Abstract
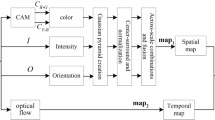
This paper proposes a video watermarking scheme based on visual saliency and secret sharing, which can be used for both synchronous authentication and copyright protection. Firstly, video is divided into several different scenes, and region of interest (ROI) for each I frames would be extracted automatically using the proto-object based saliency attention model. Secondly, the robust watermark and fragile watermark are generated according to ROI. The robust watermark is synthesized by copyright information and ROI of the first I frame for each video scene, and the edge map of ROI in each I frame is chosen as the fragile watermark. Finally, the robust watermark and fragile watermark are embedded into I frames of video scenes so that it can achieve video authentication and copyright information simultaneously. Experimental results demonstrate that the proposed method is robust to recompression and frame attack, and is also sensitive to tamper at the same time.














Similar content being viewed by others
References
Blakley G (1979) Safeguarding cryptographic keys. Proceedings of the National Computer Conference 48:313–317
Itti L, Koch C, Niebur E (1998) A model of saliency-based visual attention for rapid scene analysis. IEEE Transactions on Pattern Analysis and Machine Intelligence 20(11):1254–1259
Koz A, Alatan AA (2008) Oblivious Spatio-Temporal Watermarking of Digital Video by Exploiting the Human Visual System. IEEE Transactions on Circuits and Systems for Video Technology 18(3):326–33
Kuo TY, Lo YC (2010) A hybrid scheme of robust and fragile watermarking for H.264/AVC video. IEEE International Symposium on Broadband Multimedia Systems and Broadcasting, 1-6
Li CT (2004) Digital fragile watermarking scheme for authentication of JPEG images. IEE Proc Vision Image Signal Process 151(6):460–466
Lin YR, Huang HY, Hsu WH (2006) An embedded watermark technique in video for copyright protection. 18th International Conference on Pattern Recognition 4:795–798
Lin PY, Lee JS, Chang CC (2009) Dual Digital Watermarking for Internet Media Based on Hybrid Strategies. IEEE Transactions on Circuits and Systems for Video Technology 19(8):1169–1171
Lin CC, Tsai WH (2004) Secret image sharing with steganography and authentication. Journal of Systems and Software 73(3):405–414
Liu HM, Zhu L, J.W. Huang (2006) A Hybrid Watermarking Scheme for Video Authentication. IEEE International Conference on Image Processing, 2569-2572
Mansouri A, Aznaveh AM, Torkamani F et al (2010) A Low Complexity Video Watermarking in H.264 Compressed Domain. IEEE Transactions on Information Forensics and Security 5(4):649–657
Park SW, Shin SU (2011) Authentication and Copyright Protection Scheme for H.264/AVC and SVC. Journal of Information Science and Engineering 27:129–142
Qin C, Chang CC, Chen PY (2012) Self-Embedding Fragile Watermarking with Restoration Capability Based on Adaptive Bit Allocation Mechanism. Signal Processing 92(4):1137–1150
Qin C, Chang CC, Chen KN (2013) Adaptive Self-recovery for Tampered Images Based on VQ Indexing and Inpainting. Signal Processing 93(4):933–946
Qiu G, Marziliano P, Ho ATS et al (2004) A hybrid watermarking scheme for H.264/AVC video. Proceedings of the 17th International Conference on Pattern Recognition 4:865–868
Shamir A (1979) How to share a secret. ACM Communicaions 22(11):612–613
Thien CC, Lin JC (2002) Secret image sharing. Computers & Graphics 26(5):765–770
Walther D, Koch C (2006) Modeling attention to salient proto-objects. Neural Networks 19(9):1395–1407
Wang CC, Hsu YC (2010) Fragile watermarking scheme for H.264 video authentication. Optical Engineering 49(2):027003
Wang RD, Li Q, Zhu HL et al (2012) Fragile watermarking scheme suitable for the authentication of H.264/AVC video content. Journal of Information and Computational Science 9(13):3693–3706
Wang RZ, Su CH (2006) Secret image sharing with smaller shadow images. Pattern Recognition Letters 27(6):551–555
Xu DW, Wang RD, Wang JC (2009) Blind Digital Watermarking of Low Bit-Rate Advanced H.264/AVC Compressed Video Digital Watermarking. Digital Watermarking, Springer Berlin / Heidelberg 5703:96–109
Zhang XP, Wang SZ, Qian ZX, Feng GR (2011) Reference Sharing Mechanism for Watermark Self-Embedding. IEEE Transactions on Image Processing 20(2):485–495
Zhong WD, Wu GR, Niu K et al. (2011) An improved hybrid video watermarking scheme. IEEE 3rd International Conference on Communication Software and Networks, 364-367
Acknowledgements
This work was supported in part by the National Basic Research Program of China(973 Program) under Grant No. 2012CB316400, the National Natural Science Foundation of China under Grant No.61075007 and the Natural Science Foundation Research Plan of Shaanxi Province of China under Grant No.11JK0900.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tian, L., Zheng, N., Xue, J. et al. Authentication and copyright protection watermarking scheme for H.264 based on visual saliency and secret sharing. Multimed Tools Appl 74, 2991–3011 (2015). https://doi.org/10.1007/s11042-013-1765-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1765-5