Abstract
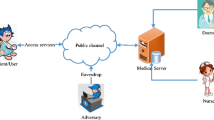
E-Healthcare is an emerging field that provides mobility to its users. The protected health information of the users are stored at a remote server (Telecare Medical Information System) and can be accessed by the users at anytime. Many authentication protocols have been proposed to ensure the secure authenticated access to the Telecare Medical Information System. These protocols are designed to provide certain properties such as: anonymity, untraceability, unlinkability, privacy, confidentiality, availability and integrity. They also aim to build a key exchange mechanism, which provides security against some attacks such as: identity theft, password guessing, denial of service, impersonation and insider attacks. This paper reviews these proposed authentication protocols and discusses their strengths and weaknesses in terms of ensured security and privacy properties, and computation cost. The schemes are divided in three broad categories of one-factor, two-factor and three-factor authentication schemes. Inter-category and intra-category comparison has been performed for these schemes and based on the derived results we propose future directions and recommendations that can be very helpful to the researchers who work on the design and implementation of authentication protocols.




Similar content being viewed by others
References
Khan, F.A., et al.: A cloud-based healthcare framework for security and patients data privacy using wireless body area networks. In: Procedia Computer Science, Vol. 34, pp. 511–517 (2014)
Sun, J., et al., Security and Privacy for Mobile Healthcare (m-Health) Systems, 2011.
Adamsk, T., and Winieck, W.: Entity identification algorithms for distributed measurement and control systems with asymmetry of computational power. In: PRZEGLAD ELEKTROTECHNICZNY, Vol. 84, pp. 216–219 (2008)
Cheng, X.R., and Li, M.X.: The authentication of the grid monitoring system for wireless sensor networks. In: Prz Elektrotechniczn 01a (2013)
Pejaś, J., Fray, I.E., Ruciński, A.: Authentication protocol for software and hardware components in distributed electronic signature creation system. In: Prz Elektrotechniczn 10b (2012)
Lamport, L., Password authentication with insecure communication. Commun. ACM 24(11):770–772, 1981.
Hwang, T., Chen, Y., Laih, C.S.: Non-interactive password authentications without password tables. In: 1990 IEEE Region 10 Conference on Computer and Communication Systems, 1990, IEEE TENCON’90, pp. 429–431 (1990)
Zhang, Y., et al., CADRE: Cloud-assisted drug recommendation service for online pharmacies. Mobile Networks and Applications 20(3):348–355, 2015.
Li, X.-L., et al.: Offline password guessing attacks on smart-card-based remote user authentication schemes. In: Proceedings of the 6th International Asia Conference on Industrial Engineering and Management Innovation, pp. 81–89. Springer (2016)
Schechter, S.E., et al.: Utilization of a protected module to prevent offline dictionary attacks, US Patent App. 15/048,989 (2016)
Alsaleh, M., Mannan, M., van Oorschot, P.C., Revisiting defenses against large-scale online password guessing attacks. IEEE Transactions on dependable and secure computing 9(1):128–141, 2012.
Das, M.L., Saxena, A., Gulati, V.P., A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 50(2):629–631, 2004.
Syverson, P.: A taxonomy of replay attacks [cryptographic protocols]. In: Proceedings of the Computer Security Foundations Workshop VII, 1994, CSFW 7, pp. 187–191. IEEE (1994)
Goyal, P., Parmar, V., Rishi, R., Manet: vulnerabilities, challenges, attacks, application. IJCEM International Journal of Computational Engineering & Management 11(2011):32–37, 2011.
Goyal, P., Batra, S., Singh, A., A literature review of security attack in mobile ad-hoc networks. Int. J. Comput. Appl. 9(12):11–15, 2010.
Salem, M.B., Hershkop, S., Stolfo, S.J.: A survey of insider attack detection research. In: Insider Attack and Cyber Security, pp. 69–90. Springer (2008)
Probst, C.W., Hansen, R.R., Nielson, F.: Where can an insider attack?. In: International Workshop on Formal Aspects in Security and Trust, pp. 127–142. Springer (2006)
Jiang, S., Smith, S., Minami, K.: Securing web servers against insider attack. In: Proceedings 17th Annual Computer Security Applications Conference, 2001. ACSAC 2001, pp. 265–276. IEEE (2001)
Sarkar, A., et al.: Insider attack identification and prevention using a declarative approach. In: 2014 IEEE on Security and Privacy Workshops (SPW), pp. 265–276. IEEE (2014)
Carl, G., et al., Denial-of-service attack-detection techniques. IEEE Internet Computing 10(1):82–89, 2006.
Schuba, C.L., et al.: Analysis of a denial of service attack on TCP. In: Proceedings in the 1997 IEEE Symposium on Security and Privacy, 1997, pp. 208–223. IEEE (1997)
Wood, A.D., and Stankovic, J.A., Denial of service in sensor networks. computer 35(10):54–62, 2002.
Pathan, A.-S.K., Lee, H.-W., Hong, C.S.: Security in wireless sensor networks: issues and challenges. In: 2006 8th International Conference Advanced Communication Technology, Vol. 2, p. 6. IEEE (2006)
Latif, R., et al., EVFDT: an Enhanced Very Fast Decision Tree algorithm for detecting distributed denial of service attack in cloud-assisted wireless body area network. Mob. Inf. Syst,1–13, 2015.
Burg, A.: Ad hoc network specific attacks. In: Seminar Ad hoc networking: Concepts, Applications, and Security. Technische Universitat Munchen,’03 (2003)
Tsuji, T., and Shimizu, A., An impersonation attack on one-time password authentication protocol OSPA. IEICE Trans. Commun. 86(7):2182–2185, 2003.
Tamilselvan, L., and Sankaranarayanan, D.V., Prevention of impersonation attack in wireless mobile ad hoc networks. International Journal of Computer Science and Network Security (IJCSNS) 7(3):118–123, 2007.
Chen, T.-H., and Shih, W.-K., A robust mutual authentication protocol for wireless sensor networks. ETRI J. 32(5):704–712, 2010.
Arshad, H., and Nikooghadam, M., An efficient and secure authentication and key agreement scheme for session initiation protocol using ECC. Multimedia Tools and Applications 75(1):181–197, 2016.
Jiang, Q., et al., Improvement of robust smart-card-based password authentication scheme. Int. J. Commun. Syst. 28(2):383–393, 2015.
Messerges, T.S., Dabbish, E.A., Sloan, R.H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Messerges, T.S., Dabbish, E.A., Sloan, R.H.: Investigations of Power Analysis Attacks on Smartcards. In: Smartcard 99, pp. 151–161 (1999)
Chari, S., et al.: Towards sound approaches to counteract power-analysis attacks. In: Annual International Cryptology Conference, pp. 398–412. Springer (1999)
Messerges, T.S.: Power analysis attacks and countermeasures for cryptographic algorithms, University of Illinois at Chicago (2000)
Li, Y., Chen, M., Wang, J.: Introduction to side-channel attacks and fault attacks. In: 2016 Asia-Pacific International Symposium on Electromagnetic Compatibility (APEMC), Vol. 1, pp. 573–575. IEEE (2016)
Zhu, J., and Ma, J., A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 50(1):231–235, 2004.
Chiou, S.-Y., Ying, Z., Liu, J., Improvement of a privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 40(4):1–15, 2016.
Pfitzmann, A., and Hansen, M.: Anonymity, unlinkability, undetectability, unobservability, pseudonymity, and identity management-a consolidated proposal for terminology. In: Version v0 31, p. 15 (2008)
Pfitzmann, A., and Hansen, M.: A terminology for talking about privacy by data minimization: Anonymity, unlinkability, undetectability, unobservability, pseudonymity, and identity management (2010)
Tseng, Y.-M., Weakness in simple authenticated key agreement protocol. Electron. Lett. 36(1):1, 2000.
Amin, R., and Biswas, G.P., An improved rsa based user authentication and session key agreement protocol usable in tmis. J. Med. Syst. 39(8):1–14, 2015.
Awasthi, A.K., and Lal, S., A remote user authentication scheme using smart cards with forward secrecy. IEEE Trans. Consum. Electron. 49(4):1246–1248, 2003.
Hwang, R.-J., Lai, C.-H., Su, F.-F., An efficient signcryption scheme with forward secrecy based on elliptic curve. Appl. Math. Comput. 167(2):870–881, 2005.
Adrian, D., et al.: Imperfect forward secrecy: How Diffie-Hellman fails in practice. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, pp. 5–17. ACM (2015)
Jau, J.: Password update systems and methods, US Patent App. 11/289,029 (2005)
Islam, S.K.H., and Biswas, G.P., Design of improved password authentication and update scheme based on elliptic curve cryptography. Math. Comput. Model. 57(11):2703–2717 , 2013.
Watanabe, K., et al.: Biometric information processing apparatus and biometric information processing method, US Patent 7,899,21 (2011)
Uludag, U., et al.: cryptosystems: issues and challenges. In: Proceedings of the IEEE, Vol. 92, pp. 948–960 (2004)
Jin, A.T.B., Ling, D.N.C., Goh, A., Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern recogn. 37(11):2245–2255, 2004.
Lumini, A., and Nanni, L., An improved BioHashing for human authentication. Pattern recogn. 40(3): 1057–1065, 2007.
Leng, L., et al., A remote cancelable palmprint authentication protocol based on multi-directional two-dimensional PalmPhasor-fusion. Security and Communication Networks 7(11):1860–1871, 2014.
Leng, L., and Teoh, A.B.J., Alignment-free row-co-occurrence cancelable palmprint fuzzy vault. Pattern Recogn. 48(7):2290–2303, 2015.
Nanni, L., and Lumini, A., Random subspace for an improved biohashing for face authentication. Pattern Recogn. Lett. 29(3):295–300, 2008.
Rivest, R.L., Shamir, A., Adleman, L., A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2):120–126, 1978.
Mainanwal, V., Gupta, M., Upadhayay, S.K.: Zero Knowledge Protocol with RSA Cryptography Algorithm for Authentication in Web Browser Login System (Z-RSA). In: 5th International Conference on Communication Systems and Network Technologies (CSNT), 2015, pp. 776–780. IEEE (2015)
Dolev, D., and Yao, A., On the security of public key protocols. IEEE Trans. Inf. Theory 29(2):198–208, 1983.
Malone-Lee, J., and Mao, W.: Two birds one stone: signcryption using RSA. In: Cryptographers’ Track at the RSA Conference, pp. 211–226. Springer (2003)
Bleichenbacher, D.: Chosen ciphertext attacks against protocols based on the RSA encryption standard PKCS# 1. In: Annual International Cryptology Conference, pp. 1–12. Springer (1998)
Koblitz, N.: Elliptic curve cryptosystems, Vol. 48 (1987)
Miller, V.S.: Use of elliptic curves in cryptography. In: Advances in CryptologyCRYPTO’85 Proceedings, pp. 417–426. Springer (1985)
Aydos, M., Yantk, T., Koc, C.K.: A high-speed ECC-based wireless authentication on an ARM microprocessor. In: 16th Annual Conference on Computer Security Applications, 2000. ACSAC’00, pp. 401–409. IEEE (2000)
Gura, N., Patel, A., Wander, A., Eberle, H., Shantz, S.C.: Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In: International Workshop on Cryptographic Hardware and Embedded Systems, pp. 119–132. Springer (2004)
Gupta, K., and Silakari, S., Ecc over rsa for asymmetric encryption: A review. IJCSI International Journal of Computer Science Issues 8(3), 2011.
Bafandehkar, M.: Comparison of ecc and rsa algorithm in resource constrained devices. In: 2013 International Conference on IT Convergence and Security (ICITCS), pp. 1–3. IEEE (2013)
Savari, M., Montazerolzohour, M., Thiam, Y.E.: Comparison of ECC and RSA algorithm in multipurpose smart card application. In: International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), 2012, pp. 49–53. IEEE (2012)
Woo, T.Y.C., and Lam, S.S., A lesson on authentication protocol design. ACM SIGOPS Operating Systems Review 28(3):24–37, 1994.
Harbitter, A., and Menasce, D.A.: A methodology for analyzing the performance of authentication protocols, Vol. 5 (2002)
Thilagavathi, K., and Rajeswari, P.G., Efficiency and Effectiveness Analysis over ECC-Based Direct and Indirect Authentication Protocols: An Extensive Comparative Study. ICTACT Journal on Communication Technology 3(1):515–524, 2012.
Prasanna, S., and Gobi, M., PERFORMANCE ANALYSIS OF DISTINCT SECURED AUTHENTICATION PROTOCOLS USED IN THE RESOURCE CONSTRAINED PLATFORM. ICTACT Journal on Communication Technology 5(1), 2014.
Agarwal, A.K., and Wang, W.: Measuring performance impact of security protocols in wireless local area networks. In: 2nd International Conference on Broadband Networks, 2005, pp. 581–590. IEEE (2005)
Zhang, Y.: Health-CPS: healthcare cyber-physical system assisted by cloud and big data (2015)
Wu, Z.-Y., et al., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Wei, J., Hu, X., Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Huang, Y.-M., Hsieh, M.-Y., Chao, H.-C., Hung, S.-H., Park, J.H., Pervasive, secure access to a hierarchical sensor-based healthcare monitoring architecture in wireless heterogeneous networks. IEEE journal on selected areas in communications 27(4):400–411, 2009.
González-Valenzuela, S., Chen, M., Leung, V.C.M., Mobility support for health monitoring at home using wearable sensors. IEEE Trans. Inf. Technol. Biomed. 15(4):539–549, 2011.
Hamdi, O., Chalouf, M.A., Ouattara, D., Krief, F., eHealth: Survey on research projects, comparative study of telemonitoring architectures and main issues. J. Netw. Comput. Appl. 46:100–112, 2014.
Sawand, A., et al., Toward energy-efficient and trustworthy eHealth monitoring system. China Communications 12(1):46–65, 2015.
Ng, H.S., Sim, M.L., Tan, C.M., Security issues of wireless sensor networks in healthcare applications. BT Technol. J. 24(2):138–144, 2006.
Egbogah, E.E., and Fapojuwo, A.O.: A survey of system architecture requirements for health care-based wireless sensor networks, Vol. 11 (2011)
Jemal, H., et al., Mobile Cloud Computing in Healthcare System, pp. 408–417: Springer, 2015.
Sajid, A., Abbas, H., Saleem, K., Cloud-Assisted IoT-Based SCADA Systems Security: A Review of the State of the Art and Future Challenges. IEEE Access 4:1375–1384, 2016.
Khan, M.K., Zhang, J., Wang, X., Chaotic hash-based fingerprint biometric remote user authentication scheme on mobile devices. Chaos, Solitons & Fractals 35(3):519–524, 2008.
Zhou, J., et al., Securing m-healthcare social networks: Challenges, countermeasures and future directions. IEEE Wirel. Commun. 20(4):12–21, 2013.
Wu, M., Garfinkel, S., Miller, R., Secure web authentication with mobile phones. DIMACS workshop on usable privacy and security software 2010, 2004.
Kumar, T.R., and Raghavan, S.V.: PassPattern System (PPS): a pattern-based user authentication scheme. In: International Conference on Research in Networking, pp. 162–169. Springer (2008)
Gunson, N., et al., User perceptions of security and usability of single-factor and two-factor authentication in automated telephone banking. Computers & Security 30(4):208–220, 2011.
Adams, A., and Sasse, M.A., Users are not the enemy. Commun. ACM 42(12):40–46, 1999.
Weir, C.S., User perceptions of security, convenience and usability for ebanking authentication tokens. Computers & Security 28(1):47–62, 2009.
Braz, C., and Robert, J.-M.: Security and usability: the case of the user authentication methods. In: Proceedings of the 18th Conference on l’Interaction Homme-Machine, pp. 199–203. ACM (2006)
Koved, L., and Zhang, B.: Improving Usability of Complex Authentication Schemes Via Queue Management and Load Shedding. In: Symposium on Usable Privacy and Security (SOUPS). Citeseer (2014)
Zhang, Y., et al., iDoctor: Personalized and professionalized medical recommendations based on hybrid matrix factorization. Futur. Gener. Comput. Syst., 2016.
Zhang, Y., GroRec: a group-centric intelligent recommender system integrating social, mobile and big data technologies. IEEE Trans. Serv. Comput., 2016.
Shimizu, A., A dynamic password authentication method using a one-way function. Systems and computers in Japan 22(7):32–40, 1991.
Harn, L.: A public-key based dynamic password scheme. In: [Proceedings of the 1991] Symposium on Applied Computing, 1991, pp. 430–435. IEEE (1991)
Steiner, J.G., Neuman, B.C., Schiller, J.I.: Kerberos: An Authentication Service for Open Network Systems. In: USENIX Winter, pp. 191–202 (1988)
Bellovin, S.M., and Merritt, M.: Encrypted key exchange: Password-based protocols secure against dictionary attacks. In: 1992 IEEE Computer Society Symposium on Research in Security and Privacy, 1992. Proceedings, pp. 72–84. IEEE (1992)
Haller, N.: The S/KEY one-time password system (1995)
Gwoboa, H., Password authentication without using a password table. Inf. Process. Lett. 55(5):247–250, 1995.
Chang, C.C., and Wu, T.C.: A password authentication scheme without verification tables. In: 8th IASTED International Symposium of Applied Informatics. Innsbruck, Austria, pp. 202–204 (1990)
Wang, Y.-Y., et al., A more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 32(4):583–585, 2009.
Chan, C.-K., and Cheng, L.-M., Cryptanalysis of a remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(4):992–993, 2000.
Hwang, M.-S., Chang, C.-C., Hwang, K.-F., An ElGamal-like cryptosystem for enciphering large messages. IEEE Trans. Knowl. Data Eng. 14(2):445–446, 2002.
Lee, C.-C., Hwang, M.-S., Yang, W.-P., A flexible remote user authentication scheme using smart cards. ACM SIGOPS Operating Systems Review 36(3):46–52, 2002.
Lee, C.-C., Li, L.-H., Hwang, M.-S., A remote user authentication scheme using hash functions. ACM SIGOPS Operating Systems Review 36(4):23–29, 2002.
Shen, J.-J., Lin, C.-W., Hwang, M.-S., A modified remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 49(2):414–416, 2003.
Sun, H.-M., An efficient remote use authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(4):958–961, 2000.
Khan, M.K., Kim, S.-K., Alghathbar, K., Cryptanalysis and security enhancement of a more efficient & secure dynamic ID-based remote user authentication scheme. Comput. Commun. 34(3):305–309, 2011.
Chen, H.-M., Lo, J.-W., Yeh, C.-K., An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907–3915 , 2012.
Jiang, Q., et al., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37(1):1–8, 2013.
Kumari, S., Khan, M.K., Kumar, R., Cryptanalysis and improvement of a privacy enhanced scheme for telecare medical information systems. J. Med. Syst. 37(4):1–11, 2013.
Debiao, H., Jianhua, C., Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Lee, T.-F., An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. J. Med. Syst. 37(6):1–9, 2013.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6): 3833–3838, 2012.
Das, A.K., and Bruhadeshwar, B., An improved and effective secure password-based authentication and key agreement scheme using smart cards for the telecare medicine information system. J. Med. Syst. 37(5):1–17, 2013.
Xu, X., et al., A Secure and Efficient Authentication and Key Agreement Scheme Based on ECC for Telecare Medicine Information Systems. J. Med. Syst. 38(1):1–7, 2013. issn: 1573-689X.
Islam, S.K.H., and Khan, M.K., Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J. Med. Syst. 38(10):1–16 , 2014.
Chaudhry, S.A., Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J. Med. Syst. 39(6):1–11, 2015.
Zhang, L., Tang, S., Cai, Z., Efficient and flexible password authenticated key agreement for voice over internet protocol session initiation protocol using smart card. Int. J. Commun. Syst. 27(11):2691–2702, 2014.
Jiang, Q., et al., Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. J. Med. Syst. 38(2):1–8 , 2014.
Mishra, D., Srinivas, J., Mukhopadhyay, S., A secure and efficient chaotic map-based authenticated key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(10):1–10, 2014.
Tu, H., et al., An improved authentication protocol for session initiation protocol using smart card. Peer-to-Peer Networking and Applications 8(5):903–910, 2014. issn: 1936-6450.
Chaudhry, S.A., et al., An improved and provably secure privacy preserving authentication protocol for SIP. Peer-to-Peer Networking and Applications,1–15, 2015.
Farash, M.S., Security analysis and enhancements of an improved authentication for session initiation protocol with provable security. Peer-to-Peer Networking and Applications 9(1):82–91, 2016.
Kumari, S., et al., An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Networking and Applications,1–14, 2015.
Wen, F., and Guo, D., An improved anonymous authentication scheme for telecare medical information systems. J. Med. Syst. 38(5):1–11, 2014.
Wen, F., A more secure anonymous user authentication scheme for the integrated EPR information system. J. Med. Syst. 38(5):1–7, 2014.
Xie, Q., Improvement of a uniqueness-and-anonymity-preserving user authentication scheme for connected health care. J. Med. Syst. 38(9):1–10, 2014.
Kocher, P., Jaffe, J., Jun, B., Differential power analysis. Advances in Cryptology—CRYPTO’99,388–397, 1999.
Brier, E., Clavier, C., Olivier, F., Correlation power analysis with a leakage model, pp. 16–29: Springer, 2004.
Gandolfi, K., Mourtel, C., Olivier, F., Electromagnetic analysis: Concrete results, pp. 251–261: Springer, 2001.
Gierlichs, B., et al., Mutual information analysis, pp. 426–442: Springer, 2008.
Kocher, P., et al., Introduction to differential power analysis. Journal of Cryptographic Engineering 1(1):5–27, 2011.
Standaert, F.-X., Malkin, T.G., Yung, M., A unified framework for the analysis of side-channel key recovery attacks, pp. 443–461: Springer, 2009.
Messerges, T.S., Dabbish, E.A., Sloan, R.H., Power analysis attacks of modular exponentiation in smartcards, pp. 144–157: Springer, 1999.
Shiao, D.-R., Chang, Y.-F., Yu, S.-H., A uniqueness-and anonymity- preserving remote user authentication scheme for connected health care. J. Med. Syst.,1–09, 2013.
Das, A.K., and Goswami, A., A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(3):1–16 , 2013.
Kim, K.-W., and Lee, J.-D., On the security of two remote user authentication schemes for telecare medical information systems. J. Med. Syst. 38(5):1–11, 2014.
Wen, F., A Robust Uniqueness-and-Anonymity-Preserving Remote User Authentication Scheme for Connected Health Care. J. Med. Syst.,1–09, 2013.
Xu, L., and Wu, F., Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 39(2):1–9, 2015.
Amin, R., and Biswas, G.P., A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. J. Med. Syst. 39(8):1–19, 2015.
Awasthi, A.K., and Srivastava, K., A biometric authentication scheme for telecare medicine information systems with nonce. J. Med. Syst. 37(5):1–4, 2013.
Tan, Z., A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J. Med. Syst. 38(3):1–9, 2014.
Arshad, H., and Nikooghadam, M., Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(12):1–12 , 2014.
Yan, X., et al., A Secure Biometrics-based Authentication Scheme for Telecare Medicine Information Systems. J. Med. Syst. 37(5):1–6, 2014.
Lu, Y., et al., An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J. Med. Syst. 39(3):1–8, 2015.
Chaudhry, S.A., et al., An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography. J. Med. Syst. 39(11):1–12, 2015.
Mishra, D., et al., Cryptanalysis and improvement of Yan et al.’s biometric-based authentication scheme for telecare medicine information systems. J. Med. Syst. 38(6):1–12, 2014.
Giri, D., et al., An efficient and robust rsa-based remote user authentication for telecare medical information systems. J. Med. Syst. 39(1):1–9, 2015.
Khan, M.K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):1–12, 2013.
Amin, R., and Biswas, G.P., A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. J. Med. Syst. 39(3):1–17, 2015.
Amin, Ruhul and Biswas, GP, Cryptanalysis and design of a three-party authenticated key exchange protocol using smart card. Arab. J. Sci. Eng. 40(11):3135–3149, 2015.
Does HIPAA require two-factor authentication? http://hipaapoliciesandprocedures.com/f-a-q/does-hipaa-require-two-factor-authentication
Authentication, Access Control, and Authorization. https://www.healthit.gov/facas/FACAS/sites/faca/files/Baker_HITSC_PSWG_revisions.pdf, Accessed: 2014-04-24
Identity and Access Management for Health Information Exchange. https://www.healthit.gov/sites/default/files/identitymanagementfinal.pdf, Accessed: 2013-12-15
State and National Trends of Two-Factor Authentication for Non-Federal Acute Care Hospitals. https://www.healthit.gov/sites/default/files/briefs/oncdatabrief32_two-factor_authent_trends.pdf, Accessed: 2015-11-15
Acknowledgment
This Project was funded by the National plan of Science, Technology and Innovation (MAARIFAH), King Abdulaziz City for Science and Technology, Kingdom of Saudi Arabia, Award Number (12-INF2817-02).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Aslam, M.U., Derhab, A., Saleem, K. et al. A Survey of Authentication Schemes in Telecare Medicine Information Systems. J Med Syst 41, 14 (2017). https://doi.org/10.1007/s10916-016-0658-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0658-3