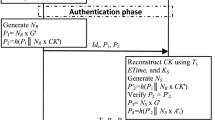
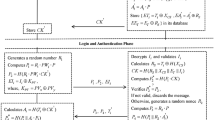
Abstract
The presence of the Internet of Things (IoT) enables the exponential growth of IoT devices. The IoT commonly involves many limited resources that are incapable of processing classical cryptographic protocols and vulnerable to threats like privacy loss, Distributed Denial of Service (DDoS) Attacks, and quantum computers. One-time passwords (OTPs) are essential in IoT for enhancing security by ensuring single-use authentication codes and preventing unauthorized access while being lightweight, scalable, and suitable for resource-constrained devices. The proposed work is a novel OTP generation scheme designed on isogeny between two Montgomery elliptic curves, such as translation maps and isogeny computed by the V élu formula to provide secure communication. This scheme is secure and lightweight due to the utilization of the Montgomery curve, known for its computational efficiency in elliptic curve operations, to significantly reduce the complexity and increase the speed of OTP generation. The security is proven by the hardness of computational Deffie Hellman (CDH) over elliptic curves and isogenies. Hence, the scheme is lightweight and suitable for use in secure IoT device communications.


Similar content being viewed by others
Data availability
The research did not generate any data to disclose, and there is no code available to share.
References
Rothmuller M, Barker S. IoT the internet of transformation 2020. Juniper Research, Basingstoke, UK, Whitepaper. 2020.
Chen L, Song Y, Ma W, Lu T, Zhang P, Chen L. A powerful adversary model and corresponding OTP time slot allocation scheme in RIS-assisted physical layer key generation. EURASIP J Wirel Commun Netw. 2024;2024(1):54.
Liu C-X, Liu Y, Zhang Z-J, Cheng Z-Y. The novel authentication scheme based on theory of quadratic residues for wireless sensor networks. Int J Distrib Sens Netw. 2013;9(3): 829048.
Chen Y, Chou J-S, Sun H-M. A novel mutual authentication scheme based on quadratic residues for RFID systems. Comput Netw. 2008;52(12):2373–80.
Yeh T-C, Wu C-H, Tseng Y-M. Improvement of the RFID authentication scheme based on quadratic residues. Comput Commun. 2011;34(3):337–41.
Kalra S, Sood SK. Advanced password based authentication scheme for wireless sensor networks. J Inf Secur Appl. 2015;20:37–46.
Odelu V, Das AK, Goswami A. An efficient biometric-based privacy-preserving three-party authentication with key agreement protocol using smart cards. Secur Commun Netw. 2015;8(18):4136–56.
; Zhao G, Si X, Wang J, Long X, Hu T. A novel mutual authentication scheme for internet of things. In: Proceedings of 2011 international conference on modelling, identification and control. IEEE; 2011. pp. 563–566.
Koner C, Bhattacharjee PK, Bhunia CT, Maulik U. A novel four entity mutual authentication technique for 3-G mobile communications. Int J Recent Trends Eng. 2009;2(2):111.
Bellare M, Hoornaert F, Naccache D, Ranen O. HOTP: an HMAC-based one-time password algorithm. Network Working Group, Request for Comments 2005; 4226.
Azrour M, Mabrouki J, Guezzaz A, Kanwal A. Internet of things security: challenges and key issues. Secur Commun Netw. 2021;2021(1):5533843.
Yan SCS, Wei ATS, Bong JH, Teh QL, Sivalingam S, Khoo SY, Nafy TM. Authentication of IoT device with the enhancement of one-time password (OTP). J IT Asia. 2021;9(1):29–40.
Elias EP, Santhanavijayan A, Janet B, Arul KRJ. OTP system based on ECC key exchange. In: 2022 International conference on communication, computing and internet of things (IC3IoT). IEEE; 2022. pp. 1–6.
Panja A, Mondal S, Islam A, Ghosh TK, Karforma S. An efficient and secure fingerprint based authentication scheme using elliptic curve cryptography. Webology 2022;19(2).
Hammi MT, Livolant E, Bellot P, Serhrouchni A, Minet P. A lightweight mutual authentication protocol for the IoT. In: Mobile and wireless technologies 2017: ICMWT 2017 4. Springer; 2018. pp. 3–12.
Jao D, De Feo L. Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies. In: Post-quantum cryptography: 4th international Workshop, PQCrypto 2011, Taipei, Taiwan, November 29–December 2, 2011. Proceedings 4. Springer; 2011. pp. 19–34.
Montgomery PL. Speeding the pollard and elliptic curve methods of factorization. Math Comput. 1987;48(177):243–64.
Williams H. A modification of the RSA public-key encryption procedure (Corresp.). IEEE Trans Inf Theory. 1980;26(6):726–9.
Boneh D, Franklin M. Identity-based encryption from the Weil pairing. In: Annual international cryptology conference. Springer; 2001. pp. 213–229.
Wu M, Garfinkel S, Miller R. Secure web authentication with mobile phones. In: DIMACS workshop on usable privacy and security software. Citeseer. 2010; 2004.
Albalawi A, Almrshed A, Badhib A, Alshehri S. A survey on authentication techniques for the internet of things. In: 2019 International conference on computer and information sciences (ICCIS). IEEE; 2019. pp. 1–5.
Prakash A, Kumar U. Authentication protocols and techniques: a survey. Int J Comput Sci Eng. 2018;6(6):1014–20.
Agrawal S, Ahlawat P. A survey on the authentication techniques in internet of things. In: 2020 IEEE international students’ conference on electrical, electronics and computer science (SCEECS), IEEE; 2020. pp. 1–5.
Mitchell CJ, Chen L. Comments on the s/key user authentication scheme. ACM SIGOPS Oper Syst Rev. 1996;30(4):12–6.
Lee Y, Kim H. Insider attack-resistant OTP (one-time password) based on bilinear maps. Int J Comput Commun Eng. 2013;2(3):304.
Yao H, Yan Q, Fu X, Zhang Z, Lan C. ECC-based lightweight authentication and access control scheme for IoT e-healthcare. Soft Comput. 2022; pp. 1–21.
Koblitz AH, Koblitz N, Menezes A. Elliptic curve cryptography: the serpentine course of a paradigm shift. J Number Theory. 2011;131(5):781–814.
Silverman JH, Suzuki J. Elliptic curve discrete logarithms and the index calculus. In: International conference on the theory and application of cryptology and information security. Springer; 1998. pp. 110–125.
Shivraj V, Rajan M, Singh M, Balamuralidhar P. One time password authentication scheme based on elliptic curves for internet of things (IoT). In: 2015 5th National symposium on information technology: towards new smart world (NSITNSW). IEEE; 2015. pp. 1–6.
Chauhan, A., Mitra, A.: A OTP-based lightweight authentication scheme in python toward possible uses in distributed applications. In: Proceedings of international conference on data science and applications: ICDSA 2022, vol. 1. Springer; 2023. pp. 781–789.
Baccouri S, Farhat H, Azzabi T, Attia R. Lightweight authentication scheme based on elliptic curve El Gamal. J Inf Telecommun. 2024;8(2):231–61.
Bernstein DJ, Lange T. Montgomery curves and the Montgomery ladder. Topics in Computational Number Theory Inspired by Peter L. Montgomery, 2017. pp. 82–115 .
Hammi B, Fayad A, Khatoun R, Zeadally S, Begriche Y. A lightweight ECC-based authentication scheme for internet of things (IoT). IEEE Syst J. 2020;14(3):3440–50.
Silverman JH. The arithmetic of elliptic curves, vol. 106. New York: Springer; 2009.
Costello C, Smith B. Montgomery curves and their arithmetic: the case of large characteristic fields. J Cryptogr Eng. 2018;8(3):227–40.
Bernstein DJ. Curve25519: new Diffie–Hellman speed records. In: Public key cryptography-PKC 2006: 9th international conference on theory and practice in public-key cryptography, New York, NY, USA, April 24–26, 2006. Proceedings 9. Springer; 2006. pp. 207–228.
Ghatpande S, Großschädl J, Liu Z. A family of lightweight twisted Edwards curves for the internet of things. In: IFIP international conference on information security theory and practice. Springer; 2018. pp. 193–206.
Funding
The authors declare that they have no financial or personal conflicts of interest related to this manuscript to disclose.
Author information
Authors and Affiliations
Contributions
Sweta Mishra investigated the research and drafted the main manuscript text. Dr. Jha supervised the research and contributed to the problem formulation. Dr. Bhaskar Mondal contributed to the literature review, prepared all the figures, proofread, and arranged the systematic review throughout. All authors equally contributed to the scientific work and reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors do not have any financial or personal conflict of interest related to this manuscript to disclose.
Ethical approval
The manuscript does not present human or animal studies, so no ethical approval is needed.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mishra, S., Mondal, B. & Jha, R.K. Lightweight Authentication Scheme Based on ECC for IoT. SN COMPUT. SCI. 5, 949 (2024). https://doi.org/10.1007/s42979-024-03291-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-024-03291-5