Abstract
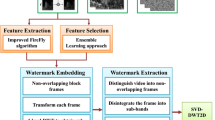
In recent years, we face an increasing interest in protecting multimedia data and copyrights due to the high exchange of information. Attackers are trying to get confidential information from various sources, which brings the importance of securing the data. Many researchers implemented techniques to hide secret information to maintain the integrity and privacy of data. In order to protect confidential data, histogram-based reversible data hiding with other cryptographic algorithms are widely used. Therefore, in the proposed work, a robust method for securing digital video is suggested. We implemented histogram bit shifting based reversible data hiding by embedding the encrypted watermark in featured video frames. Histogram bit shifting is used for hiding highly secured watermarks so that security for the watermark symbol is also being achieved. The novelty of the work is that only based on the quality threshold a few unique frames are selected, which holds the encrypted watermark symbol. The optimal value for this threshold is obtained using the Firefly Algorithm. The proposed method is capable of hiding high-capacity data in the video signal. The experimental result shows the higher capacity and video quality compared to other reversible data hiding techniques. The recovered watermark provides better identity identification against various attacks. A high value of PSNR and a low value of BER and MSE is reported from the results.









Similar content being viewed by others
References
Agilandeeswari L, Ganesan K (2016) A robust color video watermarking scheme based on hybrid embedding techniques. Multimed Tools Appl 75:8745–8780
Alotaibi SS (2020) Optimization insisted watermarking model: hybrid firefly and Jaya algorithm for video copyright protection. Soft Comput. https://doi.org/10.1007/s00500-020-04833-8
Altay SY, Ulutaş G (2021) Self-adaptive step firefly algorithm based robust watermarking method in DWT-SVD domain. Multimed Tools Appl. https://doi.org/10.1007/s11042-020-10251-7
Arab F, Abdullah SM, Hashim SZM, Mana AA, Zamani M (2016) A robust video watermarking technique for the tamper detection of surveillance systems. Multimed Tools Appl 75:10855–10885
Asikuzzaman M, Alam MJ, Lambert AJ, Pickering MR (2016) Robust DT CWT-based DIBR 3D video watermarking using chrominance embedding. IEEE Trans Multimed 18(9):1733–1748
Ayubi P, Barani M, Valandar M, Irani B, Sadigh R (2021) A new chaotic complex map for robust video watermarking. Artif Intell Rev 54(2):1237–1280
Bhardwaj A, Verma VS, Jha RK (2018) Robust video watermarking using significant frame selection based on coefficient difference of lifting wavelet transform. Multimed Tools Appl 77(2018):19659–19678
Cao Z, Wang L (2019) A secure video watermarking technique based on hyperchaotic Lorentz system. Multimed Tools Appl 78(2019):26089–26109
Chang C, Chou YC, Lu TC (2007) A semi-blind watermarking based on discrete wavelet transform. In: International conference on information and communications security, Berlin, Heidelberg
Chuan Q, Wei Z, Fang C, Xinpeng Z, Chin-Chen C (2018) Separable reversible data hiding in encrypted images via adaptive embedding strategy with block selection. Signal Process 153(2018):109–122
Dang C, Radha H (2015) RPCA-KFE: Key frame extraction for video using robust principal component analysis. IEEE Trans Image Process 24(11):3742–3753
Doğan S (2016) A new data hiding method based on chaos embedded genetic algorithm for color image. Artif Intell Rev 46(1):129–143
Ejaz N, Mehmood I, Baik SW (2014) Feature aggregation based visual attention model for video summarization. Comput Electr Eng 40(3):993–1005
Kumar M, Hensman A (2013) Robust digital video watermarking using reversible data hiding and visual cryptography. In: 24th IET Irish signals and systems conference, Ireland
Lu ZM, Guo SZ (2017) Lossless information hiding in images. Syngress
Furini M, Geraci F, Montangero M et al (2010) STIMO: STIll and MOving video storyboard for the web scenario. Multimed Tools Appl 46:47. https://doi.org/10.1007/s11042-009-0307-7
Himeur Y, Boukabou A (2018a) A robust and secure key-frames based video watermarking system using chaotic encryption. Multimed Tools Appl 77:8603–8627
Himeur Y, Boukabou A (2018b) A robust and secure key-frames based video watermarking system using chaotic encryption. Multimed Tools Appl 77(7):8603–8627
Hou J, Ou B, Tian H, Qin Z (2021) Reversible data hiding based on multiple histograms modification and deep neural network. Signal Process Image Commun 92:11618
Huang H-C, Chen Y-H, Abraham A (2010) Optimized watermarking using swarm-based bacterial foraging. J Inf Hiding Multimed Signal Process 1(1):51–58
Jia Y, Yin Z, Zhang X, Luo Y (2019) Reversible data hiding based on reducing invalid shifting of pixels in histogram shifting. Signal Process 163(2019):238–246
Karmakar A, Phadikar A, Phadikar BS, Maity GK (2016) A blind video watermarking scheme resistant to rotation and collusion attacks. J King Saud Univ Comput Inf Sci 28(2):199–210
Katzenbeisser S Petitcolas F (2000) Information hiding techniques for steganography and digital watermarking, United States: information hiding techniques for steganography and digital watermarking
Kulkarni P, Kulkarni G (2018) Visual cryptography based grayscale image watermarking in DWT domain. In: 2018 Second international conference on electronics, communication and aerospace technology (ICECA), Coimbatore, India
Kumar M, Srivastava S, Hensman A (2016) A hybrid novel approach of video watermarking. Int J Signal Process Image Process Pattern Recognit 9(10):395–406
Kumar R, Ki-Hyun J (2020) Robust reversible data hiding scheme based on two-layer embedding strategy. Inf Sci 512:96–107
Li Z, Chen X-W, Ma J (2015) Adaptively imperceptible video watermarking based on the local motion entropy. Multimed Tools Appl 74(2015):2781–2802
Li Y, Yao S, Yang K, Tan Y-A, Zhang Q (2019) A high-imperceptibility and histogram-shifting data hiding scheme for JPEG images. IEEE Access 7:73573–73582
Malik S, Reddlapalli RK (2019) Histogram and entropy based digital image watermarking scheme. Int J Inf Technol 11(2019):373–379
Mishra A, Agarwal C, Sharma A, Bedi P (2014) Optimized gray-scale image watermarking using DWT–SVD and firefly algorithm. Expert Syst Appl 41(17):7858–7867
Mustafa Bilgehan I, Mustafa U, Guzin U (2017) A new reversible database watermarking approach with firefly optimization algorithm. Math Prob Eng. https://doi.org/10.1155/2017/1387375
Nasrullah N, Sang J, Mateen M, Akbar MA, Xiang H, Xia X (2019) Reversible data hiding in compressed and encrypted images by using Kd-tree. Multimed Tools Appl 78:17535–17554
Noor R, Khan A, Sarfaraz A, Mehmood Z, Cheema AM (2019) Highly robust hybrid image watermarking approach using Tchebichef transform with secured PCA and CAT encryption. Soft Comput 23(2019):9821–9829
Rajkumar R, Vasuki A (2019) Reversible and robust image watermarking based on histogram shifting. Clust Comput 22:12313–12323
Rasti P, Samiei S, Agoyi M, Escalera S, Anbarjafari G (2016) Robust non-blind color video watermarking using QR decomposition and entropy analysis. J Vis Commun Image Represent 38(2016):838–847
Senthilnathan T, Prabu P, Sivakumar R, Sakthivel S (2019) An enhancing reversible data hiding for secured data using shuffle block key encryption and histogram bit shifting in cloud environment. Clust Comput 22(2019):12839–12847
Shah M, Zhang W, Hu H, Zhou H, Mahmood T (2018) Homomorphic encryption-based reversible data hiding for 3D mesh models. Arab J Sci Eng 43:8145–8157
Singh TR, Singh KM, Roy S (2013) Video watermarking scheme based on visual cryptography and scene change detection. AEU-Int J Electron C 67(8):645–651
Tang Z, Xu S, Yao H, Qin C, Zhang X (2019) Reversible data hiding with differential compression in encrypted image. Multimed Tools Appl 78(2019):9691–9715
Thakur S, Singh A, Ghrera S, Elhoseny M (2019) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed Tools Appli 78(3):3457–3470
Thanki R, Kothari A, Trivedi D (2019) Hybrid and blind watermarking scheme in DCuT–RDWT domain. J Inf Secur Appl 46:231–249
Wang C, Shan R, Zhou X (2018) Anti-HEVC recompression video watermarking algorithm based on the all phase biorthogonal transform and SVD. IETE Tech Rev 35(2018):42–58
Weng S, Zhang C, Zhang T, Chen K (2021) High capacity reversible data hiding in encrypted images using SIBRW and GCC. J Vis Commun Image Represent 75:102932
Xu D, Chen K, Wang R, Su S (2018) Separable reversible data hiding in encrypted images based on two-dimensional histogram modification. Secur Commun Netw. https://doi.org/10.1155/2018/1734961
Yang X (2009) Nature-inspired metaheuristic algorithms. Luniver press
Youssef SM, ElFarag AA, Ghatwary NM (2014) Adaptive video watermarking integrating a fuzzy wavelet-based human visual system perceptual model. Multimed Tools Appl 73(2014):1545–1573
Zhao J, Li Z (2018) Three-dimensional histogram shifting for reversible data hiding. Multimed Syst 24:95–109
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, M., Aggarwal, J., Rani, A. et al. Secure video communication using firefly optimization and visual cryptography. Artif Intell Rev 55, 2997–3017 (2022). https://doi.org/10.1007/s10462-021-10070-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10462-021-10070-8