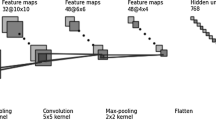
Abstract
This paper deals with a well-known problem in the area of the smudge attacks: when a user draws a pattern to unlock the pattern lock on a smartphone screen, pattern extraction sometimes becomes difficult owing to the existence of the oily residuals around it. This is because the phone screen becomes obscured by these residuals, which significantly lower the guess rate of the pattern lock. To address this, this paper proposes a novel attack method based on a Convolutional Neural Network (CNN). CNNs are known to exhibit high accuracy in image classification. However, using only CNNs for the attack is not sufficient, because there are 389,112 possible patterns, and training the CNN for all the cases is difficult. We therefore propose two ideas to overcome the aforementioned problem. The first one is the application of ’Screen Segmentation,’ where we divide the screen into four segments to reduce the number of possible patterns to 1470 in each segment. The second is the use of pruning rules, which reduces the number of total pattern cases by combining the patterns in each segment. Furthermore, by applying the Android pattern lock constraints, we reduce the number of possible patterns. To validate the proposed idea, we collected 3500 image data by photographing the screen of Android smartphones and generated 367,500 image data based on their possible combinations. Using those data sets, we conducted an experiment whereby we investigated the success rate of our attack in various situations, dealing with different pattern lock lengths and type of prior application usage. The result shows that up to a pattern lock length of seven, the proposed method has on an average, 79% success rate, which is meaningful result in smudge attacks. In addition, in an ideal case where only the actual pattern lock is entered, without oily residuals, the proposed scheme supports an even higher performance, i.e., a 93% successful guess rate on an average.















Similar content being viewed by others
References
Number of Smartphone Users in Advanced and Emerging Economies . https://www.oberlo.com/statistics/how-many-people-have-smartphones. [Online; Accessed 06 Dec 2019]
Alberts, C.J., Dorofee, A.: Managing Information Security Risks: The OCTAVE Approach. Addison-Wesley Longman Publishing Co., Inc., Boston (2002)
Tao, H., Adams, C.: Pass-go: a proposal to improve the usability of graphical passwords. IJ Netw. Sec. 7(2), 273 (2008)
Van Bruggen, D.: Studying the impact of security awareness efforts on user behavior. Ph.D. thesis, University of Notre Dame (2014)
Aviv, A.J., Gibson, K.L., Mossop, E., Blaze, M., Smith, J.M.: Smudge attacks on smartphone touch screens. Woot 10, 1 (2010)
Cha, S., Kwag, S., Kim, H., Huh, J.H.: Boosting the guessing attack performance on android lock patterns with smudge attacks, In: Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security (ACM, 2017), pp. 313–326 (2017)
Andriotis, P., Tryfonas, T., Oikonomou, G.: Complexity metrics and user strength perceptions of the pattern-lock graphical authentication method. International Conference on Human Aspects of Information Security, Privacy, and Trust, pp. 115–126. Springer, New York (2014)
Corning. Mobile users can’t leave their phone alone for six minutes and check it up to 150 times a day. https://www.dailymail.co.uk/news/article-2276752/Mobile-users-leave-phone-minutes-check-150-times-day.html (2013). [Online; Accessed 21 Dec 2020]
Andriotis, P., Tryfonas, T., Oikonomou, G., Yildiz, C.: A pilot study on the security of pattern screen-lock methods and soft side channel attacks. In: Proceedings of the Sixth ACM Conference on Security and Privacy in Wireless and Mobile Networks, pp 1–6. ACM, New York (2013)
LeCun, Y., Boser, B., Denker, J.S., Henderson, D., Howard, R.E., Hubbard, W., Jackel, L.D.: Backpropagation applied to handwritten zip code recognition. Neural Comput. 1(4), 541 (1989)
Behnke, S.: Hierarchical Neural Networks for Image Interpretation, vol. 2766. Springer, New York (2003)
He, K., Zhang, X., Ren, S., Sun, J.: Identity mappings in deep residual networks. In: European Conference on Computer Vision, pp. 630–645. Springer, New York (2016)
Huang, G., Liu, Z., Van Der Maaten, L., Weinberger, K.Q.: Densely connected convolutional networks. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pp. 4700–4708 (2017)
Anand, R., Mehrotra, K., Mohan, C.K., Ranka, S.: Efficient classification for multiclass problems using modular neural networks. IEEE Trans. Neural Netw. 6(1), 117 (1995)
Allwein, E.L., Schapire, R.E., Singer, Y.: Reducing multiclass to binary: a unifying approach for margin classifiers. J. Mach. Learn. Res. 1(Dec), 113 (2000)
Tsoumakas, G., Katakis, I.: Multi-label classification: an overview. Int. J. Data Warehous. Min. (IJDWM) 3(3), 1 (2007)
Lee, H., Kim, S., Kwon, T.: Here is your fingerprint!: Actual risk versus user perception of latent fingerprints and smudges remaining on smartphones. In: Proceedings of the 33rd Annual Computer Security Applications Conference, pp. 512–527. ACM (2017)
Corning. Corning Gorilla Glass 6 Production Information Sheet. https://www.corning.com/microsites/csm/gorillaglass/PI_Sheets/2020/Corning%20Gorilla%20Glass%206_PI%20Sheet.pdf (2018). [Online; Accessed 15 Oct 2020]
Liaro, S.: Why your brand-new smartphone will scratch just as easily as your old one? https://www.theverge.com/circuitbreaker/2018/10/19/17514174/gorilla-glass-scratch-resistance-google-pixel-3- samsung-galaxy-s9-note (2018). [Online; Accessed 15 Oct 2020]
Brookes, T.: How to protect and restore your smartphone’s oleophobic coating. https://www.howtogeek.com/662731/how-to-protect-and-restore-your-smartphones- oleophobic-coating/ (2020). [Online; Accessed 15 Oct 2020]
Amazon Web Service. https://aws.amazon.com/. [Online; Accessed 15 Nov 2019]
Python Library Opencv. https://pypi.org/project/opencv-python/. [Online; Accessed 15 Nov 2019]
Python Library Keras. https://www.tensorflow.org/guide/keras. [Online; Accessed 15 Nov 2019]
Mobile device security. https://www.channelpronetwork.com/article/mobile-device-security-startling-statistics-data -loss-and-data-breaches. [Online; Accessed 15 Nov 2019]
Smartphone theft vulnerability. https://slate.com/technology/2014/12/smartphone-theft-is-a-big-problem-says-fccs -subcommittee-on-mobile-device-theft-prevention.html. [Online; Accessed 15 Nov 2019]
Park, D., Kim, S.: A design and implementation of mobile application usage pattern analysis system. J. Korea Instit. Inf. Commun. Eng. 18(9), 2272 (2014)
Ling, C.X., Huang, J., Zhang, H.: Auc: a better measure than accuracy in comparing learning algorithms. In: Conference of the Canadian Society for Computational Studies of Intelligence, pp. 329–341. Springer, New York (2003)
Liu, Y., Liu, J., Lin, Z., Luo, X., Duan, J.: I know it’s you: Touch behavioral characteristics recognition on smartphone based on pattern password., In PACIS, p. 118 (2015)
Aviv, A.J., Maguire, J., Prak, J.L.: Analyzing the impact of collection methods and demographics for android’s pattern unlock. In: Proceedings of the Workshop on Usable Security (USEC). Internet Society (2016)
Ye, G., Tang, Z., Fang, D., Chen, X.,. Kim, K.I, Taylor, B., Wang, Z.: Cracking android pattern lock in five attempts. In: Proceedings of the 2017 Network and Distributed System Security Symposium 2017 (NDSS 17) (Internet Society, 2017) (2017)
Harbach, M., Von Zezschwitz, E., Fichtner, A., De Luca, A., Smith, M.: It’s a hard lock life: A field study of smartphone (un) locking behavior and risk perception. In: Proceedings of the 10th Symposium on Usable Privacy and Security, pp. 213–230. \(\{\)SOUPS\(\}\) (2014)
Andriotis, P., Tryfonas, T., Yu, Z.: Poster: breaking the android pattern lock screen with neural networks and smudge attacks. In: Proceedings of the Sixth ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec’14) (2014)
Aviv, A.J., Budzitowski, D., Kuber, R.: Is bigger better? comparing user-generated passwords on 3 \(\times \) 3 vs. 4 \(\times \) 4 grid sizes for android’s pattern unlock. In: Proceedings of the 31st Annual Computer Security Applications Conference, pp. 301–310. ACM (2015)
Kwon, T., Na, S.: Tinylock: Affordable defense against smudge attacks on smartphone pattern lock systems. Comput. Sec. 42, 137 (2014)
Higashikawa, S., Kosugi, T., Kitajima, S., Mambo, M.: Shoulder-surfing resistant authentication using pass pattern of pattern lock. IEICE Trans. Inf. Syst. 101(1), 45 (2018)
Amruth, M., Praveen, K.: Intelligent Systems Technologies and Applications, pp. 23–31. Springer, New York (2016)
Guerar, M., Merlo, A., Migliardi, M.: Clickpattern: a pattern lock system resilient to smudge and side-channel attacks. JoWUA 8(2), 64 (2017)
Kim, S., Ku, Y., Kwon, T.: Smudge-based smart device fingerprint authentication attack study. J. Korea Instit. Inf. Sec. Cryptol. 28(5), 1113 (2018)
Abdelrahman, Y., Khamis, M., Schneegass, S., Alt, F.: Stay cool! understanding thermal attacks on mobile-based user authentication. In: Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems, pp. 3751–3763. ACM (2017)
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (No. 2019R1A2C4069769)
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
All procedures performed in studies involving human participants were in accordance with the ethical standards of the institutional and/or national research committee and with the 1964 Helsinki declaration and its later amendments or comparable ethical standards.
Informed consent
Informed consent was obtained from each study participant after they were told of the potential risks and benefits as well as the investigational nature of the study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Shin, H., Sim, S., Kwon, H. et al. A new smart smudge attack using CNN. Int. J. Inf. Secur. 21, 25–36 (2022). https://doi.org/10.1007/s10207-021-00540-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-021-00540-z