Abstract
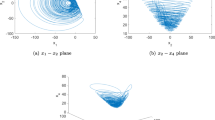
In this paper, a novel algorithm for image encryption based on the hyper-chaotic system is proposed. In order to generate the initial conditions of the hyper-chaotic system, 256-bit long external secret key is used. The algorithm consists of three main sections. In the first section, instead of encrypting each pixel, the rows and columns of the image are encrypted using a row-column algorithm. In order to reach higher sensitivity, higher complexity and higher security, the second section employs masking process which is applied to each quarter of the image (i.e. sub-images) that is to be encrypted, using that sub-image data itself and one of the other sub-images and the average data of other quarters of image. Finally in the last diffusion section, the four most significant bit planes will be encrypted. Experimental results and performance analysis prove the viability of this cryptography based on privacy, integrity and authenticity. It is demonstrated that 2D Correlation Coefficients (CC), Mean Absolute Error (MAE), Encryption Quality (EQ), Mean Square Error (MSE), Peak Signal-to-Noise Ratio (PSNR), the Number of Pixel Change Rate (NPCR), the Unified Average Changing Intensity (UACI), entropy and decryption quality can satisfy security and performance requirements (CC < 0.0032, MAE > 80, EQ > 210.90, MSE > 9555, PSNR < 8.3875, NPCR > 99.61243%, UACI > 33.47573% and Entropy > 7.99734). It can be seen that this algorithm yields better security performance in comparison to the results obtained from other algorithms.

















Similar content being viewed by others
References
Liao X, Lai S, Zhou Q (2010) A novel image encryption algorithm based on self-adaptive wave transmission. J Signal Process 90:2714–2722
Huang CK, Liao CW, Hsu SL, Jeng YC (2011) Implementation of gray image encryption with pixel shuffling and gray-level encryption by single chaotic system. Telecommun Syst. doi:10.1007/s11235-011-9461-0
Fridrich J (1997) Image encryption based on chaotic maps. IEEE Conf Comput Cybern Simul 2:1105–1110
Chen G, Mao Y, Chui CK (2004) A symmetric image encryption scheme based on 3D chaotic cat maps. J Chaos Solitons Fractals 21:749–761
Mao Y, Chen G, Lian S (2004) A novel fast image encryption scheme based on 3D chaotic baker maps. Int J Bifurc Chaos 14(10):3613–3624
Wang Y, Wong KW, Liao X, Xiang T, Chen G (2009) A chaos-based image encryption algorithm with variable control parameters. J Chaos Solitons Fractals 41:1773–1783
Mazloom S, Eftekhari-Moghadam AM (2009) Color image encryption based on coupled nonlinear chaotic map. J Chaos Solitons Fractals 42:1745–1754
Akhshani A, Behnia S, Akhavan A, Hassan HA, Hassan Z (2010) A novel scheme for image encryption based on 2D piecewise chaotic maps. J Opt Commun 283:3259–3266
Seyedzadeh SM, Mirzakuchaki S (2012) A fast color image encryption algorithm based on coupled two dimensional piecewise chaotic map. J Signal Process 92:1202–1215
Mirzaei O, Yaghoobi M, Irani H (2012) A new image encryption method: parallel Sub-image encryption with hyper chaos. J Nonlinear Dyn 67(1):557–566
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. J Opt Commun 285:29–37
Wei X, Guo L, Zhang Q, Zhang J, Lian S (2012) A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J Syst Softw 85(2):290–299
Yen JC, Guo JI (2000) A new chaotic key-based design for image encryption and decryption. Proc IEEE Int Conf Circ Syst 4:49–52
Li S, Zheng X (2002) Cryptanalysis of a chaotic image encryption method. Proc IEEE Symp Circ Syst 2:708–711
Belkhouche F, Qidwai U (2003) Binary image encoding using one-dimensional chaotic map. Proc IEEE Annu Techical Conf :39–43
Lian S, Sun J, Wang Z (2005) Security analysis of a chaos-based image encryption algorithm. Physica A 351:645–661
Li C, Li S, Asim M, Nunez J, Alvarez G, Chen G (2009) On the security defects of an image encryption scheme. J Image Vision Comput 27(9):1371–1381
Nian-Sheng L (2011) Pseudo-randomness and complexity of binary sequences generated by the chaotic system. J Commun Nonlinear Sci Numer Simul 16:761–768
Gao T, Chen Z (2008) A new image encryption algorithm based on hyper-chaos. Phys Lett A 372:394–400
Rhouma R, Belghith S (2008) Cryptanalysis of a new image encryption algorithm based on hyper-chaos. Phys Lett A 372:5973–5978
Ge X, Liu F, Lu B, Yang C (2010) Improvement of Rhouma’s attacks on Gao algorithm. J Phys Lett A 374:1362–1367
Zhang G, Liu Q (2011) A novel image encryption method based on total shuffling scheme. J Opt Commun 284:2775–2780
Akhavan A, Samsudin A, Akhshani A (2011) A symmetric image encryption scheme based on combination of nonlinear chaotic maps. J Frankl Inst 348:1797–1813
Sun F, Liu S, Li Z, Lu Z (2008) A novel image encryption scheme based on spatial chaos map. J Chaos Solitons Fractals 38:631–640
Kwok HS, Tang WKS (2007) A fast image encryption system based on chaotic maps with finite precision representation, Chaos Solitons Fractals 32:1518–1529
Borujeni SE, Eshghi M (2011) Chaotic image encryption system using phase-magnitude transformation and pixel substitution. J Telecommun Syst. doi:10.1007/s11235-011-9458-8
Rössler OE (1976) An equation for continuous chaos original research article, Phys Lett A 57(5):397–398
Norouzi B, Mirzakuchaki S, Seyedzadeh SM, Mosavi MR (2012) A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed Tools Appl. doi:10.1007/s11042-012-1292-9
Norouzi B, Seyedzadeh SM, Mirzakuchaki S, Mosavi MR (2013) A novel image encryption based on hash function with only two-round diffusion process. Multimedia Systems. doi:10.1007/s00530-013-0314-4
Behnia S, Akhshani A, Ahadpour S, Mahmodi H, Akhavan A (2007) A fast chaotic encryption scheme based on piecewise nonlinear chaotic maps. J Phys Lett A 366:391–396
Khanzadi H, Omam MA, Lotfifar F, Eshghi M (2010) Image encryption based on gyrator transform using chaotic maps. IEEE Conf Signal Process :2608–2612
Zhang Q, Guo L, Wei X (2010) Image encryption using DNA addition combining with chaotic maps. J Math Comput Model 52:2028–2035
Zhong Z, Chang J, Shan M, Hao B (2012) Double image encryption using double pixel scrambling and random phase encoding, J Opt Commun 285:584–588
El-Latif AAA, Li L, Niu X (2012) A New image encryption scheme based on cyclic elliptic curve and chaotic system. Multimed Tool Appl. doi:10.1007/s11042-012-1173-2
Sam IS, Devaraj P, Bhuvaneswaran RS (2012) A novel image cipher based on mixed transformed logistic maps. Multimed Tool Appl 56:315–330. doi:10.1007/s11042-010-0652-6
Taneja N, Raman B, Gupta I (2012) Combinational domain encryption for still visual data. Multimed Tool Appl 59:775–793. doi:10.1007/s11042-011-0775-4
Wang K, Pei, Zou L, Song A, He Z (2005) On the security of 3D Cat map based symmetric image encryption scheme. Phys Lett A 343(6):432–439
Lian S (2009) Efficient image or video encryption based on spatiotemporal chaos system. Chaos, Solitons Fractals 40:2509–2519
Rhouma R, Belghith S (2008) Cryptanalysis of a spatiotemporal chaotic image/video cryptosystem. Phys Lett A 372:5790–5794
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24:926–934
Li C, Li S, Asim M, Nunez J, Alvarez G, Chen G (2009) On the security defects of an image encryption scheme. Image Vis Comput 27:1371–1381
Patidar V, Pareek NK, Sud KK (2009) A new substitution-diffusion based image cipher using chaotic standard and logistic maps. Commun Nonlinear Sci Numer Simul 14:3056–3075
Rhouma R, Solak E, Belghith S (2010) Cryptanalysis of a new substitution–diffusion based image cipher. Commun Nonlinear Sci Numer Simul 15:1887–1892
Patidar V, Pareek NK, Purohit G, Sud KK (2010) Modified substitution-diffusion image cipher using chaotic standard and logistic maps. Commun Nonlinear Sci Numer Simul 15:2755–2765
Li C, Li S, Lo K-T (2011) Breaking a modified substitution-diffusion image cipher based on chaotic standard and logistic maps. Commun Nonlinear Sci Numer Simul 16:837–843
Wang X, Liu L (2013) Cryptanalysis of a parallel sub-image encryption method with high-dimensional chaos. Nonlinear Dyn 73:795–800
Zhu C, Liao C, Deng X (2013) Breaking and improving an image encryption scheme based on total shuffling scheme. Nonlinear Dyn 71:25–34
Wang XY, Yang L, Liu R, Kadir A (2010) A chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn 62(3):615–621
Zhang Y, Li C, Li Q, Zhang D, Shu S (2012) Breaking a chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn 69:1091–1096
Li C, Liu Y, Xie T, Chen M (2013) Breaking a novel image encryption scheme based on improved hyperchaotic sequences. Nonlinear Dyn. doi:10.1007/s11071-013-0924-6
Ye G, Wong K-W (2013) An image encryption scheme based on time-delay and hyperchaotic system. Nonlinear Dyn 71:259–267
Huang X, Ye G (2013) An image encryption algorithm based on hyper-chaos and DNA sequence. Multimed Tools Appl. doi:10.1007/s11042-012-1331-6
Liu F, Koenig H (2012) Puzzle - an efficient, compression independent video encryption algorithm. Multimed Tools Appl. doi:10.1007/s11042-012-1185-y
Amin M, Faragallah OS, El-Latif AAA (2010) A chaotic block cipher algorithm for image cryptosystems. J Commun Nonlinear Sci Numer Simul 15(11):3484–3497
Zhu ZL, Zhang W, Wong KW, Yu H (2011) A chaos-based symmetric image encryption scheme using a Bit-level permutation. J Inform Sci 181:1171–1186
Gao T, Chen Z (2008) Image encryption based on a new total shuffling algorithm. J Chaos Solitons Fractals 38:213–220
Huang R, Rhee KH, Uchida S (2012) A parallel image encryption method based on compressive sensing. Multimed Tools Appl. doi:10.1007/s11042-012-1337-0
Acknowledgments
The authors would like to thank the Editor, the anonymous Referees, and Miss Shirin Saberian for their valuable comments and suggestions to improve this paper.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Norouzi, B., Seyedzadeh, S.M., Mirzakuchaki, S. et al. A novel image encryption based on row-column, masking and main diffusion processes with hyper chaos. Multimed Tools Appl 74, 781–811 (2015). https://doi.org/10.1007/s11042-013-1699-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1699-y