Abstract
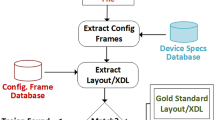
This paper reviews a developed integrated circuit (IC) decomposition workflow that can be leveraged for extracting design files and performing advanced verification and validation techniques on fabricated chips. In this work, a commercial 130-nm microcontroller is delayered and imaged to recreate the full design stack-up. Using MicroNet’s Pix2Net, the features for each layer are extracted allowing a GDSII file to be generated and design netlists for target components to be recovered. The full decomposition process is executed on both the read only memory (ROM) array and universal serial communications interface (USCI) of the microcontroller to recover the layout GDSII and circuit netlist. A single-precision floating point unit (FPU) test article is used to incorporate a spectrum of error types into the design layout, thus creating a set of test articles with obfuscated errors. Once the netlists for each of the modified designs are extracted, formal verification techniques are applied to each netlist, thus illuminating the errors originally inserted into the layout. The extracted netlists are then converted into register transfer level (RTL) representations and simulated with the original design verification testbench.











Similar content being viewed by others
References
Tehranipoor M, Koushanfar F (2013) A survey of hardware Trojan taxonomy and detection. IEEE Des Test 0740-0745:10–25
Solomon R, Sandborn P, Pecht M (2000) Electronic part life cycle concepts and obsolescence forecasting. IEEE Trans Compon Packag Technol 23:707–717
Kühne U, Beyer S, Bormann J, Barstow J (2010) Automated formal verification of processors based on architectural models. Paper presented at Formal Methods in Computer Aided Design, Lugano, Switzerland, 20-23 October 2010
Salmani H, Tehranipoor M, Karri R (2013) On design vulnerability analysis and trust benchmark development. Paper presented at the IEEE 31st International Conference on Computer Design (ICCD), Asheville, 6-8 October 2013
Shakya B, He T, Salmani H, Forte D, Bhunia S, Tehranipoor M (2017) Benchmarking of hardware Trojans and maliciously affected circuits. J Hardw Syst Sec 1:85–102
Chiu RL, Chen T, Chem S (2008) S/D LDD junction stain/delineation by electrochemical displacement with illumination. In: Proceedings from the 34th International Symposium for Testing and Failure (ISTFA), Portland, 2-6 November 2008
Principe E, Asadizanjani N, Forte D, Tehranipoor M, Chivas R, DiBattista M, Silverman S, Marsh M, Piche N, Mastovich J (2017) Steps toward automated deprocessing of integrated circuits. In: Proceedings from the 43rd International Symposium for Testing and Failure Analysis (ISTFA), Pasadena, 5-9 November 2017
Kimura A, Liu K, Prabhu S, Bibyk S, Creech G (2013) Trusted verification test bench development for phase-locked loop (PLL) hardware insertion. Paper presented at IEEE 56th Midwest Symposium on Circuits and Systems (MWSCAS), Columbus, 4-7 August 2013
Kimura A (2017) Development of trust metrics for quantifying design integrity and error implementation cost. Electronic Thesis or Dissertation. The Ohio State University, May 2017. https://etd.ohiolink.edu/
Funding
The work presented in this paper was sponsored by the Air Force Research Laboratory in Dayton, OH. Approved for public release (approval ID: 88ABW-2019-1048).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kimura, A., Scholl, J., Schaffranek, J. et al. A Decomposition Workflow for Integrated Circuit Verification and Validation. J Hardw Syst Secur 4, 34–43 (2020). https://doi.org/10.1007/s41635-019-00086-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41635-019-00086-6