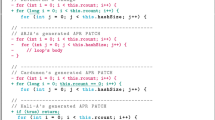
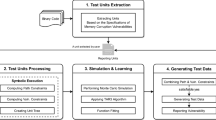
Abstract
This paper presents a dynamic approach to detecting, eliminating and fixing memory leaks. With our approach, a program to be analyzed is instrumented before its execution. Dynamic symbolic execution is employed so as to expose memory leaks occurring in all execution paths. During the program execution, information about each allocated memory area is updated when corresponding statements are executed. Based on this information, a back-end leak checker records the changes of variables pointing to each memory area, detects memory leaks and deallocates leaked memory areas. After the program execution, a fixed program containing deallocation statements is generated. We have implemented our approach in a tool called DEF_LEAK based on Low Level Virtual Machine compiler infrastructure. Experiments show that DEF_LEAK can detect more leaks than the existing dynamic detection tools for programs with user inputs. Moreover, DEF_LEAK is more effective for helping programmers understand and fix memory leaks than other detection tools.






Similar content being viewed by others
Notes
References
Andrzejak A, Eichler F, Ghanavati M (2017) Detection of memory leaks in C/C++ code via machine learning. In: IEEE international symposium on software reliability engineering workshops, IEEE, pp 252–258
Bush WR, Pincus JD, Sielaff DJ (2000) A static analyzer for finding dynamic programming errors. Softw-Pract Exp 30(7):775–802
Cadar C, Engler D (2005) Execution generated test cases: how to make systems code crash itself. In: International SPIN workshop on model checking of software, Springer, pp 2–23
Cadar C, Dunbar D, Engler DR, et al (2008a) KLEE: unassisted and automatic generation of high-coverage tests for complex systems programs. In: USENIX symposium on operating systems design and implementation, pp 209–224
Cadar C, Ganesh V, Pawlowski PM, Dill DL, Engler DR (2008b) EXE: automatically generating inputs of death. ACM Trans Inf Syst Secur 12(2):10:1–10:38
Cherem S, Princehouse L, Rugina R (2007) Practical memory leak detection using guarded value-flow analysis. SIGPLAN Not 42(6):480–491
Chou AC (2003) Static analysis for bug finding in systems software. Ph.D. thesis, Stanford University
Clause J, Orso A (2010) LEAKPOINT: pinpointing the causes of memory leaks. In: ACM/IEEE international conference on software engineering, ACM, pp 515–524
Clause J, Li W, Orso A (2007) Dytan: a generic dynamic taint analysis framework. In: International symposium on software testing and analysis, ACM, pp 196–206
Cui J, Tian C, Zhang N, Duan Z, Du H (2018) Verifying schedulability of tasks in ROS-based systems. J Comb Optim. https://doi.org/10.1007/s10878-018-0328-0
Duan Z (2005) Temporal logic and temporal logic programming. Science Press, Beijing
Evans D (1996) Static detection of dynamic memory errors. SIGPLAN Not 31(5):44–53
Fu C, Chau V, Li M, Xue CJ (2018a) Race to idle or not: balancing the memory sleep time with dvs for energy minimization. J Comb Optim 35(3):860–894
Fu S, Cui B, Guo T, Song X (2018b) C++ memory detection tool based on dynamic instrumentation. In: International conference on emerging internetworking, data & web technologies. Springer, pp 663–674
Gao Q, Xiong Y, Mi Y, Zhang L, Yang W, Zhou Z, Xie B, Mei H (2015) Safe memory-leak fixing for C programs. In: ACM/IEEE international conference on software engineering, IEEE, pp 459–470
Hackett B, Rugina R (2005) Region-based shape analysis with tracked locations. SIGPLAN Not 40(1):310–323
Hastings R, Joyce B (1992) Purify: fast detection of memory leaks and access errors. In: The winter 1992 USENIX conference, Citeseer, pp 125–138
Hauswirth M, Chilimbi TM (2004) Low-overhead memory leak detection using adaptive statistical profiling. SIGPLAN Not 39(11):156–164
Heine DL, Lam MS (2003) A practical flow-sensitive and context-sensitive C and C++ memory leak detector. SIGPLAN Not 38(5):168–181
Insolvibile G (2003) Advanced memory allocation. Linux J 2003(109):7
Joy MM, Rammig FJ (2017) A hybrid methodology to detect memory leaks in soft real-time embedded systems software. Int J Embed Syst 9(1):61–73
Jump M, McKinley KS (2007) Cork: dynamic memory leak detection for garbage-collected languages. SIGPLAN Not 42(1):31–38
Jung Y, Yi K (2008) Practical memory leak detector based on parameterized procedural summaries. In: International symposium on memory management, ACM, pp 131–140
Kim D, Wang W, Li D, Lee JL, Wu W, Tokuta AO (2016) A joint optimization of data ferry trajectories and communication powers of ground sensors for long-term environmental monitoring. J Comb Optim 31(4):1550–1568
Lattner C, Lenharth A, Adve V (2007) Making context-sensitive points-to analysis with heap cloning practical for the real world. SIGPLAN Not 42(6):278–289
Nethercote N, Seward J (2007) Valgrind: a framework for heavyweight dynamic binary instrumentation. SIGPLAN Not 42(6):89–100
Nguyen HH, Rinard M (2007) Detecting and eliminating memory leaks using cyclic memory allocation. In: International symposium on memory management, ACM, pp 15–30
Orlovich M, Rugina R (2006) Memory leak analysis by contradiction. In: International static analysis symposium, Springer, pp 405–424
Shingari D, Arunkumar A, Wu C (2015) Characterization and throttling-based mitigation of memory interference for heterogeneous smartphones. In: IEEE international symposium on workload characterization, IEEE, pp 22–33
Sui Y, Ye D, Xue J (2012) Static memory leak detection using full-sparse value-flow analysis. In: International symposium on software testing and analysis, ACM, pp 254–264
Wang M, Tian C, Zhang N, Duan Z, Du H (2018) Verifying a scheduling protocol of safety-critical systems. J Comb Optim. https://doi.org/10.1007/s10878-018-0343-1
Xie Y, Aiken A (2005) Context-and path-sensitive memory leak detection. In: European software engineering conference held jointly with ACM SIGSOFT international symposium on foundations of software engineering, ACM, pp 115–125
Yang K, Duan Z, Tian C, Zhang N (2018) A compiler for MSVL and its applications. Theor Comput Sci 749:2–16
Zhang N, Duan Z, Tian C (2016a) Model checking concurrent systems with MSVL. Sci China-Inf Sci 59(11):118,101
Zhang N, Yang M, Gu B, Duan Z, Tian C (2016b) Verifying safety critical task scheduling systems in PPTL axiom system. J Comb Optim 31(2):577–603
Zhao JL, He L, He B (2016) C++ memory check tool based on dynamic binary instrumentation platform. In: International conference on broadband and wireless computing, communication and applications. Springer, pp 3–11
Acknowledgements
This research is supported by the National Natural Science Foundation of China Grant Nos. 61420106004, 61732013, 61751207 and 61572386.
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yu, B., Tian, C., Zhang, N. et al. A dynamic approach to detecting, eliminating and fixing memory leaks. J Comb Optim 42, 409–426 (2021). https://doi.org/10.1007/s10878-019-00398-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10878-019-00398-x