 (2022). https://doi.org/10.1007/s41315-022-00234-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41315-022-00234-2