Abstract
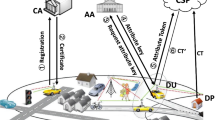
The state-of-the-art research in vehicular network security does not address the need for low latency message access control in vehicular applications with tight connection time and message delay requirements. In existing security solutions, the major limitation is that no trust establishment mechanisms that adapt to rapidly changing scenarios and highly mobile environments (mainly because of key management delay, processing overhead, and changing communication peers). To address this issue, we present a policy management framework for secure data access control in vehicular networks. Our solution address two interrelated research areas to achieve efficiency and scalability for data access control and policy management in highly dynamic vehicular networks. The main contributions are in two-fold: (a) efficient key management and group-based policy enforcement using attribute-based cryptography; and (b) dynamic security policy management framework and methodology to manage credentials based on role, time, location and other situation dependent attributes. Our solution utilizes efficient attribute-based cryptography algorithm to achieve unprecedented speedups in message processing time to meet the real-time requirement. To demonstrate the effectiveness of our proposed solution, a systematic and comprehensive evaluation is produced to valid our proposed solution.









Similar content being viewed by others
Notes
In Appendix 2, we present how to combine static attributes and dynamic attributes using ABE solutions.
References
Hubaux, J., Capkun, S., Luo, S.: The security and privacy of smart vehicles. Secur. Privacy Mag. IEEE 2(3), 49–55 (2004)
Gerlach, M., Festag, A., Leinmuller, T., Goldacker, G., Harsch, C.: Security architecture for vehicular communication. In: Proceedings of the 5th International Workshop on Intelligent Transportation (WIT), March (2007)
Papadimitratos, P., Buttyan, L., Hubaux, J.P., Kargl, F., Kung, A., Raya, M.: Architecture for secure and private vehicular communications. In: Proccedings of the 7th International Conference on ITS Telecommunications (2007)
Doetzer, F.: Privacy issues in vehicular ad hoc networks. In: Proceedings of Workshop on Privacy Enhancing Technologies, Cavtat, Croatia. Springer, Berlin (2005)
Freudiger, J., Raya, M., Félegyházi, M., Papadimitratos, P., Hubaux, J.: Mix-zones for location privacy in vehicular networks. In: Proceedings of WiN-ITS (2007)
Calandriello, G., Hubaux, J., Lioy, A.: Efficient and robust pseudonymous authentication in VANET. In: Proceedings of the Fourth ACM International Workshop on Vehicular ad hoc Networks, pp. 19–28. ACM Press, New York (2007)
Raya, M., Hubaux, J.: Securing vehicular ad hoc networks. J. Comput. Secur. 15(1), 39–68 (2007)
Zhang, C., Lin, X., Lu, R., Ho., P.H.: RAISE: An efficient RSU-aided message authentication scheme in vehicular communication networks. In: Proceedings of IEEE International Conference on Communications (ICC) (2008)
Zhu, H., Lin, X., Lu, R., Ho, P.H., Shen, X.: AEMA: An aggregated emergency message authentication scheme for enhancing the security of vehicular ad hoc networks. In: Proceedings of IEEE International Conference on Communications (ICC) (2008)
Hur, J., Park, C., Yoon, H.: An efficient pre-authentication scheme for IEEE 802.11-based vehicular networks (2007)
Gerlach, M., FOKUS, F.: Trust for vehicular applications. In: Proceedings of the Eighth International Symposium on Autonomous Decentralized Systems (ISADS), pp. 295–304 (2007)
Raya, M., Papadimitratos, P., Aad, I., Jungels, D., Hubaux, J.: Eviction of misbehaving and faulty nodes in vehicular networks. Select. Areas Commun. IEEE J. 25(8), 1557–1568 (2007)
Raya, M., Papadimitratos, P., Gligor, V., Hubaux, J., EPFL, S.: On data-centric trust establishment in ephemeral ad hoc networks. In: Proceedings of IEEE Infocom (2008)
Yan, G., Choudhary, G., Weigle, M., Olariu, S.: Providing VANET security through active position detection. In: Proceedings of VANET’07 (2007)
Boneh, D., Franklin, M.: Identity-based encryption from the Weil pairing. SIAM J. Comput. 32(2), 586–615 (2003)
Goyal, V., Pandey, O., Sahai, A., Waters, B.: Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM Conference on Computer and Communications Security, pp. 89–98. ACM Press, New York (2006)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Bethencourt, J., Sahai, A., Waters, B.: Ciphertext-policy attribute-based encryption. In: Proceedings of the 28th IEEE Symposium on Security and Privacy (Oakland) (2007)
Hong, X., Huang, D., Gerla, M., Cao, Z.: Sat: Building new trust architecture for vehicular networks. In: Proceedings of the 3rd ACM International Workshop on Mobility in the Evolving Internet Architecture (MobiArch) (2008)
Huang, D., Verma, M.: ASPE: Attribute based secure policy enforcement for data access control in vehicular ad hoc networks. Ad Hoc Networks J. (Special Issue of Privacy & Security in WSNs) (2009)
Burns, J., Cheng, A., Gurung, P., Rajagopalan, S., Rao, P., Rosenbluth, D., Surendran, A., Martin Jr, D.: Automatic management of network security policy. In: DARPA Information Survivability Conference and Exposition (DISCEX), vol. 2 (2001)
Dulay, N.D.N.: The ponder policy specification language. In: Lecture Notes in Computer Science. Springer, Berlin, pp. 18–38 (2001)
Hoagland, J., Pandey, R., Levitt, K.: Security policy specification using a graphical approach. Technical Report cs/9809124 (1998)
Mukhi, N., Plebani, P.: Supporting policy-driven behaviors in web services: experiences and issues. In: Proceedings of the 2nd International Conference on Service Oriented Computing, pp. 322–328. ACM, New York (2004)
Paul, R.: DoD towards software services. In: 10th IEEE International Workshop on Object-Oriented Real-Time Dependable Systems (WORDS), pp. 3–6 (2005)
Tsai, W., Wei, X., Paul, R., Chung, J., Huang, Q., Chen, Y.: Service-oriented system engineering (SOSE) and its applications to embedded system development. Service Orient. Comput. Appl. 1(1), 3–17 (2007)
Tsai, W., Zhou, X., Wei, X.: A policy enforcement framework for verification and control of service collaboration. Inf. Syst. E-Bus. Manage. 6(1), 83–107 (2008)
Chadha, R., Cheng, H., Cheng, Y., Chiang, J., Ghetie, A., Levin, G., Tanna, H.: Policy-based mobile ad hoc network management. POLICY (2004)
Chiang, C., Chadha, R., Cheng, Y., Levin, G., Li, S., Poylisher, A., Technologies, T.: A novel software agent framwork with embeded policy control. In: MILCOM, vol. 5, p. 2863 (2005)
Chiang, C., Demers, S., Gopalarishnan, P., Kant, L., Poylisher, A., Cheng, Y., Chadha, R., Levin, G., Li, S., Ling, Y., et al.: Performance analysis of drama: a distributed policy-based system for manet management. In: Military Communications Conference (MILCOM), pp. 1–8 (2006)
Singh, J., Vargas, L., Bacon, J., Moody, K.: Policy-based information sharing in publish/subscribe middleware. In: Policies for Distributed Systems and Networks, 2008. IEEE Workshop on POLICY 2008, pp. 137–144 (2008)
Anastasi, G., Borgia, E., Conti, M., Gregori, E.: Wi-Fi in ad hoc mode: a measurement study. In: Proceedings of IEEE Annual Copnference on Pervasive Computing and Communications (PERCOM), pp. 145–154 (2004)
Cseh, C.: Architecture of the dedicated short-range communications (DSRC) protocol. IEEE Vehicular Technology Conference (VTC) 3, 2095–2099 (1998)
Liu, J., Hong, X., Zheng, Q., Tang, L.: Privacy-preserving quick authentication in fast roaming networks. In: Proceedings of IEEE Conference on Local Computer Networks (LCN). Workshop on Network Security, Tampa, Nov. 14–17 (2006)
Papadimitratos, P., Kung, A., Hubaux, J., Kargl, F.: Privacy and identity management for vehicular communication systems: a position paper. In: Proceedings of Workshop on Standards for Privacy in User-Centric Identity Management, Zurich, Switzerland, July (2006)
Holzmann, G.: The model checker SPIN. IEEE Trans. Softw. Eng. 23(5), 279–295 (1997)
Nii, H.P.; Stanford University: CA Knowledge Systems Lab Blackboard Systems. Department of Computer Science, Stanford University (1986)
Tsai, W., Wei, X., Chen, Y., Paul, R.: A robust testing framework for verifying web services by completeness and consistency analysis. In: IEEE International Workshop on Service-Oriented System Engineering (SOSE), pp. 159–166
Boneh, D., Lynn, B., Shacham, H.: Short signatures from the Weil pairing. In: Proceedings of the Asiacrypt 2001, vol. 2248, pp. 514–532. LNCS (2001)
Sampigethaya, K., Huang, L., Li, M., Poovendran, R., Matsuura, K., Sezaki, K.: CARAVAN: providing location privacy for VANET. In: Proceedings of Embedded Security in Cars (ESCAR) (2005)
Pairing-based cryptography library. http://crypto.stanford.edu/pbc/
Crpto++ library 5.5.2: A free C++ class library of cryptographic schemes. http://www.cryptopp.com/
Saha, A., Johnson, D.: Modeling mobility for vehicular ad-hoc networks. In: Proceedings of the 1st ACM international workshop on Vehicular ad hoc networks, pp. 91–92. ACM, New York (2004)
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: CP-ABE Decrypt Protocol
The cryptographic construction of PGDA is based on CP-ABE. PGDA proposes extensions of CP-ABE for vehicular networks and the system is initialized by using a set of publicly known parameters for vehicle i:
The params i can be stored in vehicle i by the GTA at the time of registration. We use i to represent a unique vehicle ID. The detailed explanation of params is given in Table 3.
The Protocol 4 presents a sketch of Decrypt protocol presented in [18]. To complete the presentation of our solutions, we present the CP-ABE Decrypt protocol in details. For correctness and security proof of CP-ABE scheme, interested readers should refer to [18].
We first define a function \(DecryptNode(\mathcal{CT},\mathcal{SK},x)\) that takes as input a ciphertext \(\mathcal{CT}\), a private key \(\mathcal{SK}\), which is associated with a set \(\mathcal{S}\) of attributes, and a node x from the attribute tree \(\mathcal{T}\). If j is the attribute value of the node x and x is a leaf node, then we can compute the following formulas for vehicle i:
We now consider the recursive case when x is a non-leaf node. The algorithm \(DecryptNode(\mathcal{CT},\mathcal{SK}, x)\) then proceeds as follows: For all nodes z that are children of x, it calls \(DecryptNode(\mathcal{CT}, \mathcal{SK}, z)\) and stores the output as F z . Let \(\mathcal{S}_x\) be an arbitrary k x -sized set of child nodes z such that \(F_z \neq \bot\). If no such set exists then the node was not satisfied and the function returns \(\bot\). Otherwise, compute
where j = index(z) and \(\mathcal{S}_x'=\{{\bf index}(z):z \in \mathcal{S}_x\}\). We define the Lagrange coefficient \(\Updelta_{i,S}\) for \( i \in {\mathbb{Z}}_p \) and a set S, of elements in \({\mathbb{Z}}_p\):
The decryption algorithm begins by calling the DecryptNode function on the root node R of the tree T. If the tree is satisfied by \(\mathcal{S}\) we set \(\zeta = DecryptNode(\mathcal{CT},\mathcal{SK}, R) = e(g, g)^{r_iq_R(0)} = e(g, g)^{r_is}.\) The algorithm decrypts by computing:
Appendix 2: Integration of Policy Trees
The detailed ABE key generation, encryption and decryption algorithms are described in Appendix 9. Here, we just preset how to use them at the functional level to describe our solutions. Using dynamic and static attributes, a vehicle can construct versatile policies.
In Fig. 9, we present the ways to combine static and dynamic attributes, where s tree and d tree represent policy trees formed by static and dynamic attributes, respectively. Combining two trees side-by-side is shown in Fig. 10a. Using XOR operator, we can derive the DEK \(k=k_d\oplus k_s\). In Fig. 10b, c, we present two ways to combine two trees in a top-down fashion. The intersection of two trees is a combined node by integrate a leaf node in the upper tree and the root of the lower tree. In Fig. 10d, we present an example of combining multiple static and dynamic trees. The critical issue of combining multiple trees in a top-down fashion is how to form a combined node from two set of attributes used for different system parameters.
In Fig. 10, we present a method to make a combined node from two policy trees: \(\mathcal{PT}_1\) and \(\mathcal{PT}_2\), where the notations are presented in Table 4 of Appendix 1. The ciphertexts produced by \(\mathcal{PT}_1\) and \(\mathcal{PT}_2\) is presented as follows:
\(\mathcal{CT}_1\) is created by checking if a node in \(\mathcal{PT}_1\) is a combined node. If a node is not a combined node, then the ciphertext component is computed using the normal procedure specified in the Encrypt protocol. If a node is a combined node, then the Encrypt protocol needs to use a masking value k′ (a.k.a., one-time pad) randomly selected to encrypt the ciphertext components C j and C′ j . Once \(\mathcal{CT}_1\) is computed, the Encrypt protocol needs to use the masking value k′ as the encrypted message to construct \(\mathcal{CT}_2\) using a different set of public parameters following the procedure of Encrypt protocol:
Combining \(\mathcal{CT}_1\) and \(\mathcal{CT}_2\), we have the integrated ciphertext:
The decryption procedure is straightforward. A ciphertext receiver first needs to use the Decrypt protocol to decrypt the masking value k′ in \(\mathcal{CT}_2\); and then it performs the following bit-wise XOR operations
to recover the masked values \(\mathcal{C}_j\) and \(\mathcal{C}'_j\) in \(\mathcal{CT}_1\). Finally, the receiver can use Decrypt protocol again to decrypt the DEK encrypted in \(\mathcal{CT}_1\). We must note that the system parameters used in two decryption procedures are different. When there are multiple combined nodes, the above described decryption procedure will be repeated until a message receiver can successfully reach the root and derive the DEK.
Rights and permissions
About this article
Cite this article
Huang, D., Tsai, WT. & Tseng, Yh. Policy Management for Secure Data Access Control in Vehicular Networks. J Netw Syst Manage 19, 448–471 (2011). https://doi.org/10.1007/s10922-010-9197-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10922-010-9197-2