Abstract
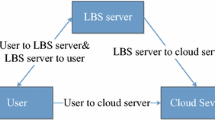
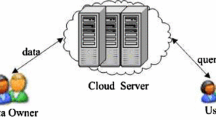
Cloud computing services enable organizations and individuals to outsource the management of their data to a service provider in order to save on hardware investments and reduce maintenance costs. Only authorized users are allowed to access the data. Nobody else, including the service provider, should be able to view the data. For instance, a real-estate company that owns a large database of properties wants to allow its paying customers to query for houses according to location. On the other hand, the untrusted service provider should not be able to learn the property locations and, e.g., selling the information to a competitor. To tackle the problem, we propose to transform the location datasets before uploading them to the service provider. The paper develops a spatial transformation that re-distributes the locations in space, and it also proposes a cryptographic-based transformation. The data owner selects the transformation key and shares it with authorized users. Without the key, it is infeasible to reconstruct the original data points from the transformed points. The proposed transformations present distinct trade-offs between query efficiency and data confidentiality. In addition, we describe attack models for studying the security properties of the transformations. Empirical studies demonstrate that the proposed methods are efficient and applicable in practice.
Similar content being viewed by others
References
Advanced Encryption Standard (AES): NIST—Federal Information Processing Standards Publication 197, Nov (2001)
Agrawal, R., Kiernan, J., Srikant, R., Xu, Y.: Order-preserving encryption for numeric data. In: SIGMOD (2004)
Agrawal, R., Srikant, R.: Privacy-preserving data mining. In: SIGMOD (2000)
Böhm C.: A cost model for query processing in high-dimensional data spaces. ACM TODS 25(2), 129–178 (2000)
Brinkhoff T.: A framework for generating network-based moving objects. GeoInformatica 6(2), 153–180 (2002)
Butz A.R.: Alternative algorithm for Hilbert’s space-filling curve. IEEE Trans. Comput. C-20(4), 424–426 (1971)
Cheng, W., Pang, H., Tan, K.-L.: Authenticating multi-dimensional query results in data publishing. In: DBSec (2006)
Damiani, E., Vimercati, S.D.C., Jajodia, S., Paraboschi, S., Samarati, P.: Balancing confidentiality and efficiency in untrusted relational DBMSs. In: CCS (2003)
Devanbu P., Gertz M., Martel C., Stubblebine S.G.: Authentic data publication over the Internet. J. Comput. Secur. 11(3), 291–314 (2003)
Dwork, C.: Differential privacy: a survey of results. In: TAMC, pp. 1–19 (2008)
Gedik, B., Liu, L.: Location privacy in mobile systems: a personalized anonymization model. In: ICDCS (2005)
Ghinita, G., Kalnis, P., Khoshgozaran, A., Shahabi, C., Tan, K.L.: Private queries in location based services: anonymizers are not necessary. In: SIGMOD (2008)
Ghinita, G., Karras, P., Kalnis, P., Mamoulis, N.: Fast data anonymization with low information loss. In: VLDB (2007)
Goldreich O., Ostrovsky R.: Software protection and simulation on oblivious rams. J. ACM 43, 431–473 (1996)
Gruteser, M., Grunwald, D.: Anonymous usage of location-based services through spatial and temporal cloaking. In: USENIX MobiSys (2003)
Hacigümüs, H., Iyer, B.R., Li, C., Mehrotra, S.: Executing SQL over encrypted data in the database-service-provider model. In: SIGMOD (2002)
Hacigümüs, H., Mehrotra, S., Iyer, B.R.: Providing database as a service. In: ICDE (2002)
Hjaltason G.R., Samet H.: Distance browsing in spatial databases. TODS 24(2), 265–318 (1999)
Kalnis P., Ghinita G., Mouratidis K., Papadias D.: Preventing location-based identity inference in anonymous spatial queries. IEEE TKDE 19(12), 1719–1733 (2007)
Kargupta, H., Datta, S., Wang, Q., Sivakumar, K.: On the privacy preserving properties of random data perturbation techniques. In: ICDM (2003)
Khoshgozaran, A., Shahabi, C.: Blind evaluation of nearest neighbor queries using space transformation to preserve location privacy. In: SSTD (2007)
LeFevre, K., DeWitt, D.J., Ramakrishnan, R.: Mondrian multidimensional k-anonymity. In: ICDE (2006)
Li, N., Li, T., Venkatasubramanian, S.: t-Closeness: privacy beyond k-anonymity and l-diversity. In: ICDE (2007)
Liu K., Kargupta H., Ryan J.: Random projection-based multiplicative data perturbation for privacy preserving distributed data mining. IEEE TKDE 18(1), 92–106 (2006)
Machanavajjhala, A., Gehrke, J., Kifer, D., Venkitasubramaniam, M.: l-Diversity: privacy beyond k-anonymity. In: ICDE (2006)
Merkle, R.C.: A certified digital signature. In: CRYPTO (1989)
Mokbel, M.F., Chow, C.-Y., Aref, W.G.: The new casper: query processing for location services without compromising privacy. In: VLDB (2006)
National Institute of Standards and Technology. Secure Hashing. http://csrc.nist.gov/groups/ST/toolkit/secure_hashing.html
Papadimitriou, S., Li, F., Kollios, G., Yu, P.S.: Time series compressibility and privacy. In: VLDB (2007)
Samarati P.: Protecting respondents’ identities in microdata release. IEEE TKDE 13(6), 1010–1027 (2001)
Stuckmann, P., Ehlers, N., Wouters, B.: GPRS traffic performance measurements. In: IEEE Vehicular Technology Conference (2002)
Theodoridis, Y., Sellis, T.K.: A model for the prediction of R-tree performance. In: PODS (1996)
Weber, R., Schek, H.-J., Blott, S.: A quantitative analysis and performance study for similarity-search methods in high-dimensional spaces. In: VLDB (1998)
Williams, P., Sion, R., Carbunar, B.: Building castles out of mud: practical access pattern privacy and correctness on untrusted storage. In: Proceedings of the ACM Conference on Computer and Communications Security (CCS), pp. 139–148 (2008)
Wong, W.K., Cheung, D.W., Kao, B., Mamoulis, N.: Secure k-NN computation on encrypted databases. In: SIGMOD (2009)
Yang, Y., Papadopoulos, S., Papadias, D., Kollios, G.: Spatial outsourcing for location-based services. In: ICDE (2008)
Yiu, M.L., Ghinita, G., Jensen, C.S., Kalnis, P.: Outsourcing search services on private spatial data. In: ICDE (2009)
Yiu, M.L., Jensen, C.S., Huang, X., Lu, H.: SpaceTwist: Managing the trade-offs among location privacy, query performance, and query accuracy in mobile services. In: ICDE (2008)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yiu, M.L., Ghinita, G., Jensen, C.S. et al. Enabling search services on outsourced private spatial data. The VLDB Journal 19, 363–384 (2010). https://doi.org/10.1007/s00778-009-0169-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00778-009-0169-7