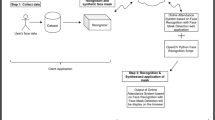
Abstract
We propose a service-oriented architecture based on biometric system where training and classification tasks are used by millions of users via internet connection. Such a large-scale biometric system needs to consider template protection, accuracy and efficiency issues. This is a challenging problem since there are tradeoffs among these three issues. In order to simultaneously handle these issues, we extract both global and local features via controlling the sparsity of random bases without training. Subsequently, the extracted features are fused with a sequential classifier. In the proposed system, the random basis features are not stored for security reason. The non-training based on feature extraction followed by a sequential learning contributes to computational efficiency. The overall accuracy is consequently improved via an ensemble of classifiers. We evaluate the performance of the proposed system using equal error rate under a stolen-token scenario. Our experimental results show that the proposed method is robust over severe local deformation with efficient computation for simultaneous transactions. Although we focus on face biometrics in this paper, the proposed method is generic and can be applied to other biometric traits.








Similar content being viewed by others
References
Achlioptas D (2003) Database-friendly random projections: Johnson-Lindenstrauss with binary coins. J Comput Syst Sci 66(4):671–687
Agulla E, Muras E, Castro J, Mateo C (2007) An open source Java framework for biometric web authentication based on BioAPI. Lecture notes in computer science, vol 4693. Springer, Berlin, p 809
Bevilacqua V, Cariello L, Carro G, Daleno D, Mastronardi G (2008) A face recognition system based on Pseudo 2D HMM applied to neural network coefficients. Soft Comput 12(7):615–621
Bhattacharjee D, Nasipuri M, Basu DK, Kundu M (2010) Human face recognition using fuzzy multilayer perceptron. Soft Comput 14(6):559–570
Bouchachia A, Mittermeir R (2007) Towards incremental fuzzy classifiers. Soft Comput 11(2):193–207
Bruce Poon MAA, Yan H (2011) Performance evaluation and comparison of pca based human face recognition methods for distorted images. Int J Mach Learn Cybern 2(4):245–259
Chacko BP, Raju G, Vimal Krishnan VR, Anto PB (2011) Handwritten character recognition using wavelet energy and extreme learning machine. Int J Mach Learn Cybern
Cheung K, Kong A, Zhang D, Kamel M, You J, Toby H (2005) An analysis on accuracy of cancelable biometrics based on biohashing. In: KES, pp 1168–1172
Cheung K, Kong A, Zhang D, Kamel M, You J (2006) Revealing the secret of facehashing. Lecture notes in computer science, vol 3832. Springer, Berlin, p 106
Goh A, Ngo D (2003) Computation of cryptographic keys from face biometrics. Lecture notes in computer science. Springer, Berlin, pp 1–13
Huang G, Zhu Q, Siew C (2006) Extreme learning machine: theory and applications. Neurocomputing 70(1–3):489–501
Huang GB, Wang DH, Lan Y (2011) Extreme learning machines: a survey. Int J Mach Learn Cybern 2(2):107–122
Huang J, Yuen PC, Lai JH, Li CH (2004) Face recognition using local and global features. EURASIP J Appl Signal Process 4
Jain A, Nandakumar K, Nagar A (2008) Biometric template security. EURASIP J Adv Signal Process 2008:1–17
Jin ATB, Connie T (2006) Remarks on BioHashing based cancelable biometrics in verification system. Neurocomputing 69(16–18):2461–2464
Jones M, Viola P (2003) Face recognition using boosted local features. In: Proceedings of international conference on computer vision
Jun W, Shitong W, Chung F-l (2011) Positive and negative fuzzy rule system, extreme learning machine and image classification. Int J Mach Learn Cybern 2(4):261–271
Kikuchi H, Ogata W, Nagai K, Nishigaki M (2010) Privacy-preserving similarity evaluation and application to remote biometrics authentication. Soft Comput 14(5):529–536
Kong A, Cheung K, Zhang D, Kamel M, You J (2006) An analysis of BioHashing and its variants. Pattern Recogn Lett 39(7):1359–1368
Lawrence S, Giles CL, Tsoi AhC, Back AD (1997) Face recognition: a convolutional neural-network approach. IEEE Trans Neural Netw 8(1):98–113
Li SZ, Zhang Z (2004) Floatboost learning and statistical face detection. IEEE Trans Pattern Anal Mach Intell 26:1112–1123
Li P, Hastie T, Church K (2006) Very sparse random projections. In: Proceedings of the 12th ACM SIGKDD international conference on knowledge discovery and data mining. ACM, New York, p 296
Liang N, Huang G, Saratchandran P, Sundararajan N (2006) A fast and accurate online sequential learning algorithm for feedforward networks. IEEE Trans Neural Netw 17(6):1411–1423
Liao S, Zhu X, Lei Z, Zhang L, Li S (2007) Learning multi-scale block local binary patterns for face recognition. Lecture notes in computer science, vol 4642. Springer, Berlin, p 828
Lu Y, Sundararajan N, Saratchandran P (1998) Performance evaluation of a sequential minimal radial basis function (RBF) neural network learning algorithm. IEEE Trans Neural Netw 9(2):308–318
Maltoni D, Jain A, Prabhakar S (2009) Handbook of fingerprint recognition. Springer, Berlin
Mehrotra H, Kisku D, Radhika V, Majhi B, Gupta P (2010) Feature level clustering of large biometric database. Arxiv preprint arXiv:10020383
Orriols-Puig A, Casillas J (2010) Fuzzy knowledge representation study for incremental learning in data streams and classification problems. Soft Comput (online first)
Palla S, Chikkerur S, Govindaraju V, Rudravaram P (2004) Classification and indexing in large biometric databases. In: Biometrics consortium conference, Crystal City
Ratha N, Connell J, Bolle R (2001) Enhancing security and privacy in biometrics-based authentication systems. IBM Syst J 40(3):614–634
Shan C, McOwan PW, Gong S (2009) Facial expression recognition based on local binary patterns: a comprehensive study. Image Vis Comput 27(6):803–816
Snelick R, Uludag U, Mink A, Indovina M, Jain A (2005) Large-scale evaluation of multimodal biometric authentication using state-of-the-art systems. IEEE Trans Pattern Anal Mach Intell 27:450–455
Swope (2011) Large scale soa-based biometric system design. http://www.noblis.org/MissionAreas/nsi/ThoughtLeadership/IdentityDiscoveryManagement/Documents/LargeScaleSOABasedBiometricSystemDesign.pdf
Teoh A, Ngo D (2005) Cancellable biometerics featuring with tokenised random number. Pattern Recogn Lett 26(10):1454–1460
Teoh A, Yuang C (2007) Cancelable biometrics realization with multispace random projections. IEEE Trans Syst Man Cybern Part B 37(5):1096
Teoh A, Ngo D, Goh A (2004) Personalised cryptographic key generation based on FaceHashing. Comput Security 23(7):606–614
Teoh A, Goh A, Ngo D (2006) Random multispace quantization as an analytic mechanism for biohashing of biometric and random identity inputs. IEEE Trans Pattern Anal Mach Intell 28(12):1892
Teoh A, Kuan Y, Lee S (2008) Cancellable biometrics and annotations on BioHash. Pattern Recogn Lett 41(6):2034–2044
Toh K (2008) Deterministic neural classification. Neural Comput 20(6):1565–1595
Viola P, Jones M (2002) Robust real-time object detection. Int J Comput Vis 57(2):137–154
Wang X, Dong C (2009) Improving generalization of fuzzy if–then rules by maximizing fuzzy entropy. IEEE Trans Fuzzy Syst 17(3):556–567
Wang X, Chen A, Feng H (2011a) Upper integral network with extreme learning mechanism. Neurocomputing 74(16):2520–2525
Wang X, Dong L, Yan J (2011b) Maximum ambiguity based sample selection in fuzzy decision tree induction. IEEE Trans Knowl Data Eng 99:1
Xu X, Liu W, Venkatesh S (2011) An innovative face image enhancement based on principle component analysis. Int J Mach Learn Cybernetics
Yang X, Lu J, Zhang G (2010) Adaptive pruning algorithm for least squares support vector machine classifier. Soft computing 14(7):667–680 (online first)
Yu W, Teng X, Liu C (2006) Face recognition fusing global and local features. J Electron Imaging 15:013–014
Zhang L, Chu R, Xiang S, Liao S, Li S (2007) Face detection based on multi-block lbp representation. Lecture notes in computer science, vol 4642. Springer, Berlin, p 11
Acknowledgments
This research was supported by MKE, Korea under ITRC NIPA-2012-(C1090-1221-0008) and this research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education, Science and Technology (2009-0067625).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Choi, K., Toh, KA., Uh, Y. et al. Service-oriented architecture based on biometric using random features and incremental neural networks. Soft Comput 16, 1539–1553 (2012). https://doi.org/10.1007/s00500-012-0827-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-012-0827-3