Abstract
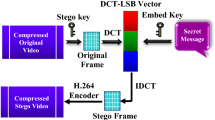
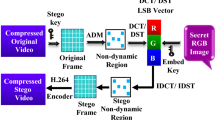
The proposed research work is presenting a novel approach in the field of steganography, especially in the compressed video domain with optimum imperceptibility to secure the secret information. In this approach, the specific secret cover video frames are selected from the sequence of video frame from which the non-dynamic region is separated. Discrete sine transform (DST) transforms this non-dynamic region from spatial domain to frequency domain. The least significant bits (LSBs) of the integer part of DST components are used to conceal the secret data. The H.264 codec is used to construct the compressed stego video using intra-frame, inter-frame prediction, motion vector estimation, transform coefficient, i.e., Discrete Cosine Transform (DCT), quantization, and entropy coding. The efficiency of the proposed hybrid technique “DST- Secret Bit Positions of Non-dynamic Region for Message (DST-SBPNRM)” for video steganography is measured by evaluating imperceptibility, robustness and embedding capacity. Moreover, the proposed technique is experimented on the well-defined video dataset and the obtained results are compared with the related work to validate the significance of the proposed work.




Similar content being viewed by others
References
Liu, Y., Liu, S., Wang, Y., Zhao, H., Liu, S.: Video steganography: a review. Neurocomputing (2018). https://doi.org/10.1016/j.neucom.2018.09.091. ((accepted manuscript; Elsevier November 2018))
Mstafa, R.J., Elleithy, K.M.: Compressed and raw video steganography techniques: a comprehensive survey and analysis. Multimedia Tools Appl. 76(20), 21749–21786 (2017)
Mstafa, R.J., Elleithy, K.M., Abdelfattah, E.: Video steganography techniques: taxonomy, challenges, and future directions. Applications and Technology Conference (LISAT), 2017 IEEE Long Island, pp. 1–6. IEEE (2017). https://doi.org/10.1109/LISAT.2017.8001965
Richardson, I.E.: The H.264 advanced video compression standard. Wiley, New York (2010).. ((ISBN: 978-0-470-51692-8))
Mstafa, R.J., Elleithy, K.M.: A DCT-based robust video steganographic method using BCH error correcting codes. In: 2016 IEEE Long Island Systems, Applications and Technology Conference (LISAT). IEEE (2016). https://doi.org/10.1109/LISAT.2016.7494111
Liu, S., Xu, D.: A robust steganography method for HEVC based on secret sharing. Cogn. Syst. Res. 59, 207–220 (2020). https://doi.org/10.1016/j.cogsys.2019.09.008
Yilmaz, A., Alatan, A.A.: Error concealment of video sequences by data hiding. In: 2003 International Conference on Image Processing, pp. 679–682. IEEE (2003). https://doi.org/10.1109/ICIP.2003.1246771
Shukur, W.A., Abdullah, W.N., Qurban, L.K.: Information hiding in digital video using DCT, DWT and CvT. J. Phys. Conf. Ser. 1003, 1–19 (2018). ((Conference 1))
Mstafa, R.J., Elleithy, K.M.: A novel video steganography algorithm in DCT domain based on hamming and BCH codes. In: 37th IEEE Sarnoff Symposium, pp. 208–213. IEEE (2016). https://doi.org/10.1109/SARNOF.2016.7846757
Mstafa, R.J., Elleithy, K.M., Abdelfattah, E.: A robust and secure video steganography method in DWT-DCT domains based on multiple object tracking and ECC. IEEE Access (vol. 5), pp. 5354–5365. IEEE, Institute of Electrical Electronics Engineers, Inc. (2017). https://doi.org/10.1109/ACCESS.2017.2691581, Accessed 6th Apr 2017. (ISSN No.: 2169-3536)
Britanak, V., Rao, K.R.: Two-dimensional DCT/DST universal computational structure for 2m×2n block sizes. IEEE Trans. Signal Process. (2000). https://doi.org/10.1109/78.875483
Chan, A., Zeng, K., Mohapatra, P., Lee, S.-J., Banerjee, S.: Metrics for evaluating video streaming quality in Lossy IEEE 802.11 wireless networks. In: INFOCOM'10: Proceedings of the 29th Conference on Information Communications, pp. 1613–1621 (2010)
Video compression Guru, Elecard Video (2019). https://www.elecard.com/videos
Mstafa, R.J., Elleithy, K.M.: An ECC/DCT—based robust video steganography algorithm for secure data communication. J. Cyber Secur. 53, 167–194 (2017)
Tampere University of Technology, Ultra Video Group (2018). http://ultravideo.cs.tut.fi/#testsequences. Accessed on 15 Jul 2018
Xiph.org Foundation, Derf’s test media collection (2017). https://media.xiph.org/video/derf/. Accessed on 27 Oct 2017
Remega video database (2017). https://github.com/remega/video_database/tree/master/videos. Accessed on 8 Nov 2017
Yang, J., Li, S.: An efficient information hiding method based on motion vector space encoding for HEVC. Multimedia Tools Appl. 77(10), 11979–12001 (2017)
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Y. Zhang.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Patel, R., Lad, K., Patel, M. et al. A hybrid DST-SBPNRM approach for compressed video steganography. Multimedia Systems 27, 417–428 (2021). https://doi.org/10.1007/s00530-020-00735-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-020-00735-9