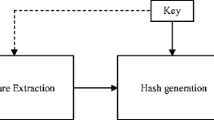
Abstract
Recently, web applications, such as Stock Image and Image Library, are developed to provide the integrated management for user's images. Image hashing techniques are used for the image registration, management and retrieval as the identifier also, investigations have been performed to raise the hash performance like discernment. This paper proposes GLOCAL image hashing method utilizing the hierarchical histogram which is based on histogram bin population method. So far, many studies have proven that image hashing techniques based on this histogram are robust against image processing and geometrical attacks. We modified existing image hashing method developed by our research team [20]. The main idea of the paper is that it helps generate more fluent hash string if we have specific length of histogram bin. Another operation is empowering weighting factor into hash string at each level. Thus, we can raise the magnitude of hash string generated from same context or features and also strengthen the robustness of generated hash.











Similar content being viewed by others
References
Belongie S, Malik J, Puzicha J (2002) Shape matching and object recognition using shape contexts. IEEE Trans Pattern Anal Mach Intell 24(4):509–522
Bhatacherjee S, Kutter M (1998) Compression tolerant image authentication. Proc. IEEE Conf. on Image Processing
Dittman J, Steinmetz A, Steinmetz R (1999) Content based digital signature for motion picture authentication and content fragile watermarking. Proc. IEEE Int. Conf. on Multimedia Computing and Systems, pp 209–213
Fridrich J, Goljan M (2000) Robust hash functions for digital watermarking. Proc. IEEE International Conf. on Information Technology: Coding and Computing, pp 178–183, Mar
Fridrich J, Soukal D, Lukas J (2003) Detection of copymove forgery in digital images. Proceedings of Digital Forensic Research Workshop
Johnson M, Ramchandran K (2003) Dither-based secure image hashing using distributed coding. Proc. IEEE Int. Conf. Image Processing, (Barcelona, Spain), September 2003
Johnson NL, Kotz S, Balakrishnan N (1995) Continuous uni-variate distributions, vol 2. Wiley, New York
Kim HJ, Kim SY, Kim H (2007) A new image hash computation method. International Workshop on Ubiquitous Convergence Technology
Kozat SS, Venkatesan R, Mihcak MK (2004) Robust perceptual image hashing via matrix invariants. Proceedings of International Conference on Image Processing, pp 3443–3446
Lee SH, Kwon KR (2010) Robust 3D hashing algorithm using key-dependent block surface coefficient. Journal of IEEK 47(1):1–14
Lin CY, Chang SF (2001) A robust image authentication system distinguishing JPEG compression from malicious manipulation. IEEE Trans Circuits Syst Video Technol 11(2):153–168
Lowe DG (2004) Distinctive image features from scale-invariant key-points. Int J Comput Vision 60(2):91–110
Lu C-S, Liao H-YM (2003) Structural digital signature for image authentication. IEEE Transactions on Multimedia, pp 161–173, June
Mihcak K, Venkatesan R (2001) New iterative geometric techniques for robust image hashing. Proc. ACM Workshop on Security and Privacy in Digital Rights Management Workshop, pp 13–21, Nov
Mikolajczyk K, Schmid C (2003) A performance evaluation of local descriptors. Proceedings of the computer vision and pattern recognition, pp 257–263
Monga V, Mhcak MK (2005) Robust and secure image hashing via non-negative matrix factorizations. IEEE Trans Inf Forensics Secur 27(3):379–391
Swaminathan A, Mao Y, Wu M (2006) Robust and secure image hashing. IEEE Trans Inf Forensics Secur 1(2):215–230
Tang ZJ, Wang SZ, Zhang XP, Wei WM, Su SJ (2008) Robust image hashing for tamper detection using non-negative matrix factorization. JUCT 2(1):18–26
Venkatesan R, Koon SM, Jakubowski MH, Moulin P (2000) Robust image hashing. Proc. IEEE Conf. on Image Processing, pp 664–666, Sept
Xiang S, Kim HJ, Huang J (2007) Histogram-based image hashing scheme robust against geometric deformations. Proceedings of the ACM Multimedia and Security Workshop, pp 121–128
Acknowledgement
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education, Science and Technology (KRF-2008-331-D00580).
We really thanks researcher who have developed histogram based methods and others. Due to their theorems and results, our method can get valuable performance.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Choi, Y.S., Park, J.H. Image hash generation method using hierarchical histogram. Multimed Tools Appl 61, 181–194 (2012). https://doi.org/10.1007/s11042-010-0724-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-010-0724-7