Abstract
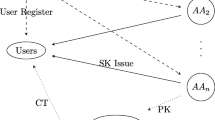
For realizing the flexible, scalable and fuzzy fine-grained access control, ciphertext policy attribute-based encryption (CP-ABE) scheme has been widely used in the cloud storage system. However, the access structure of CP-ABE scheme is outsourced to the cloud storage server, resulting in the disclosure of access policy privacy. In addition, there are multiple authorities that coexist and each authority is able to issue attributes independently in the cloud storage system. However, existing CP-ABE schemes cannot be directly applied to data access control for multi-authority cloud storage system, due to the inefficiency for user revocation. In this paper, to cope with these challenges, we propose a decentralized multi-authority CP-ABE access control scheme, which is more practical for supporting the user revocation. In addition, this scheme can protect the data privacy and the access policy privacy with policy hidden in the cloud storage system. Here, the access policy that is realized by employing the linear secret sharing scheme. Finally, the security and performance analyses demonstrate that our scheme has high security in terms of access policy privacy and efficiency in terms of computational cost of user revocation.


Similar content being viewed by others
References
Beimel A (1996) Secure schemes for secret sharing and key distribution. Technion-Israel Institute of technology, Faculty of computer science
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: IEEE symposium on security and privacy, IEEE, pp 321–334
Castiglione A, Cattaneo G, De Maio G, Petagna F (2011) Secr3t: secure end-to-end communication over 3g telecommunication networks. In: Proceedings of innovative mobile and internet services in ubiquitous computing (IMIS) 2011, IEEE, pp 520–526
Chatterjee S, Sarkar P (2006) Multi-receiver identity-based key encapsulation with shortened ciphertext. In: Progress in cryptology–INDOCRYPT 2006, Springer, NewYork, pp 394–408
De SJ, Ruj S (2015) Decentralized access control on data in the cloud with fast encryption and outsourced decryption. In: Proceedings of the global communications conference 2015, IEEE, pp 1–6
Fu Z, Sun X, Liu Q, Zhou L, Shu J (2015) Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans Commun 98(1):190–200
Han J, Susilo W, Mu Y, Zhou J, Au MHA (2015) Improving privacy and security in decentralized ciphertext-policy attribute-based encryption. IEEE Trans Inf Forensics Secur 10(3):665–678
He D, Zeadally S, Wu L (2015) Certificateless public auditing scheme for cloud-assisted wireless body area networks. IEEE Syst J 99:1–10
Hu VC, Kuhn DR, Ferraiolo DF (2015) Attribute-based access control. Computer 2:85–88
Huang X, Liu JK, Tang S, Xiang Y, Liang K, Xu L, Zhou J (2015) Cost-effective authentic and anonymous data sharing with forward security. IEEE Trans Comput 64(4):971–983
Jung T, Li XY, Wan Z, Wan M (2013) Privacy preserving cloud data access with multi-authorities. In: Proceedings of the IEEE INFOCOM 2013, IEEE, pp 2625–2633
Kate A, Zaverucha G, Goldberg I (2007) Pairing-based onion routing. In: Privacy enhancing technologies, Springer, NewYork, pp 95–112
Lai J, Deng RH, Li Y (2012) Expressive CP-ABE with partially hidden access structures. In: Proceedings of the 7th ACM symposium on information. ACM, computer and communications security, pp 18–19
Lewko A, Waters B (2011) Decentralizing attribute-based encryption. In: Advances in cryptology–EUROCRYPT 2011, Springer, NewYork, pp 568–588
Li W, Xue K, Xue Y, Hong J (2015) Tmacs: a robust and verifiable threshold multi-authority access control system in public cloud storage. IEEE Trans Inf Forensics Secur 10(1):55–68
Liu Z, Cao Z, Huang Q, Wong DS, Yuen TH (2011) Fully secure multi-authority ciphertext–policy attribute-based encryption without random oracles. In: Computer security– ESORICS 2011, Springer, NewYork, pp 278297
Müller S, Katzenbeisser S, Eckert C (2008) Distributed attribute-based encryption. In: Information security and cryptology–ICISC 2008, Springer, NewYork, pp 20–36
Nishide T, Yoneyama K, Ohta K (2008) Attribute-based encryption with partially hidden encryptor-specified access structures. In: Applied cryptography and network security, Springer, NewYork, pp 111–129
Phuong TVX, Yang G, Susilo W (2016) Hidden ciphertext policy attribute-based encryption under standard assumptions. IEEE Trans Inf Forensics Secur 11(1):35–45
Ren YJ, Shen J, Wang J, Han J, Lee SY (2015) Mutual verifiable provable data auditing in public cloud storage. J Internet Technol 16(2):317–323
Ruj S, Stojmenovic M, Nayak A (2014) Decentralized access control with anonymous authentication of data stored in clouds. IEEE Trans Parallel Distrib Syst 25(2):384–394
Sahai A, Waters B (2005) Fuzzy identity-based encryption. In: Advances in cryptology EUROCRYPT 2005, Springer, NewYork, pp 457–473
Shao J, Lu R, Lin X (2015) Fine-grained data sharing in cloud computing for mobile devices. In: Proceedings of the IEEE INFOCOM 2015, IEEE, pp 2677–2685
Wang H, Zheng Z, Wu L, He D (2016a) New large-universe multi-authority ciphertext-policy abe scheme and its application in cloud storage systems. J High Speed Netw 22(2):153–167
Wang J, Chen X, Huang X, You I, Xiang Y (2015) Verifiable auditing for outsourced database in cloud computing. IEEE Trans Comput 64(11):3293–3303
Wang S, Zhou J, Liu JK, Yu J, Chen J, Xie W (2016b) An efficient file hierarchy attribute-based encryption scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(6):1265–1277
Xia Z, Wang X, Sun X, Wang Q (2016) A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27(2):340–352
Xu R, Lang B (2015) A CP-ABE scheme with hidden policy and its application in cloud computing. Int J Cloud Comput 4(4):279–298
Yadav UC, Ali ST (2015) Ciphertext policy-hiding attributebased encryption. In: Proceedings of advances in computing, communications and informatics 2015, IEEE, pp 2067–2071
Yang K, Jia X (2014a) DAC-MACS: Effective data access control for multi-authority cloud storage systems. In: Security for cloud storage systems, Springer, NewYork, pp 59–83
Yang K, Jia X (2014b) Expressive, efficient, and revocable data access control for multi-authority cloud storage. IEEE Trans Parallel Distrib Syst 25(7):1735–1744
Yu J, Ren K, Wang C (2016) Enabling cloud storage auditing with verifiable outsourcing of key updates. IEEE Trans Inf Forensics Secur 11(6):1362–1375
Zhou J, Cao Z, Dong X, Lin X (2015a) TR-MABE: whitebox traceable and revocable multi-authority attributebased encryption and its applications to multi-level privacy-preserving e-healthcare cloud computing systems. In: Proceedings of the IEEE INFOCOM 2015, IEEE, pp 2398–2406
Zhou Z, Huang D, Wang Z (2015b) Efficient privacy preserving ciphertext-policy attribute based-encryption and broadcast encryption. IEEE Trans Comput 64(1):126–138
Acknowledgments
The work was supported by the National Natural Science Foundation of China (No. 61572001, No.61502008), the Research Fund for the Doctoral Program of Higher Education (No. 20133401110004), the Natural Science Foundation of Anhui Province (No. 1508085QF132), and the Doctoral Research Start-up Funds Project of Anhui University. The authors are very grateful to the anonymous referees for their detailed comments and suggestions regarding this paper.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Zhong, H., Zhu, W., Xu, Y. et al. Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage. Soft Comput 22, 243–251 (2018). https://doi.org/10.1007/s00500-016-2330-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-016-2330-8