Abstract
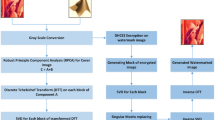
In the modern era of technology, watermarking plays an important role in embedding of the copyright information in order to provide authenticity in imperceptible and robust manner. In this paper, a new watermarking technique is introduced that works in correlation with discrete Tchebichef transform (DTT), robust principal component analysis (R-PCA) and singular value decomposition (SVD). To enhance the security and robustness, the watermark logo is scrambled using CAT mapping scrambling. The original image is decomposed to low-rank and sparse components using R-PCA; curvelet transforms are obtained using DTT to embed the processed watermark using SVD into colored image. The robustness and imperceptibility of the proposed technique are verified by testing against a variety of the geometric and image processing attacks. The substantial results obtained show that this technique is more computationally effective and provides high resistance against attacks. Moreover, this technique provides a large area for researchers to work on and further modify it.



Similar content being viewed by others
References
Bhowmik D, Oakes M, Abhayaratne C (2016) Visual attention-based image watermarking. IEEE Access 4(9):8002–8018
Gao G, Cui Z, Zhou C (2018) Blind reversible authentication based on PEE and CS reconstruction. IEEE Signal Process Lett
Guo Y, Cao X, Zhang W, Wang R (2018) Fake colorized image detection. arXiv preprint arXiv:1801.02768
Juarez-Sandoval O, Fragoso-Navarro E, Cedillo-Hernandez M, Cedillo-Hernandez A, Nakano M, Perez-Meana H (2018) Improved imperceptible visible watermarking algorithm for auxiliary information delivery. IET Biom 7(4):305–313
Khan A (2014) Joint ownership verification for digital text. Adv Comput Sci Appl 3(4):525–531
Khan A (2015a) Comparative analysis of watermarking techniques. Sci Int 27(6):6091–6096
Khan A (2015b) Robust textual steganography. J Sci 4(4):426–434
Khan A, Sarfaraz A (2017) Vetting the security of mobile applications. Sci Int 29(2):361–365
Khan A, Sarfaraz A (2018a) Practical guidelines for securing wireless local area networks (WLANs). Int J Secur Appl 12(3):19–28
Khan A, Sarfaraz A (2018b) Novel high-capacity robust and imperceptible image steganography scheme using multi flipped permutations and frequency entropy matching method. Soft Comput. https://doi.org/10.1007/s00500-018-3441-1
Khan A, Sohaib M, Amjad FM (2016) High-capacity multi-layer framework for highly robust textual steganography. Sci Int 28(5):4451–4457
Lin ZX, Peng F, Long M (2018) A low-distortion reversible watermarking for 2D engineering graphics based on region nesting. IEEE Trans Inf Forensics Secur 13(9):2372–2382
Liu S, Pan Z, Song H (2017) Digital image watermarking method based on DCT and fractal encoding. IET Image Proc 11(10):815–821
Loan NA, Hurrah NN, Parah SA, Lee JW, Sheikh JA, Bhat GM (2018) Secure and robust digital image watermarking using coefficient differencing and chaotic encryption. IEEE Access 6:19876–19897
Martínez S, Gérard S, Cabot J (2018) On watermarking for collaborative model-driven engineering. IEEE Access 6:29715–29728
Miri A, Faez K (2018) An image steganography method based on integer wavelet transform. Multimed Tools Appl 77(11):13133–13144
Nie X, Li X, Chai Y, Cui C, Xi X, Yin Y (2018) Robust image fingerprinting based on feature point relationship mining. IEEE Trans Inf Forensics Secur 13(6):1509–1523
Noor R, Khan A, Sarfaraz A (2018) High performance and energy efficient image watermarking for video using a mobile device. Wirel Pers Commun. https://doi.org/10.1007/s11277-018-6097-3
Qin Z, Weng J, Cui Y, Ren K (2018) Privacy-preserving image processing in the cloud. IEEE Cloud Comput 5(2):48–57
Saidi M, Hermassi H, Rhouma R, Belghith S (2017) A new adaptive image steganography scheme based on DCT and chaotic map. Multimed Tools Appl 76(11):13493–13510
Sarfaraz A, Khan A (2018) Feature selection based correlation attack on HTTPS secure searching. Wireless Pers Commun 103(4):2995–3008
Sarreshtedari S, Akhaee MA, Abbasfar A (2015) A watermarking method for digital speech self-recovery. IEEE Trans Audio Speech Lang Process 23(11):1917–1925
Shahdoosti HR, Salehi M (2017) Transform-based watermarking algorithm maintaining perceptual transparency. IET Image Proc 12(5):751–759
Shuguo Y, Qingliang L (2017) Image watermarking algorithm based on wavelet transform. In: 2017 IEEE 2nd international conference on signal and image processing, pp 116–121
Sutojo T, Rachmawanto EH, Sari CA (2017) Fast and efficient image watermarking algorithm using discrete tchebichef transform. In: 2017 5th IEEE international conference on cyber and IT service management, pp 1–5
Wang Y, Liu J, Yang Y, Ma D, Liu R (2017) 3D model watermarking algorithm robust to geometric attacks. IET Image Proc 11(10):822–832
Wang YG, Zhu G, Shi YQ (2018) Transportation spherical watermarking. IEEE Trans Image Process 27(4):2063–2077
Wu HZ, Shi YQ, Wang HX, Zhou LN (2017) Separable reversible data hiding for encrypted palette images with color partitioning and flipping verification. IEEE Trans Circuits Syst Video Technol 27(8):1620–1631
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Mentioned authors have no conflict of interest upon this article.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by A. Di Nola.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Noor, R., Khan, A., Sarfaraz, A. et al. Highly robust hybrid image watermarking approach using Tchebichef transform with secured PCA and CAT encryption. Soft Comput 23, 9821–9829 (2019). https://doi.org/10.1007/s00500-019-03838-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-019-03838-2