Abstract
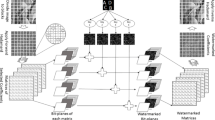
Digital watermarking is an efficient and promising means to protect intellectual properties. Based on growing attention on the intellectual property, protection of the product ownership becomes extremely important and necessary. In this paper, a quantization-based image watermarking method is proposed using dual-tree complex wavelet transform (DT-CWT) and the \(L_1\)-norm function. To enhance the robustness, the watermark is embedded in the DT-CWT domain of the high-frequency sub-band images by using the \(L_1\)-norm function. The performance of the proposed scheme is investigated in terms of image quality (peak signal-to-noise ratio or PSNR) and robustness (bit error ratio or BER). Experimental results show that the proposed method is robust against noise attack, filtering, JPEG compression, amplitude scaling and gain attack with a good invisibility.













Similar content being viewed by others
References
M.A. Akhaee, S.M.E. Sahraeian, C. Jin, Blind image watermarking using a sample projection approach. IEEE Trans. Inf. Forensics Secur. 6(3), 883–893 (2011)
J. Bai, C.C. Chang, T.S. Nguyen, C. Zhu, Y. Liu, A high payload steganographic algorithm based on edge detection. Displays 46, 42–51 (2017)
N. Bi, Q.Y. Sun, D.R. Huang, Z.H. Yang, J.W. Huang, Robust image watermarking based on multiband wavelets and empirical mode decomposition. IEEE Trans. Image Process. 16(8), 1956–1967 (2007)
B. Chen, G. Wornell, Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans. Inf. Theory 47(4), 1423–1443 (2001)
T. Celik, K.K. Ma, Unsupervised change detection for satellite images using dual-tree complex wavelet transform. IEEE Trans. Geosci. Remote Sens. 48(3), 1199–1210 (2010)
L.E. Coria, M.R. Pickering, P. Nasiopoulos, R. Kreidieh ward, A video watermarking scheme based on the dual tree complex wavelet transform. IEEE Trans. Inf. Forensics Secur. 3(3), 466–474 (2008)
M.Q. Fan, H.X. Wang, Chaos-based discrete fractional Sine transform domain audio watermarking scheme. Comput. Electr. Eng. 35(3), 506–516 (2009)
F.P. Gonzalez, C. Mosquera, M. Barni et al., Rational dither modulation: a high-rate data-hiding method invariant to gain attacks. IEEE Trans. Signal Process. 53(10), 3960–3975 (2005)
H.B. Kekre, T. Sarode, S. Natu, Robust watermarking by SVD of watermark embedded in DKT-DCT and DCT wavelet column transform of host image, in International Conference on Communication, Information, and Computing Technology (ICCICT), Mumbai, India (2015), pp. 1–6
N.K. Kalantari, S.M. Ahadi, A logarithmic quantization index modulation for perceptually better data hiding. IEEE Trans. Image Process. 19(6), 1504–1518 (2010)
Y. Li, Z. Lu, C. Zhu, X. Niu, Robust image hashing based on random gabor filtering and dithered lattice vector quantization. IEEE Trans. Image Process. 21(4), 1963–1980 (2012)
J.H. Liu, K. She, A hybrid approach of DWT and DCT for rational dither modulation watermarking. Circuits Syst. Signal Process. 31(2), 797–811 (2012)
Q. Li, I.J. Cox, Using perceptual models to improve fidelity and provide resistance to valumetric scaling for quantization index modulation watermarking. IEEE Trans Inf. Forensics Secur. 2(2), 127–139 (2007)
R. Mothi, M. Karthikeyan, A wavelet packet and fuzzy based digital image watermarking, in International Conference on Computational Intelligence and Computing Research (ICCIC) (2013), pp. 1–5
B. Ou, L. Li, Y. Zhao, R. Ni, Efficient color image reversible data hiding based on channel-dependent payload partition and adaptive embedding. Signal Process. 108, 642–657 (2015)
C. Qin, C.C. Chang, Y.-P. Chiu, A novel joint data-hiding and compression scheme based on SMVQ and image inpainting. IEEE Trans. Image Process. 23(3), 969–977 (2014)
H. Sadreazami, O. Ahmad, M.N.S. Swamy, Multiplicative watermark decoder in contourlet domain using the normal inverse gaussian distribution. IEEE Trans. Multimed. 18(2), 196–207 (2016)
P.-C. Su, Y.-C. Chang, Y. Wu, Geometrically resilient digital image watermarking by using interest point extraction and extended pilot signals. IEEE Trans. Inf. Forensics Secur. 12(8), 1897–1908 (2013)
I. Selesnick, R. Baraniuk, N. Kingsbury, The dual-tree complex wavelets transform-a coherent framework for multi-scale signal and image processing. IEEE Signal Process. Mag. 22(6), 123–151 (2005)
S. Wang, D. Zheng, J.Y. Zhao, W.J. Tam, F. Speranza, Adaptive watermarking and tree structure based image quality estimation. IEEE Trans. Multimed. 16(2), 311–325 (2014)
Z. Wang, A.C. Bovik, Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 1–14 (2004)
D.W. Xu, R.D. Wang, Y.Q. Shi, Data hiding in encrypted H.264/AVC video streams by codeword substitution. IEEE Trans. Inf. Forensics Secur. 9(4), 596–606 (2014)
M. Zareian, H.R. Tohidypour, Robust quantisation index modulation-based approach for image watermarking. IET Image Process. 7(5), 432–441 (2013)
M. Zareian, H.R. Tohidypour, Z.J. Wang, A novel quantization-based watermarking approach invariant to gain attack, in IEEE International Conference on Acoustics, Speech and Signal Processing(ICASSP) (2013) pp. 2945–2948
M. Zareian, H.R. Tohidypour, A novel gain invariant quantization-based watermarking approach. IEEE Trans. Inf. Forensics Secur. 9(11), 1804–1813 (2014)
Z. Zhang, C. Zhu, Y. Zhao, Two-description image coding with steganography. IEEE Signal Process. Lett. 15, 887–890 (2008)
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grant No. 61228102, the Natural Science Foundation of Jiangsu Province of China under Grant No. 20165024411 and the Fundamental Research Funds for the Central Universities under Grant No. 2015B01614. The authors would like to thank professor N. Kingsbury for providing the software code to perform the dual-tree complex wavelet transform and thank Dr. Qiao Li for sharing the software code of his paper in the literature [13].
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, J., Xu, Y., Wang, S. et al. Complex Wavelet-Domain Image Watermarking Algorithm Using \(L_1\)-Norm Function-Based Quantization. Circuits Syst Signal Process 37, 1268–1286 (2018). https://doi.org/10.1007/s00034-017-0607-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-017-0607-5