Abstract
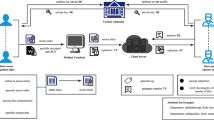
An effectively designed e-healthcare system can significantly enhance the quality of access and experience of healthcare users, including facilitating medical and healthcare providers in ensuring a smooth delivery of services. Ensuring the security of patients’ electronic health records (EHRs) in the e-healthcare system is an active research area. EHRs may be outsourced to a third-party, such as a community healthcare cloud service provider for storage due to cost-saving measures. Generally, encrypting the EHRs when they are stored in the system (i.e. data-at-rest) or prior to outsourcing the data is used to ensure data confidentiality. Searchable encryption (SE) scheme is a promising technique that can ensure the protection of private information without compromising on performance. In this paper, we propose a novel framework for controlling access to EHRs stored in semi-trusted cloud servers (e.g. a private cloud or a community cloud). To achieve fine-grained access control for EHRs, we leverage the ciphertext-policy attribute-based encryption (CP-ABE) technique to encrypt tables published by hospitals, including patients’ EHRs, and the table is stored in the database with the primary key being the patient’s unique identity. Our framework can enable different users with different privileges to search on different database fields. Differ from previous attempts to secure outsourcing of data, we emphasize the control of the searches of the fields within the database. We demonstrate the utility of the scheme by evaluating the scheme using datasets from the University of California, Irvine.



Similar content being viewed by others
References
Microsoft HealthVault (2015) http://www.healthvault.com. Accessed May 1, 2015
Google Health (2013) https://www.google.com/health. Accessed Jan. 1, 2013
Rahman, N. H. A., and Choo, K. R., A survey of information security incident handling in the cloud. Comput. Secur. 49:45–69, 2015. doi:10.1016/j.cose.2014.11.006.
Esposito, C., Castiglione, A., and Choo, K. K. R., Encryption-Based Solution for Data Sovereignty in Federated Clouds. IEEE Cloud Comput. 3(1):12–17, 2016. doi:10.1109/MCC.2016.18.
Nepal, S., Ranjan, R., and Choo, K. K. R., Trustworthy Processing of Healthcare Big Data in Hybrid Clouds. IEEE Cloud Comput. 2(2):78–84, 2015. doi:10.1109/MCC.2015.36.
Choo, K.-K. R., A Conceptual Interdisciplinary Plug-and-Play Cyber Security Framework. In: Kaur, H., and Tao, X. (Eds.), ICTs and the Millennium Development Goals: A United Nations Perspective. Springer US, Boston, MA, pp. 81–99, 2014. doi:10.1007/978-1-4899-7439-6_6.
Choo, K. K. R., and Grabosky, P., Cyber Crime. In: Paoli, L. (Ed.), Oxford Handbook of Organized Crime. Oxford University Press, New York, pp. 482–499, 2013. doi:10.1093/oxfordhb/9780199730445.013.003.
Kim-Kwang, C. R., Cyber threat landscape faced by financial and insurance industry. Trends Issues Crime Crim. Justice 408:1–6, 2011. http://www.aic.gov.au/publications/current%20series/tandi/401-420/tandi408.html .
Congress, U. S., Health Insurance Portability and Accountability Act of. Tabers Cyclopedic Med. Dictionary 2:6, 1996.
Ren, Y., Shen, J., Wang, J., Han, J., and Lee, S., Mutual Verifiable Provable Data Auditing in Public Cloud Storage. J. Internet Technol. 16(2):317–323, 2015.
Ma, T., Zhou, J., Tang, M., Tian, Y., Aldhelaan, A., Alrodhaan, M., and Lee, S., Social Network and Tag Sources Based Augmenting Collaborative Recommender System. IEICE Trans. Inf. Syst. 98(4):902–910, 2015.
Li, L., Lu, R., Choo, K. K. R., Datta, A., and Shao, J., Privacy-Preserving-Outsourced Association Rule Mining on Vertically Partitioned Databases. IEEE Trans. Inf. Forensics Secur. 11(8):1847–1861, 2016. doi:10.1109/TIFS.2016.2561241.
Liu, X., Choo, R., Deng, R., Lu, R., and Weng, J., Efficient and Privacy-Preserving Outsourced Calculation of Rational Numbers. IEEE Trans. Depend. Secure Comput. 2016. doi:10.1109/TDSC.2016.2536601.
Liu, X., Deng, R., Choo, K. K. R., and Weng, J., An Efficient Privacy-Preserving Outsourced Calculation Toolkits with Multiple Keys. IEEE Trans. Inf. Forensics Secur. 11(1):2401–2414, 2016. doi:10.1109/TIFS.2016.2573770.
Xia, Z., Wang, X., Sun, X., and Wang, Q., A Secure and Dynamic Multi-Keyword Ranked Search Scheme over Encrypted Cloud Data. IEEE Trans. Parallel Distrib. Syst. 27(2):340–352, 2016.
Fu, Z., Sun, X., Liu, Q., Zhou, L., and Shu, J., Achieving Efficient Cloud Search Services: Multi-Keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing. IEICE Trans. Commun. E98.B(1):190–200, 2015.
Boneh, D., and Franklin, M., Identity-Based Encryption from the Weil Pairing. In: Kilian, J. (Ed.), Advances in Cryptology — CRYPTO 2001: 21st Annual International Cryptology Conference, Santa Barbara, California, USA, August 19–23, 2001 Proceedings. Springer, Berlin Heidelberg, pp. 213–229, 2001. doi:10.1007/3-540-44647-8_13.
Tep KS, Martini B, Hunt R, Choo KKR A Taxonomy of Cloud Attack Consequences and Mitigation Strategies: The Role of Access Control and Privileged Access Management. In: Trustcom/BigDataSE/ISPA, 2015 IEEE, 20–22 Aug. 2015 2015. pp 1073–1080. doi: 10.1109/Trustcom.2015.485
Sahai, A., and Waters, B., Fuzzy Identity-Based Encryption. In: Cramer, R. (Ed.), Advances in Cryptology – EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, May 22–26, 2005. Proceedings. Springer, Berlin Heidelberg, pp. 457–473, 2005. doi:10.1007/11426639_27.
Bethencourt, J., Sahai, A., and Waters, B., Ciphertext-Policy Attribute-Based Encryption. Sci. Program. 2007. doi:10.1109/SP.2007.11.
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. Paper presented at the Proceedings of the 13th ACM conference on Computer and communications security, Alexandria, Virginia, USA.
Liu, Z., Seo, H., Großschädl, J., and Kim, H., Efficient Implementation of NIST-Compliant Elliptic Curve Cryptography for 8-bit AVR-Based Sensor Nodes. IEEE Trans. Inf. Forensics Secur. 11(7):1385–1397, 2016.
Liu Z, Huang X, Hu Z, Khan MK (2016) On emerging family of elliptic curves to secure internet of things: ECC Comes of Age. IEEE Transactions on Dependable & Secure Computing:1–1
Boldyreva A, Goyal V, Kumar V (2008) Identity-based encryption with efficient revocation. Paper presented at the Proceedings of the 15th ACM conference on Computer and communications security, Alexandria, Virginia, USA.
Ibraimi, L., Petkovic, M., Nikova, S., Hartel, P., and Jonker, W., Ciphertext-Policy Attribute-Based Threshold Decryption with Flexible Delegation and Revocation of User Attributes (extended version). Centre for Telematics and Information Technology. University of Twente, Enschede, 2009.
Yu S, Wang C, Ren K, Lou W (2010) Attribute based data sharing with attribute revocation. Paper presented at the Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, Beijing, China.
Yu, S., Wang, C., Ren, K., and Lou, W., Achieving Secure, Scalable, and Fine-grained Data Access Control in Cloud Computing. Int. Conf. Comput. Commun. 2010. doi:10.1109/INFCOM.2010.5462174.
Ibraimi L, Asim M, Petkovic M (2009) Secure management of personal health records by applying attribute-based encryption. doi:10.1109/PHEALTH.2009.5754828
Akinyele JA, Lehmann CU, Green MD, Pagano MW, Peterson ZNJ, Rubin AD (2010) Self-Protecting Electronic Medical Records Using Attribute-Based Encryption. Faculty Publications 2010
University of California, Irvine. (1990). https://archive.ics.uci.edu/ml/datasets.html.
Acknowledgments
This paper is supported by the National Science Foundation of China under grant No. 61401060, 61501080 and 61572095, the general program of Liaoning Provincial Department of Education Science Research under grants L2014017, and the Fundamental Research Funds for the Central Universities’ under No. DUT16QY09.
Author information
Authors and Affiliations
Corresponding authors
Additional information
This article is part of the Topical Collection on Mobile and; Wireless Health
Rights and permissions
About this article
Cite this article
Guo, C., Zhuang, R., Jie, Y. et al. Fine-grained Database Field Search Using Attribute-Based Encryption for E-Healthcare Clouds. J Med Syst 40, 235 (2016). https://doi.org/10.1007/s10916-016-0588-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0588-0