Abstract
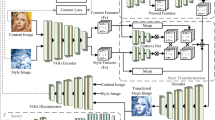
A traditional image steganography embeds secret information into a cover image to generate a secret-embedded image. The modification traces imposed on the cover image can be easily detected by steganalysis tools. Coverless steganography has been introduced to solve this problem. In this study, coverless steganography is combined with image style transfer, an arbitrary image style transfer network CSST-Net is put forward, and a secret information is encoded into the parameters (an adaptive steganography matrix) of CSST-Net, which is used to restrict the style transfer. Arbitrary image style transfer is performed instructed by the adaptive steganography matrix, and the image style transfer result driven by secret information is directly synthesized. Our experiments show that CSST-Net can not only synthesize any image style transfer result with good visual effect, but also achieve good performance in capacity, anti-steganalysis and security.









Similar content being viewed by others
References
Shen, C.X., Zhang, H.G., Feng, D.G., et al.: Survey of information security. Sci. China Ser. F Inf. Sci. 50(3), 273–298 (2007)
Wu, H.C., Wu, H.C., Wu, N.I., et al.: Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEE Proc. Vis. Image Signal Process. 152(5), 611–615 (2005)
Gulati, A.N., Sawarkar, S.D.: A new steganography approach for image encryption exchange by using the least significant bit insertion. In: International Conference & Workshop on Emerging Trends in Technology (2010)
Bender, W.R., Gruhl, D. et al.: Techniques for data hiding. IBM Syst. J. 35(3.4), 313–336 (1996)
Ni, Z., Shi, Y.Q., Ansari, N., et al.: Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 16(3), 354–362 (2006)
Li, X., Wang, J.: A steganographic method based upon JPEG and particle swarm optimization algorithm. Inf. Sci. 177(15), 3099–3109 (2007)
Mckeon, R.T.: Strange Fourier steganography in movies. In: IEEE International Conference on Electro/information Technology
Zhou, Z., Cao, Y., Sun, X.: Coverless information hiding based on bag-of-words model of image. J. Appl. Sci. 34(5), 527–536 (2016)
Otori, H.S.K.: Texture synthesis for mobile data communications. IEEE Comput. Graph. Appl. 29(6), 74–81 (2009)
Wu, K.C., Wang, C.M.: Steganography using reversible texture synthesis. IEEE Trans. Image Process. 24(1), 130–139 (2014)
Liu, M.M., Zhang, M.Q., Liu, J., et al.: Coverless information hiding based on generative adversarial networks. J. Appl. Sci. 36(002), 371–382 (2018)
Gatys, L.A., Ecker, A.S., Bethge, M.: A neural algorithm of artistic style. J. Vis. 16, 326 (2016)
Chen, T.Q., Schmidt, M.: Fast patch-based style transfer of arbitrary style (2016). arXiv:abs/1612.04337
Zhang, S., Su, S., Li, L., et al.: Arbitrary style transfer of facial image based on feed-forward network and its application in aesthetic QR code. Adv. Intell. Syst. Comput. 895 (2020)
Kaufman, L., Rousseeuw, P.J.: Agglomerative Nesting (Program AGNES). Finding Groups in Data: An Introduction to Cluster Analysis (1990). https://doi.org/10.1002/9780470316801
Yu, F., Koltun, V.: Multi-scale Context Aggregation by Dilated Convolutions (2015). arXiv:1511.07122 (2016)
Lin, T.Y., Maire, M., Belongie, S., et al.: Microsoft COCO: common objects in context. Comput. Sci. Comput. Vis. Pattern Recognit. (2014). https://doi.org/10.1007/978-3-319-10602-1_48
Li, Y., Fang, C., Yang, J., et al.: Diversified texture synthesis with feed-forward networks. In: IEEE Conference on Computer Vision and Pattern Recognition (2017)
Yi, C., Zhou, Z., Yang, C.N., et al.: Coverless information hiding based on Faster R-CNN. In: International Conference on Security with Intelligent Computing and Big-Data Services (2018)
Zhou, Z., Sun, H., Harit, R., et al.: Coverless Image Steganography Without Embedding (2015). https://doi.org/10.1007/978-3-319-27051-7_11
Wang, Y., Yang, X., Liu, J.: Cross-domain image steganography based on GANs. In: International Conference on Security with Intelligent Computing and Big-Data Services (2018)
Shanqin, Z., Shengqi, S., Li, L., et al.: An image style transfer network using multi-level noise coding mechanism and its application in coverless steganography. Symmetry 11, 1152–1170 (2019)
Liu, Q. et al.: Coverless steganography based on image retrieval of DenseNet features and DWT sequence mapping. Knowl. Based Syst. 192, 105375 (2020)
Qin, J., et al.: Coverless image steganography based on generative adversarial network. Mathematics 8(9), 1394 (2020)
Kuanar, S., Mahapatra, D., Bilas, M., et al.: Multi-path dilated convolution network for haze and glow removal in nighttime images. Vis. Comput. (2021). https://doi.org/10.1007/s00371-021-02071-z
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China under Grant No. 61802101 and in part by the Public Welfare Technology and Industry Project of Zhejiang Provincial Science Technology Department under Grant Nos. LGG18F020013 and LGG19F020016.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declared that they have no conflicts of interest to this work.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhang, S., Su, S., Li, L. et al. CSST-Net: an arbitrary image style transfer network of coverless steganography. Vis Comput 38, 2125–2137 (2022). https://doi.org/10.1007/s00371-021-02272-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00371-021-02272-6