Abstract
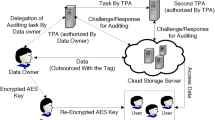
An on-demand computing in which data is stored in a remote manner and provision of services is from a pool of resources of computing that is shared is known as Cloud computing. The cloud computing fulfills the need of store and oversee show. Though to get to and secure information, numerous exceptional advancements like parallel and guide diminish strategies are accessible. The burden of usage from maintenance and storage of native data is eliminated and the owner additionally benefits from elimination of the responsibility of security and storage (Gourkhede and Theng, 2014 fourth international conference on communication systems and network technologies (CSNT), pp 677–680, 2014; Modi, J Supercomput 63(2):561–592, 2013; Smys and Bala, Clust Comput 15(3):211–222, 2012). In order to ensure modification of the accuracy of the on-demand data and its due verification on the cloud owners’ behalf, a methodology that is innovative is needed. The encryption and file split up is done using a novel secure cryptography hashing algorithm. Once the data is uploaded the user is provided with a private and public key for trustworthy retrieval of the data file. Those keys are generated using a proposed modified RSA cryptosystem algorithm. A multilevel hash tree algorithm is used to efficiently audit the data file occasionally. The implementation and therefore the results show the potency and efficiency of the proposed algorithm compared to the existing algorithm.






Similar content being viewed by others
References
Baek, J., Quang, H.V., Liu, J.K., Huang, X., Xiang, Y.: A secure cloud computing based framework for big data information management of smart grid. IEEE Trans. Cloud Comput. 3(2), 233–244 (2015)
Cloud computing wikipedia : https://en.wikipedia.org/wiki/Cloud_computing
Gourkhede, M.H., Theng, D.P.: Analysing security and privacy management for cloud computing environment. 2014 Fourth International Conference on Communication Systems and Network Technologies (CSNT), pp. 677–680 (2014)
Huang, W., Wang, H., Zhang, Y.: A novel cluster computing technique based on signal clustering and analytic hierarchy model using hadoop. In the J. Clust. Comput. ISSN: 1386-7857, pp. 1–8, (2017)
Li, J., Chen, X., Li, M., Li, J., Lee, P., Lou, W.: Secure deduplication with efficient and reliable key management. IEEE Trans. Parallel Distrib. Syst. 25(6), 1615–1626 (2013)
Ma, M., Weber, J., Berg, J.V.D.: Secure public-auditing cloud storage enabling data dynamics in the standard model, IEEE Third International Conference on Digital Information Processing, Data Mining and Wireless Communications, ISBN: 978-1-4673-9379-9 (2016)
Modi, C., et al.: A survey on security issues and solutions at different layers of Cloud computing. J. Supercomput. 63(2), 561–592 (2013)
Sengupta, B., Ruj, S.: Efficient proofs of retrievability with public verifiability for dynamic cloud storage. In IEEE Transactions on Cloud Computing, pp. 1–14 (2017)
Smys, S., Bala, G.J.: Performance analysis of virtual clusters in personal communication networks. Clust. Comput. 15(3), 211–222 (2012)
Smys S, Bala G.J. Raj J.S.: Construction of virtual backbone to support mobility in MANET—a less overhead approach. In the International Conference on Application of Information and Communication Technologies (AICT), IEEE, pp. 1–4 (2009)
Sood, A., Enbody, R.: Targeted cyber attacks-A superset of advanced persistent threats. IEEE Secur. Priv. 11(1), 54–61 (2013)
Subashini, S.: A Survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 34, 1–11 (2011)
Takabi, H., Joshi, J.B., Ahn, G.J.: Security and privacy challenges in cloud computing environments. IEEE Secur. Priv. 8(6), 24–31 (2010)
Thangavel, M., Varalakshmi, P., Kuthalingam, M.: A novel secured cryptographic hash (NSCH) algorithm. In the Proceeding of the International Journal of Engineering Research and Technology (IJERT), Vol. 3 (2014)
Vaquero, L., Rodero-Merino, L., Morán, D.: Locking the sky: a survey on IaaS cloud security. Computing 91(1), 93–118 (2011)
Wang, Q., Wang, C., Li, J., Ren, K., Lou, W.: Enabling public verifiability and data dynamics for storage security in cloud computing. In the Proceeding of ESORICS’09, Vol. 5789 of LNCS. pp. 355–370, Springer (2009)
Wang, C., Wang, Q., Ren, K., Lou, W.: Privacy-preserving public auditing for storage security in cloud computing. In the Proceeding of IEEE INFOCOM’10, (2010)
Wang, C., Ren, K., Lou, W., Li, J.: Towards publicly auditable secure cloud data storage services. IEEE Netw. Mag. 24(4), 19–24 (2010)
Wang, C., Chow, S.S.W., Wang, Q., Ren, K., Lou, W.: Privacy-preserving public auditing for secure cloud storage. IEEE Trans. Comput. 62(2), 362–375 (2013)
Yu, S., Wang, C., Ren, K., Lou, W.:‘ Achieving secure, scalable, and fine-grained access control in cloud computing. In the Proceeding of IEEE INFOCOM’10, San Diego (2010)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Anbuchelian, S., Sowmya, C.M. & Ramesh, C. Efficient and secure auditing scheme for privacy preserving data storage in cloud. Cluster Comput 22 (Suppl 4), 9767–9775 (2019). https://doi.org/10.1007/s10586-017-1486-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-017-1486-z