Abstract
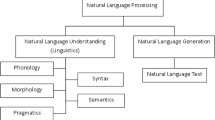
Detecting and tracking events from logging data is a critical element for security and system administrators and thus attracts more and more research efforts. However, there exists a major limitation in current processes of Event Logging analysis, related to the verbosity and language-dependence of messages produced by many logging systems. In this paper, a novel methodology was proposed to tackle this limitation by analysing event messages through a Natural Language Processing task in order to annotate them with semantic metadata. These metadata are further used to enable semantic searches or domain ontology population that help administrator to filter only relevant event and to correlate them for a prompt and efficient response and incident analysis.



Similar content being viewed by others
References
Alicante A, Benerecetti M, Corazza A, Silvestri S (2016) A distributed architecture to integrate ontological knowledge into information extraction. Int J Grid Util Comput 7(4):245–256. https://doi.org/10.1504/IJGUC.2016.081011
Amato F, Moscato F (2015) A model driven approach to data privacy verification in e-health systems. Trans Data Priv 8(3):273–296
Amato F, Moscato F (2016) Pattern-based orchestration and automatic verification of composite cloud services. Comput Electr Eng 56:842–853
Amato F, Moscato F (2017) Exploiting cloud and workflow patterns for the analysis of composite cloud services. Future Gener Comput Syst 67:255–265
Chergui N, Chikhi S, Kechadi T (2017) Semantic grid resource discovery based on skos ontology. Int J Grid Utility Comput (IJGUC) 8(4):269
Leemans M, van der Aalst WMP, van den Brand MGJ (2018a) Recursion aware modeling and discovery for hierarchical software event log analysis. In: 2018 IEEE 25th international conference on software analysis, evolution and reengineering (SANER), pp 185–196. https://doi.org/10.1109/SANER.2018.8330208
Leemans M, van der Aalst WMP, van den Brand MGJ (2018b) The statechart workbench: Enabling scalable software event log analysis using process mining. In: 2018 IEEE 25th international conference on software analysis, evolution and reengineering (SANER), pp 502–506. https://doi.org/10.1109/SANER.2018.8330248
Li T, Jiang Y, Zeng C, Xia B, Liu Z, Zhou W, Zhu X, Wang W, Zhang L, Wu J, Xue L, Bao D (2017) Flap: An end-to-end event log analysis platform for system management. In: Proceedings of the 23rd ACM SIGKDD international conference on knowledge discovery and data mining. ACM, New York, NY, USA, KDD ’17, pp 1547–1556. https://doi.org/10.1145/3097983.3098022
Luh R, Marschalek S, Kaiser M, Janicke H, Schrittwieser S (2017) Semantics-aware detection of targeted attacks: a survey. J Comput Virol Hacking Tech 13(1):47–85
Manning C, Surdeanu M, Bauer J, Finkel J, Bethard S, McClosky D (2014) The stanford corenlp natural language processing toolkit. In: Proceedings of 52nd annual meeting of the association for computational linguistics: system demonstrations, pp 55–60
Sanges G, Aversa R, Tasquier L (2017) An autonomic monitoring framework for iaas cloud applications. Int J Grid Utility Comput (IJGUC) 8(4):330
Xu H, Ding J, Li P, Sgandurra D, Wang R (2018) An improved smurf scheme for cleaning rfid data. Int J Grid Util Comput 9(2):170–178
Zhang J, Huang ML, Hoang D (2013) Visual analytics for intrusion detection in spam emails. Int J Grid Util Comput 4(2–3):178–186
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Amato, F., Cozzolino, G., Mazzeo, A. et al. Detect and correlate information system events through verbose logging messages analysis. Computing 101, 819–830 (2019). https://doi.org/10.1007/s00607-018-0662-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00607-018-0662-1