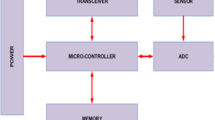
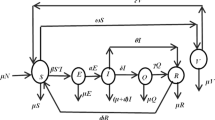
Abstract
Epidemic spreading in wireless sensor networks (WSNs) has lately attracted the attention of many researchers as a hot problem in nonlinear systems. Using wireless connectivity, the sensor nodes that makeup WSNs are linked to one another in a decentralized and distributed structure. Decentralized architectures and resource limitations pose a security risk for WSNs. Malware attacks the WSN’s sensor nodes, paralyzing them while collecting data from the network. Attacks by malware can increase the energy use of WSN sensor nodes. It just began spreading from one infected node and uses nearby nodes to expand over the whole WSN. Therefore, the protection of WSNs against malware attacks is a need that cannot be avoided. In this research paper, we propose an epidemic model to discuss the impact of charging on sensor nodes, coverage, and connectivity, considering prior research. The suggested model examines the dynamics of malware spread in WSNs and also explains how much energy is used by the sensor node. The stability of the system has been examined in terms of endemic and local equilibriums for malware propagation. The fundamental reproduction number expression, which is used to assess the prevalence of malware in WSN, has been calculated for the analysis of system dynamics. This study explains the implications of communication radius, sensor node charging, node density, and deployment area on malware dissemination. In comparison to previous models, the suggested approach offers a superior method to stop the propagation of malware in WSN. At the end, we show the results of a numerical simulation of how malware spreads, which proves that our theoretical approach is correct.


























Similar content being viewed by others
References
Mishra BK, Keshri N. Mathematical model on the transmission of worms in wireless sensor network. Appl Math Model. 2013;37(6):4103–11.
Andrews LJB, Raja L, Shanmugasundaram S. Mobile android-based remote patient monitoring system through wearable sensors. J Discrete Math Sci Cryptography. 2019;22(4):557–68.
Rawat GS, Singh K. Joint beacon frequency and beacon transmission power adaptation for internet of vehicles. Trans Emerging Telecommun Technol. 2022;33(10):4124.
Khan T, Singh K. Tasrp: a trust aware secure routing protocol for wireless sensor networks. Int J Innovative Comput Appl. 2021;12(2–3):108–22.
Abbas AM. Analysis of error for anchor-based localization in wireless sensor networks. J Interdisciplinary Math. 2020;23(2):393–401.
Arivudainambi D, Pavithra R, Kalyani P. Cuckoo search algorithm for target coverage and sensor scheduling with adjustable sensing range in wireless sensor network. J Discrete Math Sci Cryptography. 2021;24(4):975–96.
Tang C-L, Li M. Location of wireless sensor networks based on port management system. J Discrete Math Sci Cryptography. 2018;21(2):595–9.
Manju Bhambu P, Kumar S. Target k-coverage problem in wireless sensor networks. J Discrete Math Sci Cryptography. 2020;23(2):651–9.
Gambhir A, Payal A, Arya R. Water cycle algorithm based optimized clustering protocol for wireless sensor network. J Interdisciplinary Math. 2020;23(2):367–77.
Sandywell B. Monsters in cyberspace cyberphobia and cultural panic in the information age. Inform Commun Soc. 2006;9(1):39–61.
Jr GL. Not teaching viruses and worms is harmful. Communications of the ACM. 2005;48(1):144.
Venkatraman S. Autonomic framework for it security governance. Int J Manag Inform Technol. 2017;9(3):1–11.
Liang G, Weller SR, Zhao J, Luo F, Dong ZY. A framework for cyber-topology attacks: Line-switching and new attack scenarios. IEEE Trans Smart Grid. 2017;10(2):1704–12.
Upadhyay RK, Kumari S, Misra A. Modeling the virus dynamics in computer network with sveir model and nonlinear incident rate. J Appl Math Comput. 2017;54:485–509.
Ojha RP, Srivastava PK, Sanyal G. Improving wireless sensor networks performance through epidemic model. Int J Electron. 2019;106(6):862–79.
Tang S. A modified si epidemic model for combating virus spread in wireless sensor networks. Int J Wirel Inform Netw. 2011;18:319–26.
Wang X, Li Q, Li Y. Eisirs: a formal model to analyze the dynamics of worm propagation in wireless sensor networks. J Combinatorial Opt. 2010;20(1):47–62.
Keshri N, Mishra BK. Two time-delay dynamic model on the transmission of malicious signals in wireless sensor network. Chaos Solitons Fractals. 2014;68:151–8.
Mo L, You P, Cao X, Song Y.-Q, Chen J. Decentralized multi-charger coordination for wireless rechargeable sensor networks. In: 2015 IEEE 34th International Performance Computing and Communications Conference (IPCCC), pp. 1–8 (2015). IEEE
Liu G, Peng B, Zhong X, Lan X. Differential games of rechargeable wireless sensor networks against malicious programs based on silrd propagation model. Complexity. 2020;2020:
Diekmann O, Heesterbeek JAP, Metz JA. On the definition and the computation of the basic reproduction ratio r 0 in models for infectious diseases in heterogeneous populations. J Math Biol. 1990;28:365–82.
La Salle JP. The Stability of Dynamical Systems. SIAM, ??? (1976)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The manuscript has been approved by all authors and has never been published, or under consideration for publication elsewhere. We have not submitted our manuscript to a preprint server prior to submission on SN Computer Science.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Advanced Computing and Data Sciences” guest edited by Mayank Singh, Vipin Tyagi and P.K. Gupta.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Awasthi, S., Srivastava, P.K., Kumar, N. et al. A Study of the Dissemination of Malware and the Enhancement of the Lifespan of Rechargeable Wireless Sensor Networks: An Epidemiological Approach. SN COMPUT. SCI. 4, 851 (2023). https://doi.org/10.1007/s42979-023-02312-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-023-02312-z