Abstract
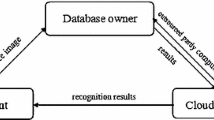
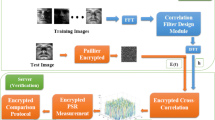
Private image data, especially including the biometric data with an authentication property, has received more and more attention along with the development of researches on big data. Consequently, to protect the private image data while enabling outsourced image computations becomes a major concern. In this present paper, we study the privacy-preserving face recognition by using a method that is different from the method of fuzzy classification recognition, which is scale-invariant feature transform (SIFT) as our key technical tool. We first propose a scheme in which the client encrypts his private image data locally and outsources the corresponding results to a company. The latter performs most of the computations, but remains ignorant of the original data. To prevent some potential adversary from forging the data, we introduce a third party who can decrypt any given valid ciphertext. Based on these ideas, we adopt the BCP double-decryption cryptosystem for our scheme. Some analyses show that our proposed scheme is secure, efficient and scalable.



Similar content being viewed by others
References
Blake IF, Kolesnikov V (2006) Conditional encrypted mapping and comparing encrypted numbers. In: Financial Cryptography and Data Security, Springer, pp 206–220
Blakley GR et al (1979) Safeguarding cryptographic keys. Proc Natl Comp Conf 48:313–317
Blundo C, Cresti A, De Santis A, and Vaccaro U (1994) Fully dynamic secret sharing schemes. In: Advances in Cryptology–CRYPTO’93, Springer, pp 110–125
Blundo C, De Santis A, De Simone R, Vaccaro U (1997) Tight bounds on the information rate of secret sharing schemes. Designs Codes Cryptograph 11(2):107–110
Blundo C, De Santis A, Vaccaro U (1993) Efficient sharing of many secrets. In: STACS 93, Springer, pp 692–703
Boneh D, Goh EJ, and Nissim K (2005). Evaluating 2-dnf formulas on ciphertexts. In Theory of cryptography, pages 325–341. Springer
Bresson E, Catalano D, Pointcheval D (2003) A simple public-key cryptosystem with a double trapdoor decryption mechanism and its applications. In: Advances in Cryptology-ASIACRYPT 2003, Springer, pp 37–54
Brown M, Lowe DG (2007) Automatic panoramic image stitching using invariant features. Int J Comp Vision 74(1):59–73
Damgård I, Geisler M, Krøigaard M (2007) Efficient and secure comparison for on-line auctions. In: Information security and privacy, Springer, pp 416–430
Damgård I, Geisler M, Krøigaard M (2009) A correction to ‘efficient and secure comparison for on-line auctions’. Int J Appl Cryptograph 1(4):323–324
De Santis A, Desmedt Y, Frankel Y, Yung M (1994) How to share a function securely. In: Proceedings of the twenty-sixth annual ACM symposium on Theory of computing, ACM, pp 522–533
Garay JA, Schoenmakers B, Villegas J (2007) Practical and secure solutions for integer comparison. In Public Key Cryptography-PKC 2007, Springer, pp 330–342
Goldreich O (2004).Foundations of cryptography: volume 2, basic applications. Cambridge University Press
Grauman K and Fergus R (2013). Learning binary hash codes for large-scale image search. In: Machine learning for computer vision, Springer, pp 49–87
Hsu CY, Lu CS, Pei SC (2012) Image feature extraction in encrypted domain with privacy-preserving sift. IEEE Trans Image Process 21(11):4593–4607
Jégou H, Zisserman A (2014) Triangulation embedding and democratic aggregation for image search. In: IEEE Conference on Computer Vision and Pattern Recognition (CVPR), 2014, IEEE, pp 3310–3317
Ke Y, Sukthankar R, Huston L, Ke Y, Sukthankar R (2004) Efficient near-duplicate detection and sub-image retrieval. In: Proceedings of the 12th Annual ACM International Conference on Multimedia, vol 4, pp 869–876
Kolesnikov V, Sadeghi AR, Schneider T (2009) Improved garbled circuit building blocks and applications to auctions and computing minima. In: Cryptology and Network Security, Springer, pp 1–20
Li J, Kim K, Zhang F, Chen X (2007) Aggregate proxy signature and verifiably encrypted proxy signature. Provable Security, Springer, pp 208–217
Lindeberg T (1994) Scale-space theory: a basic tool for analyzing structures at different scales. J Appl Stat 21(1–2):225–270
Lindell Y, Pinkas B (2009) A proof of security of yao’s protocol for two-party computation. J Cryptol 22(2):161–188
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comp Vision 60(2):91–110
Naor M, Pinkas B, Sumner R (1999) Privacy preserving auctions and mechanism design. In Proceedings of the 1st ACM conference on Electronic commerce, ACM, pp 129–139
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: Advances in cryptology-EUROCRYPT’99, Springer, pp 223–238
Peter A, Tews E, Katzenbeisser S (2013) Efficiently outsourcing multiparty computation under multiple keys. IEEE Trans Inform Foren Security 8(12):2046–2058
Qin Z, Yan J, Ren K, Chen CW, Wang C (2014) Towards efficient privacy-preserving image feature extraction in cloud computing. In: Proceedings of the ACM International Conference on Multimedia, ACM, pp 497–506
Sadeghi AR, Schneider T, Wehrenberg I (2010) Efficient privacy-preserving face recognition. In: Information, Security and Cryptology–ICISC 2009. Springer, Heidelberg, pp 229–244
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Tang Y, Liu L (2015) Privacy-preserving multi-keyword search in information networks. IEEE Trans Knowl Data Eng 27(9):2424–2437
Tuyls P, Akkermans AHM, Kevenaar TAM, Schrijen GJ, Bazen AM, Veldhuis RNJ (2005) Practical biometric authentication with template protection. In: Audio-and Video-Based Biometric Person Authentication, Springer, pp 436–446
Wang B, Yu S, Lou W, Hou YT (2014) Privacy-preserving multi-keyword fuzzy search over encrypted data in the cloud. In: Proceedings IEEE INFOCOM, 2014, pp 2112–2120
Wang J, Ma H, Tang Q, Li J, Zhu H, Ma S, Chen X (2013) Efficient verifiable fuzzy keyword search over encrypted data in cloud computing. Comp SciInform Syst 10(2):667–684
Yao ACC (1982) Protocols for secure computations. In: 23rd annual symposium on foundations of computer science (Chicago, Ill., 1982), IEEE, New York, pp 160–164
Yao ACC (1986) How to generate and exchange secrets. In: 27th Annual Symposium on Foundations of Computer Science, 1986, IEEE, pp 162–167
Zhou J, Cao Z, Dong X, Lin X (2015) PPDM: A privacy-preserving protocol for cloud-assisted e-healthcare systems. IEEE J Select Topics Signal Process 9(7):1332–1344
Acknowledgments
The work of Zheng-An Yao was partially supported by the NSFC (Grant Nos. 11271381, 11431015) and China 973 Program (Grant No. 2011 CB808000). Chun-Ming Tang’s work was supported by the NSFC (Grant No. 11271003), the National Research Foundation for Doctoral Program of Higher Education of China (Grant No. 20134410110003), and the Project of Department of Education of Guangdong Province (Grant No. 2013KJCX0146). Last, but not least, the authors are very grateful to the editor and the reviewers for their valuable comments.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest between the authors.
Informed consent
This article does not contain any studies with human participants performed by any of the authors.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Li, P., Li, T., Yao, ZA. et al. Privacy-preserving outsourcing of image feature extraction in cloud computing. Soft Comput 21, 4349–4359 (2017). https://doi.org/10.1007/s00500-016-2066-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-016-2066-5