Abstract
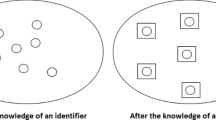
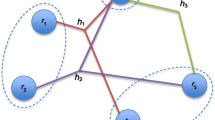
The spread of individuals’ identity information brings about threats of information revealing. Although anonymity could keep individuals’ information from attackers and other unauthorized malicious, at mostly entirely anonymity does not adapt the need of authentication and authorization. To provide the fine-grained ability of privacy preservation, we propose IdRank a reference-based method for rating the importance of identity information objectively and mechanically and provide the implementation of the concrete algorithm. We analyze the result of IdRank and discuss some computing issues of the implementation of IdRank.





Similar content being viewed by others
References
Bhargav-Spantzel A, Squicciarini AC, Bertino E (2005) Establishing and protecting digital identity in federation systems. In: Proceedings of the 2005 workshop on Digital identity management—DIM ’05. ACM Press, New York, pp 11–19, doi:10.1145/1102486.1102489, http://portal.acm.org/citation.cfm?doid=1102486.1102489
Bin X, Anup K, David Z, Ranga R, Bing H (2011) On secure communication in integrated heterogeneous wireless networks. IJITCC 1:4–23, doi:10.1504/IJITCC.2011.039281
Eckersley P (2010) How unique is your web browser? http://panopticlick.eff.org/browser-uniqueness.pdf
Georgina M, Miroslav M, Danco D (2011) Hidden Markov models for classifying protein secondary and tertiary structures. JOC 1:57–64
Haveliwala T (1999) Efficient computation of PageRank. Technical report, Stanford InfoLab, http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.65.3145&rep=rep1&type=pdf
Holt JE, Bradshaw RW, Seamons KE (2003) Hidden credentials. In: Proceedings of the 2003 ACM workshop on Privacy in the electronic society. ACM, New York, doi:http://doi.acm.org/10.1145/1005140.1005142 , http://doi.acm.org/10.1145/1005140.1005142
JaeJung K, DongYoung Y, JinYoung C, SengPhil H (2011) A method of risk assessment for multi-factor authentication. JIPS 7:187–198
Li J, Li N (2006) OACerts: Oblivious Attribute Certificates. IEEE Transactions on Dependable and Secure Computing 3(4):340–352, DOI http://doi.ieeecomputersociety.org/10.1109/TDSC.2006.54, http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=4012646
Li N, Du W, Boneh D (2005) Oblivious signature-based envelope. Distrib Comput pp 293–302, doi:10.1007/s00446-004-0116-1, http://www.springerlink.com/index/2Y6VEJ5BJG08NYYU.pdf
Mohammed A, Chan, Yeob Y, Martin, Thomas A (2011) Ensuring Anonymity for LBSs in Smartphone Environment. JIPS 7:121–136
Page L, Brin S, Motwani R, Terry W (1998) The PageRank citation ranking: bringing order to the web. World Wide Web Internet And Web Information Systems, pp 1–17, http://ilpubs.stanford.edu:8090/422
Sathappan O, Chitra P, Venkatesh P, Prabhu M (2011) Modified genetic algorithm for multiobjective task scheduling on heterogeneous computing system. IJITCC 1:146–158, doi:10.1504/IJITCC.2011.039282
Tong L, Fajiang Y, Yang L, Kong X, Yu Y (2011) Trusted computing dynamic attestation using a static analysis based behaviour model. ACSA 2(1):61–68
Wesley D, Kita MW (1991) Introduction to probability. American Mathematical Society, doi:http://dx.doi.org/10.1016/S1363-4127(97)81322-2, http://www.ncbi.nlm.nih.gov/pubmed/16758893
Winsborough WWH, Li N (2002) Towards practical automated trust negotiation. In: Policies for distributed systems and networks, 2002. Proceedings of third international workshop on, IEEE, pp 92–103, http://ieeexplore.ieee.org/xpls/abs_all.jsp?arnumber=1011297
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Fu, Z., Cao, Y., Wang, J. et al. Reference-based importance assessment model of identity information. Pers Ubiquit Comput 17, 875–882 (2013). https://doi.org/10.1007/s00779-012-0538-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00779-012-0538-x