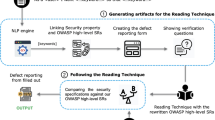
Abstract
More and more software projects today are security-related in one way or the other. Requirements engineers without expertise in security are at risk of overlooking security requirements, which often leads to security vulnerabilities that can later be exploited in practice. Identifying security-relevant requirements is labor-intensive and error-prone. In order to facilitate the security requirements elicitation process, we present an approach supporting organizational learning on security requirements by establishing company-wide experience resources and a socio-technical network to benefit from them. The approach is based on modeling the flow of requirements and related experiences. Based on those models, we enable people to exchange experiences about security-relevant requirements while they write and discuss project requirements. At the same time, the approach enables participating stakeholders to learn while they write requirements. This can increase security awareness and facilitate learning on both individual and organizational levels. As a basis for our approach, we introduce heuristic assistant tools. They support reuse of existing experiences that are relevant for security. In particular, they include Bayesian classifiers that issue a warning automatically when new requirements seem to be security-relevant. Our results indicate that this is feasible, in particular if the classifier is trained with domain-specific data and documents from previous projects. We show how the ability to identify security-relevant requirements can be improved using this approach. We illustrate our approach by providing a step-by-step example of how we improved the security requirements engineering process at the European Telecommunications Standards Institute (ETSI) and report on experiences made in this application.













Similar content being viewed by others
References
Alberts C, Dorofee A (2002) Managing information security risks: the OCTAVE (TM) approach. Addison-Wesley, New York
Allmann C, Winkler L, Kölzow T (2006) The requirements engineering gap in the OEM-supplier relationship. J Univers Knowl Manag 1(2):103–111
Baeza-Yates R, Ribeiro-Neto B (1999) Modern information retrieval. ACM Press, Addison Wesley
Barber B, Davey J (1992) The use of the CCTA risk-analysis and management methodology [CRAMM] in health information systems. In: Degoulet P, Lun KC, Piemme TE, Rienhoff O (eds) MEDINFO ’92, Elsevier, North-Holland, pp 1589–1593
Berry DM, Kamsties E (2004) Perspectives on requirements engineering, chapter 2. Ambiguity in requirements specification. Kluwer, pp 7–44
CEPSCO. Common electronic purse specification (ePurse). http://web.archive.org/web/*/http://www.cepsco.com. Accessed Apr 2007
Chantree F, Nuseibeh B, de Roeck A, Willis A (2006) Identifying Nocuous ambiguities in natural language requirements. In: Proceedings of the 14th IEEE international requirements engineering conference, pp 56–65, Minneapolis, USA, 2006. IEEE Computer Society
Chung L (1993) Dealing with security requirements during the development of information systems. In: Rolland C, Bodart F, Cauvet C (eds) CAiSE, vol 685 of lecture notes in computer science, pp 234–251. Springer
Damian D, Marczak S, Kwan I (2007) Collaboration patterns and the impact of distance on awareness in requirements-centred social networks. In: Proceedings of 15th IEEE international requirements engineering conference (RE 2007), New Delhi, India
De Marco T (1979) Structured analysis and system specification. Prentice-Hall, Englewood Cliffs
den Braber F, Hogganvik I, Lund MS, Stølen K, Vraalsen F (2007) Model-based security analysis in seven steps—a guided tour to the CORAS method. BT Technol J 25(1):101–117
Fischer G (1994) Domain-oriented design environments. Autom Softw Eng 1:177–203
Giorgini P, Massacci F, Mylopoulos J (2003) Requirement engineering meets security: a case study on modelling secure electronic transactions by VISA and mastercard. In: Song I-Y, Liddle SW, Ling TW, Scheuermann P (eds) ER, vol 2813 of lecture notes in computer science. Springer, pp 263–276
Giorgini P, Massacci F, Mylopoulos J, Zannone N (2005) ST-Tool: a CASE tool for security requirements engineering. In: RE ’05: proceedings of the 13th IEEE international conference on requirements engineering, pp 451–452, Washington, DC, USA. IEEE Computer Society
GlobalPlatform. Global platform specification (GPS). http://www.globalplatform.org. Accessed Aug 2010
Höhn S, Jürjens J (2008) Rubacon: automated support for model-based compliance engineering. In: Robby (ed) ICSE, pp 875–878. ACM
Houmb SH, Islam S, Knauss E, Jürjens J, Schneider K (2010) Eliciting security requirements and tracing them to design: an integration of common criteria, heuristics, and UMLsec. Requir Eng J 15(1):63–93
International Standardization Organization (2007) ISO 15408:2007 common criteria for information technology security evaluation, version 3.1, revision 2, CCMB-2007-09-001, CCMB-2007-09-002 and CCMB-2007-09-003, Sept 2007
Ireson N, Ciravegna F, Califf ME, Freitag D, Kushmerick N, Lavelli A (2005) Evaluating machine learning for information extraction. In: ICML ’05: proceedings of the 22nd international conference on machine learning, pp 345–352, Bonn, Germany. ACM
Islam S, Pavlidis M (2011) SecTro: a CASE tool for modelling security in requirements engineering using secure tropos. In: CAiSE ’11: Proceedings of the CAiSE forum 2011, pp 89–96, London. CEUR-WS, vol-734
Jürjens J (2005) Secure systems development with UML. Springer, New York
Jürjens J, Shabalin P (2007) Tools for secure systems development with UML. Int J Softw Tools Technol Transf 9(5):527–544
Jürjens J, Wimmel G (2001) Formally testing fail-safety of electronic purse protocols. In: 16th international conference on automated software engineering (ASE 2001), pp 408–411. IEEE Computer Society
Jürjens J, Schreck J, Bartmann P (2008) Model-based security analysis for mobile communications. In: 30th intern. conference on software engineering (ICSE 2008). ACM
Kelloway KE, Barling J (2000) Knowledge work as organizational behavior. Int J Manag Rev 2:287–304
Kiyavitskaya N, Zeni N, Breaux TD, Antón AI, Cordy JR, Mich L, Mylopoulos J (2008) Automating the extraction of rights and obligations for regulatory compliance. In: Li Q, Spaccapietra S, Yu E, Olivé A (eds) Proceedings of 27th international conference on conceptual modeling, lecture notes in computer science, pp 154–168, Barcelona, Spain. Springer
Kiyavitskaya N, Zeni N, Mich L, Berry DM (2008) Requirements for tools for ambiguity identification and measurement in natural language requirements specifications. Requir Eng J 13(3):207–239
Knauss EW (2010) Verbesserung der Dokumentation von Anforderungen auf Basis von Erfahrungen und Heuristiken. Cuvillier Verlag, Göttingen, Germany. Phd thesis
Knauss E, Flohr T (2007) Managing requirement engineering processes by adapted quality gateways and critique-based RE-Tools. In: Proceedings of workshop on measuring requirements for project and product success, Palma de Mallorca, Spain, November. in conjunction with the IWSM-Mensura conference
Knauss E, Lübke D (2008) Using the friction between business processes and use cases in SOA requirements. In: Proceedings of the 32nd annual IEEE international computer software and applications conference (COMPSAC), workshop on requirements engineering for services, pp 601–606, Turku, Finland
Knauss E, Lübke D, Meyer S (2009) Feedback-driven requirements engineering: the heuristic requirements assistant. In: International conference on software engineering (ICSE’09), formal research demonstrations track, pp 587–590, Vancouver, Canada
Knauss E, Schneider K, Stapel K (2009) Learning to write better requirements through heuristic critiques. In: Proceedings of 17th IEEE requirementes engineering conference (RE 2009), Atlanta, USA
Knauss E, Houmb S, Schneider K, Islam S, Jürjens J (2011) Supporting requirements engineers in recognising security issues. In: Berry D, Franch X (eds) Proceedings of the 17th international working conference on requirements engineering: foundation for software quality (REFSQ ’11), LNCS, Essen, Germany, Springer
Kof L (2005) Text analysis for requirements engineering. PhD thesis, Technische Universität München, München
Lee SK, Muthurajan D, Gandhi RA, Yavagal DS, Ahn G-J (2006) Building decision support problem domain ontology from natural language requirements for software assurance. Int J Softw Eng Knowl Eng 16(6):851–884
Matulevicius R, Mayer N, Mouratidis H, Dubois E, Heymans P, Genon N (2008) Adapting secure tropos for security risk management in the early phases of information systems development. In: Bellahsene Z, Léonard M (eds) CAiSE, vol 5074 of lecture notes in computer science, pp 541–555. Springer
Mellado D, Rodríguez J, Fernández-Medina E, Piattini M (2009) Automated support for security requirements engineering in software product line domain engineering. Availability, reliability and security, international conference on 0:224–231
Moody DL (2009) The "Physics" of notations: toward a scientific basis for constructing visual notations in software engineering. IEEE Trans Softw Eng 35(6):756–779
Mouratidis H, Giorgini P, Manson GA (2003) Integrating security and systems engineering: towards the modelling of secure information systems. In: Eder J, Missikoff M (eds) CAiSE, vol 2681 of lecture notes in computer science, pp 63–78. Springer
Ouedraogo M, Mouratidis H, Khadraoui D, and Dubois E (2010) An agent-based system to support assurance of security requirements. In: SSIRI, pp 78–87. IEEE Computer Society
Polanyi M (1966) The Tacit dimension. Doubleday, Garden City
Russell N, Hofstede AHMt, Aalst WMPvd (2007) newYAWL: specifying a workflow reference language using coloured petri nets. In: Eighth workshop and tutorial on practical use of coloured petri nets and the CPN tools
Schneider K (2005) Software process improvement from a FLOW perspective. In: Learning software organizations workshop, 2005
Schneider K (2007) Generating fast feedback in requirements elicitation. In: Requirements engineering: foundation for software quality (REFSQ 2007)
Schneider K (2009) Experience and knowledge management in software engineering. Springer, Berlin
Schneider K, Lübke D (2005) Systematic tailoring of quality techniques. In: World congress of software quality 2005, vol 3/3
Schneider K, Stapel K, Knauss E (2008) Beyond documents: visualizing informal communication. In: Proceedings of third international workshop on requirements engineering visualization (REV 08), Barcelona, Spain
Schön DA (1983) The reflective practitioner: how professionals think in action. Basic Books, New York
Sindre G, Opdahl AL (2005) Eliciting security requirements with misuse cases. Requir Eng J 10(1):34–44
Stapel K, Schneider K, Lübke D, Flohr T (2007) Improving an industrial reference process by information flow analysis: a case study. In: Proceedings of PROFES 2007, vol 4589 of LNCS, pp 147–159, Riga, Latvia, 2007. Springer, Berlin
Stapel K, Knauss E, Allmann C (2008) Lightweight process documentation: just enough structure in automotive pre-development. In: O’Connor RV, Baddoo N, Smolander K, Messnarz R (eds) Proceedings of the 15th european conference, EuroSPI, communications in computer and information science, pp 142–151, Dublin, Ireland, 9 2008. Springer
Stapel K, Knauss E, Schneider K (2009) Using FLOW to improve communication of requirements in globally distributed software projects. In: Workshop on collaboration and intercultural issues on requirements: communication, understanding and softskills (CIRCUS ’09), Atlanta, USA, Nov 2009
TISPAN, ETSI (2010) Telecommunications and internet converged services and protocols for advanced networking (TISPAN); services requirements and capabilities for customer networks connected to TISPAN NGN. Technical report, European Telecommunications Standards Institute
Weiss SM, Kulikowski CA (1991) Computer systems that learn: classification and prediction methods from statistics, neural nets, machine learning, and expert systems. M. Kaufmann Publishers, San Mateo
Winkler S (2007) Information flow between requirement artifacts. In: Proceedings of REFSQ 2007 international working conference on requirements engineering: foundation for software quality, vol 4542 of lecture notes in computer science, pp 232–246, Trondheim, Norway, 2007. Springer, Berlin
Wise A (2006) Little-JIL 1.5 Language Report. Technical report, Department of Computer Science, University of Massachusetts
Wohlin C, Runeson P, Höst M, Ohlsson MC, Regnell B, Wesslén A (2000) Experimentation in software engineering: an introduction. Kluwer Academic Publishers, Boston
Acknowledgments
This work was partially funded by the German National Science Foundation (DFG InfoFLOW 2008–2011) and the EU project Secure Change (ICT-FET-231101).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Schneider, K., Knauss, E., Houmb, S. et al. Enhancing security requirements engineering by organizational learning. Requirements Eng 17, 35–56 (2012). https://doi.org/10.1007/s00766-011-0141-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00766-011-0141-0