Abstract
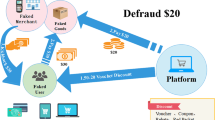
In e-commerce scenarios, frauds events such as telecom fraud, insurance fraud, and fraudulent transactions, bring a huge amount of loss to merchants or users. Identification of fraudsters helps regulators take measures for targeted control. Given a set of fraudsters and suspicious users observed from victims’ reports, how can we effectively distinguish risky users closely related to them from the others for further investigation by human experts? Fraudsters take camouflage actions to hide from being discovered; complex features on users are hard to deal with; patterns of fraudsters are sometimes difficult to explain by human knowledge; and real-world applications involve millions of users. All this makes the question hard to answer. To this end, we design eRiskCom, an e-commerce risky community detection platform to detect risky groups containing identified fraudsters and other closely related users. With the hypothesis that users who interact frequently with fraudsters are more likely to come from the same “risky community,” we construct a connected graph expanded from the identified fraudsters and suspicious users. Next, graph partition is employed to get knowledge of assignment of identified users to potential risky communities, followed by pruning to discover the core members of each community. Finally, top-K users with a high risk score in the neighborhood of core members of each potential community form a final risky community. The extensive experiments are conducted to analyze the effect of our platform components on the alignment with requirements of practical scenarios, and experimental results further demonstrate that eRiskCom is effective and easy to deploy for real-world applications.











Similar content being viewed by others
References
Akbas, E., Zhao, P.: Truss-based community search: a truss-equivalence based indexing approach. Proc. VLDB Endow. 10(11), 1298–1309 (2017)
Akoglu, L., McGlohon, M., Faloutsos, C.: OddBall: spotting anomalies in weighted graphs. In: PAKDD, pp. 410–421 (2010)
Akoglu, L., Tong, H., Koutra, D.: Graph based anomaly detection and description: a survey. DMKD 29, 626–688 (2015)
Barbieri, N., Bonchi, F., Galimberti, E., Gullo, F.: Efficient and effective community searchs. DMKD 29, 1406–1433 (2015)
Batagelj, V., Zaversnik, M.: An O(m) algorithm for cores decomposition of networks. arXiv preprint arXiv:cs/0310049 (2003)
Blondel, V.D., Guillaume, J.L., Lambiotte, R., Lefebvre, E.: Fast unfolding of communities in large networks. J. Stat. Mech. 2008(10), P10008 (2008)
Chang, L., Lin, X., Qin, L., Yu, J.X., Zhang, W.: Index-based optimal algorithms for computing steiner components with maximum connectivity. In: SIGMOD, pp. 459–474 (2015)
Chen, Y.L., Kuo, M.H., Wu, S.Y., Tang, K.: Discovering recency, frequency, and monetary (RFM) sequential patterns from customers’ purchasing data. Electron. Commer. Rec. Appl. 8(5), 241–251 (2009)
Clauset, A.: Finding local community structure in networks. Phys. Rev. E 72, 026132 (2005)
Cohen, J.: Trusses: cohesive subgraphs for social network analysis. Technical report, National Security Agency (2008)
Cook, D.J., Holder, L.B.: Graph-based data mining. IEEE Intell. Syst. Appl. 15(2), 32–41 (2000)
Cui, W., Xiao, Y., Wang, H., Lu, Y., Wang, W.: Online search of overlapping communities. In: SIGMOD, pp. 277–288 (2013)
Cui, W., Xiao, Y., Wang, H., Wang, W.: Local search of communities in large graphs. In: SIGMOD, pp. 991–1002 (2014)
Davis, M., Liu, W., Miller, P., Redpath, G.: Detecting anomalies in graphs with numeric labels. In: CIKM, pp. 1197–1202 (2011)
Derzsy, N., Majumdar, S., Malik, R.: An interpretable graph-based mapping of trustworthy machine learning research. In: Complex Networks XII, pp. 73–85 (2021)
Ding, Q., Katenka, N., Barford, P., Kolaczyk, E., Crovella, M.: Intrusion as (anti)social communication: characterization and detection. In: KDD, pp. 886–894 (2012)
Eberle, W., Holder, L.: Discovering structural anomalies in graph-based data. In: ICDMW, pp. 393–398 (2007)
Ester, M., Kriegel, H.P., Sander, J., Xu, X.: A density-based algorithm for discovering clusters in large spatial databases with noise. In: KDD, pp. 226–231 (1996)
Fang, Y., Cheng, R., Chen, Y., Luo, S., Hu, J.: Effective and efficient attributed community search. VLDB J. 26, 803–828 (2017)
Fang, Y., Huang, X., Qin, L., Zhang, Y., Cheng, R., Lin, X.: A survey of community search over big graphs. VLDB J. 29, 353–392 (2020)
Gibbons, A.: Algorithmic Graph Theory. Cambridge University Press, Cambridge (1985)
Girvan, M., Newman, M.E.: Community structure in social and biological networks. PNAS 99(12), 7821–7826 (2002)
Gupta, M., Mallya, A., Roy, S., Cho, J.H.D., Han, J.: Local learning for mining outlier subgraphs from network datasets. In: SDM, pp. 73–81 (2014)
Hamilton, W., Ying, Z., Leskovec, J.: Inductive representation learning on large graphs. In: NIPS, pp. 1024–1034 (2017)
Hollocou, A., Bonald, T., Lelarge, M.: Multiple local community detection. SIGMETRICS Perform. Eval. Rev. 45(3), 76–83 (2018)
Hooi, B., Shin, K., Song, H.A., Beutel, A., Shah, N., Faloutsos, C.: Graph-based fraud detection in the face of camouflage. ACM TKDD 11(4) (2017)
Hu, J., Wu, X., Cheng, R., Luo, S., Fang, Y.: On minimal steiner maximum-connected subgraph queries. IEEE TKDE 29(11), 2455–2469 (2017)
Huang, Q., Zhou, C., Wu, J., Wang, M., Wang, B.: Deep structure learning for rumor detection on twitter. In: IJCNN, pp. 1–8 (2019)
Huang, X., Cheng, H., Qin, L., Tian, W., Yu, J.X.: Querying k-truss community in large and dynamic graphs. In: SIGMOD, pp. 1311–1322 (2014)
Huang, X., Lakshmanan, L.V.S., Yu, J.X., Cheng, H.: Approximate closest community search in networks. Proc. VLDB Endow. 9(4), 276–287 (2015)
Jiang, M., Beutel, A., Cui, P., Hooi, B., Yang, S., Faloutsos, C.: A general suspiciousness metric for dense blocks in multimodal data. In: ICDM, pp. 781–786 (2015)
Jiang, M., Cui, P., Beutel, A., Faloutsos, C., Yang, S.: Inferring strange behavior from connectivity pattern in social networks. In: PAKDD, pp. 126–138 (2014)
Jurgovsky, J., Granitzer, M., Ziegler, K., Calabretto, S., Portier, P.E., He-Guelton, L., Caelen, O.: Sequence classification for credit-card fraud detection. Expert Syst. Appl. 100, 234–245 (2018)
Kipf, T.N., Welling, M.: Variational graph auto-encoders. In: Bayesian Deep Learning Workshop, NIPS (2016)
Kirlidog, M., Asuk, C.: A fraud detection approach with data mining in health insurance. Procedia Soc. Behav. Sci. 62, 989–994 (2012)
Kleinberg, J.M.: Authoritative sources in a hyperlinked environment. J. ACM 46(5), 604–632 (1999)
Kloumann, I.M., Kleinberg, J.M.: Community membership identification from small seed sets. In: KDD, pp. 1366–1375 (2014)
Kruskal, J.B.: On the shortest spanning subtree of a graph and the traveling salesman problem. Proc. Am. Math. Soc. 7(1), 48–50 (1956)
Lebichot, B., Braun, F., Caelen, O., Saerens, M.: A graph-based, semi-supervised, credit card fraud detection system. In: Complex Networks, pp. 721–733 (2016)
Lempel, R., Moran, S.: SALSA: the stochastic approach for link-structure analysis. ACM TOIS 19(2), 131–160 (2001)
Li, J., Wang, X., Deng, K., Yang, X., Sellis, T., Yu, J.X.: Most influential community search over large social networks. In: ICDE, pp. 871–882 (2017)
Li, X., Liu, S., Li, Z., Han, X., Shi, C., Hooi, B., Huang, H., Cheng, X.: Flowscope: spotting money laundering based on graphs. In: AAAI, pp. 4731–4738 (2020)
Li, Y., He, K., Bindel, D., Hopcroft, J.E.: Uncovering the small community structure in large networks: a local spectral approach. In: WWW, pp. 658–668 (2015)
Liu, F., Wu, J., Xue, S., Zhou, C., Yang, J., Sheng, Q.: Detecting the evolving community structure in dynamic social networks. World Wide Web 23, 715–733 (2020)
Liu, F., Wu, J., Zhou, C., Yang, J.: Evolutionary community detection in dynamic social networks. In: IJCNN, pp. 1–7 (2019)
Liu, F., Xue, S., Wu, J., Zhou, C., Hu, W., Paris, C., Nepal, S., Yang, J., Yu, P.S.: Deep learning for community detection: progress, challenges and opportunities. In: IJCAI, pp. 4981–4987 (2020)
Ma, J., Zhang, D., Wang, Y., Zhang, Y., Pozdnoukhov, A.: GraphRAD: a graph-based risky account detection system. In: MLG (2018)
Ma, X., Wu, J., Xue, S., Yang, J., Zhou, C., Sheng, Q.Z., Xiong, H., Akoglu, L.: A comprehensive survey on graph anomaly detection with deep learning. IEEE TKDE (2021)
Majumdar, S.: Fairness, explainability, privacy, and robustness for trustworthy algorithmic decision making. In: S. Basak, M. Vračko (eds.) Big Data Analytics in Chemoinformatics and Bioinformatics. Elsevier (2022)
Miller, B.A., Beard, M.S., Wolfe, P.J., Bliss, N.T.: A spectral framework for anomalous subgraph detection. IEEE TSP 63(16), 4191–4206 (2015)
Miller, B.A., Bliss, N.T., Wolfe, P.J.: Subgraph detection using eigenvector L1 norms. In: NIPS, pp. 1633–1641 (2010)
Newman, M.E.J.: Fast algorithm for detecting community structure in networks. Phys. Rev. E 69, 066133 (2004)
Newman, M.E.J.: Spectral methods for community detection and graph partitioning. Phys. Rev. E 88, 042822 (2013)
Newman, M.E.J., Girvan, M.: Finding and evaluating community structure in networks. Phys. Rev. E 69, 026113 (2004)
Noble, C.C., Cook, D.J.: Graph-based anomaly detection. In: KDD, pp. 631–636 (2003)
Raghavan, U.N., Albert, R., Kumara, S.: Near linear time algorithm to detect community structures in large-scale networks. Phys. Rev. E 76, 036106 (2007)
Rayana, S., Akoglu, L.: Collective opinion spam detection: bridging review networks and metadata. In: KDD, pp. 98–994 (2015)
Reichardt, J., Bornholdt, S.: Statistical mechanics of community detection. Phys. Rev. E 74, 016110 (2006)
Rosvall, M., Bergstrom, C.T.: Maps of random walks on complex networks reveal community structure. PNAS 105(4), 1118–1123 (2008)
Shin, K., Hooi, B., Faloutsos, C.: Fast, accurate, and flexible algorithms for dense subtensor mining. ACM TKDD 12(3) (2018)
Shrivastava, N., Majumder, A., Rastogi, R.: Mining (social) network graphs to detect random link attacks. In: ICDE, pp. 486–495 (2008)
Sozio, M., Gionis, A.: The community-search problem and how to plan a successful cocktail party. In: KDD, pp. 939–948 (2010)
Su, X., Xue, S., Liu, F., Wu, J., Yang, J., Zhou, C., Hu, W., Paris, C., Nepal, S., Jin, D., Sheng, Q.Z., Yu, P.S.: A comprehensive survey on community detection with deep learning. arXiv preprint arXiv:2105.12584 (2021)
Sun, L., Huang, X., Li, R., Choi, B., Xu, J.: Index-based intimate-core community search in large weighted graphs. IEEE TKDE (2020)
Sun, Q., Li, J., Peng, H., Wu, J., Ning, Y., Yu, P.S., He, L.: SUGAR: subgraph neural network with reinforcement pooling and self-supervised mutual information mechanism. In: WWW, pp. 2081–2091 (2021)
Wang, H., Zhou, C., Wu, J., Dang, W., Zhu, X., Wang, J.: Deep structure learning for fraud detection. In: ICDM, pp. 567–576 (2018)
Wang, L., Zong, B., Ma, Q., Cheng, W., Ni, J., Yu, W., Liu, Y., Song, D., Chen, H., Fu, Y.: Inductive and unsupervised representation learning on graph structured objects. In: ICLR (2020)
Wang, Z., Wang, W., Wang, C., Gu, X., Li, B., Meng, D.: Community focusing: yet another query-dependent community detection. In: AAAI, pp. 329–337 (2019)
Wu, J., Zhu, X., Zhang, C., Yu, P.S.: Bag constrained structure pattern mining for multi-graph classification. IEEE TKDE 26(10), 2382–2396 (2014)
Wu, Y., Jin, R., Li, J., Zhang, X.: Robust local community detection: On free rider effect and its elimination. Proc. VLDB Endow. 8(7), 798–809 (2015)
Yang, D.N., Chen, Y.L., Lee, W.C., Chen, M.S.: On social-temporal group query with acquaintance constraint. Proc. VLDB Endow. 4(6), 397–408 (2011)
Yang, J., Leskovec, J.: Defining and evaluating network communities based on ground-truth. Knowl. Inf. Syst. 42, 181–213 (2015)
Zhang, G., Zhao, L., Huang, J., Wu, J., Zhou, C., Yang, J.: eFraudCom: an e-commerce fraud detection system via competitive graph neural networks. ACM TOIS (2021)
Zhang, Y., Bian, J., Zhu, W.: Trust fraud: a crucial challenge for China’s e-commerce market. Electron. Commer. Rec. Appl. 12(5), 29–308 (2013)
Acknowledgements
This work was supported by the ARC DECRA Project (No. DE200100964). Dr. Li and Dr. Wu are the corresponding authors.
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, F., Li, Z., Wang, B. et al. eRiskCom: an e-commerce risky community detection platform. The VLDB Journal 31, 1085–1101 (2022). https://doi.org/10.1007/s00778-021-00723-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00778-021-00723-z