Abstract
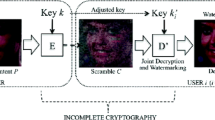
In this paper, we present a new scheme of digital rights management (DRM) system employing the fragile watermarking with permutation code for the image distribution via network. General DRM systems are designed to protect the copyright of contents and to trace the source of the illegal distributors based on the user-side watermarking. However, in the typical DRM systems, the original digital contents are temporarily disclosed without the watermarking information inside user’s system by the decryption process. Therefore, the user can copy the leaked original content inside the system and illegally redistribute via network without the permission of the content providers. Our work describes the idea of a DRM method which is composed of the incomplete cryptography based on permutation codes and user identification mechanism to control the quality of digital contents. There are two fundamental steps in our proposed cryptography: incomplete encoding and incomplete decoding. These two steps will create the scrambled content that is used as trial content and the watermarked content that is used to prevent unauthorized duplication or business of digital contents, respectively. Experimental results show that the proposed method is suitable for DRM in the network distribution system.










Similar content being viewed by others
References
Halderman, J.A.: Evaluating new copy-prevention techniques for audio CDs. In: Proceedings of ACM Workshop on Digital Rights Management (DRM), Washington, D.C. (2002)
DRM technology: Advanced image seminar 2003. The Institute of Image Electronics Engineers of Japan (2003)
Liu, Q., Safavi-Naini, R., Sheppard, N.P.: Digital rights management for content distribution. Australasian Information Security Workshop 2003 (AISW2003), vol. 21, pp. 49–58 (2003)
Kim, G.H., Shin, D.K., Shin, D.G.: An Efficient Methodology for Multimedia Digital Rights Management on Mobile Handset. IEEE Trans Consum Electron 50(4), 1130–1134 (2004)
Michiels, S., Verslype, K., Joosen, W., Decker, B.D.: Towards a software architecture for DRM. In: Proceedings of the 5th ACM workshop on Digital rights management, pp. 65–74 (2005)
Subramanya, S., Yi, B.: Digital rights management. Potential IEEE 25, 31–34 (2006)
Hartung, F., Ramme, F.: Digital rights management and watermarking of multimedia content for M-commerce applications. In: IEEE Communications Magazine, Selected Papers from ISS2000, pp. 77–84 (2000)
Lin, E.T., Eskicioglu, A.M., Lagendijk, R.L., Delp, E.J.: Advances in digital video content protection. Proc IEEE 93(1), 171–183 (2005)
Seki, A., Kameyama, W.: A proposal on open DRM system coping with both benefits of rights-holders and users. IEEE conf Image Proc 7, 4111–4115 (2003)
Lin, C.Y., Prangjarote, P., Kang, L.W., Huang, W.L., Chen, T.H.: Joint fingerprinting and decryption with noise-resistant for vector quantization images. Signal Process 92(9), 2159–2171 (2012)
Kundur, D., Karthik, K.: Video fingerprinting and encryption principles for digital rights management. Proc. IEEE 92(6), 918–932 (2004)
Karthik, K., Hatzinakos, D.: Decryption key design for joint fingerprinting and decryption in the sign bit plane for multicast content protection. I. J. Netw Secur 4(3), 254–265 (2007)
Macq, B.M., Quisquater, J.J.: Cryptology for digital TV broadcasting. Proc IEEE 83(6), 944–957 (1995)
Hartung, F., Girod, B.: Digital watermarking of MPEG-2 coded video in the bitstream domain. In: Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, vol. 4, pp. 2621–2624 (1997)
Bloom, J.: Security and rights management in digital cinema. In: Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, vol. 4, pp. 712–715 (2003)
Guo, J.M., Chang, C.H.: Prediction-based watermarking schemes using ahead/post AC prediction. Signal Process 8(90), 2552–2566 (2010)
Anderson, R.J., Manifavas, C.: Chameleon, a new kind of stream cipher. In: Proceedings of the 4th International Workshop on Fast Software Encryption, pp.107–113, 1997
Lian, S.: Multimedia content encryption: techniques and applications. CRC Press (Auerbach Publications) (2008)
Iwakiri, M., Thanh, T.M.: Incomplete cryptography method using invariant Huffman code length to digital rights management. In: The 26th IEEE International Conference on Advanced Information Networking and Applications (AINA-2012) (2012)
Thanh, T.M., Iwakiri, M.: A proposal of digital rights management based on incomplete cryptography using invariant Huffman code length feature. J. Multimed Sys, pp. 1–16 (2014) (ISSN 1432-1882)
Lee, Y., Park, S., Kim, C., Lee, S.: Temporal feature modulation for video watermarking. IEEE Trans. Circuits Syst. Video Techn. 19(4), 603–608 (2009)
Wang, L., Ling, H., Zou, F., Lu, Z.: Real-time compressed–domain video watermarking resistance to geometric distortions. IEEE MultiMedia 19(1), 70–79 (2012)
The International Telegraph and Telephone Consultative Committee Information Technology: Digital compression and coding of continuous-tone still images—requirements and guidelines, International Telecommunication Union (1992)
Matsui, K.: Fundamentals of digital watermarking. Morikita-publisher (1998) (in Japanese)
Test images: Computer Vision Group, University of Granada, Spain, http://decsai.ugr.es/cvg/index2.php. (2008)
Thanh, T.M., Hiep, P.T., Tam, T.M., Tanaka, K.: Robust semi-blind video watermarking based on frame-patch matching. Int J Electron Commun AEU 68(10), 1007–1015 (2014) (Elsevier, ISSN: 1434-8411)
Wang, Z., Bovik, A.C., Sheikh, H.R., Simoncelli, E.P.: Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process 13(4), 600–612 (2004)
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by L. Zhou.
Rights and permissions
About this article
Cite this article
Thanh, T.M., Iwakiri, M. Fragile watermarking with permutation code for content-leakage in digital rights management system. Multimedia Systems 22, 603–615 (2016). https://doi.org/10.1007/s00530-015-0472-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-015-0472-7