Abstract
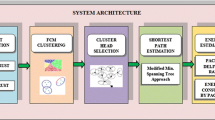
As an important medium of information transmitting, Wireless Sensor Networks (WSN) is at risk of a series of malicious nodes. In view of the inefficiency of the existing malicious node detection methods in Wireless Sensor Networks, this paper proposed a malicious node detection model based on reputation with enhanced low energy adaptive clustering hierarchy (Enhanced LEACH) routing protocol (MNDREL). MNDREL is a novel algorithm, which is aimed at identifying malicious nodes in the wireless sensor network (WSN) more efficiently. Cluster-head nodes are first selected based on the enhanced LEACH routing protocol. Other nodes in WSN then form different clusters by selecting corresponding cluster-head nodes and determine the packets delivery paths. Each node then adds its node number and reputation evaluation value to the packet before sending it to the sink node. A list of suspicious nodes is then formed by comparing the node numbers, obtained through parsing with the packets by the sink node, with the source node numbers. To determine the malicious nodes in the network, the ratio of the suspect value to the trusted value of each node is further calculated and compared with a predefined threshold. The algorithm proposed in this paper, with other two state-of-the-art methods, which are the fuzzy logic based multi-attribute trust model (FMATM) and the high-reliability trust evaluation model (HRTM), are performed and analysed in the same scenario. According to simulation experiments, the MNDREL model is more efficient in detecting malicious nodes in WSN with lower false alarm rate.






Similar content being viewed by others
References
Fahmy HMA (2016) Wireless sensor networks: concepts, applications, experimentation and analysis 1st ed. Springer Publishing Company, Incorporated, Berlin
Gong LY, Wang CD, Yang HY, Li Z, Zhao Z (2018) Fine-grained trust-based routing algorithm for wireless sensor networks. Mobile Netw Appl:1–10. https://doi.org/10.1007/s11036-018-1106-z
Zhang YQ (2013) The study on security problems of wireless sensor networks. Shandong People’s Publishing House, Jinan
Belhajem I, Maissa YB, Tamtaoui A (2018) Improving vehicle localization in a Smart City with low cost sensor networks and support vector machines. Mobile Netw Appl 23(4):854–863
Mukherjee N, Neogy S, Roy S (2016) Building wireless sensor networks: theoretical and practical perspectives. IEEE Wirel Commun 23(2):4–5
Ahmed A, Abubakar K, Channa M, Haseeb K, Khan A (2015) A survey on trust based detection and isolation of malicious nodes in ad-hoc and sensor networks. Front Comput Sci J 9(2):280–296
Prathap U, Shenoy PD, Venugopal KR (2016) CMNTS: catching malicious nodes with trust support in wireless sensor networks. In: 2016 IEEE region 10 symposium (TENSYMP). IEEE, pp 77-82
Althunibat S, Antonopoulos A, Kartsakli E et al (2016) Countering intelligent-dependent malicious nodes in target detection wireless sensor networks. IEEE Sensors J 16(23):8627–8639
Cui H, PAN J, Yan DD (2013) Malicious node detection algorithm based on reputation with voting machanism in wireless sensor networks. J China Jiliang Univ 24(4):353–359
Singh SS, Jinila YB (2016) Sensor node failure detection using check point recovery algorithm. In: 2016 international Conference on Recent Trends in Information Technology (ICRTIT). IEEE, pp 1-4
Varshney KK, Samundiswary P (2014) Performance analysis of malicious nodes in IEEE 802.15.4 based wireless sensor network. In: International Conference on Information Communication and Embedded Systems (ICICES2014). IEEE, pp 1-5
Liu HB, Cui JM, Dai HJ (2011) Multivariate classification-based malicious node detection for wireless sensor network. Chin J Sens and Actuators 24(5):771–777
Das S, Das A (2015) An algorithm to detect malicious nodes in wireless sensor network using enhanced LEACH protocol. In: 2015 International Conference on Advances in Computer Engineering and Applications. IEEE, pp 875-881
Prabha VR, Latha P (2016) Fuzzy trust protocol for malicious node detection in wireless sensor networks. Wirel Pers Commun 94(4):2549–2559
Ma ZF (2016) A study on cluster head selection scheme for LENCH-C in wireless sensor network. Dissertation, Shandong University
Acknowledgements
This research was funded by the Civil Aviation Joint Research Fund Project of National Natural Science Foundation of China under granted number U1833107.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yang, H., Zhang, X. & Cheng, F. A Novel Algorithm for Improving Malicious Node Detection Effect in Wireless Sensor Networks. Mobile Netw Appl 26, 1564–1573 (2021). https://doi.org/10.1007/s11036-019-01492-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01492-4