Abstract
With the evolution in cloud computing, cloud-based volume rendering, which outsources data rendering tasks to cloud datacenters, is attracting interest. Although this new rendering technique has many advantages, allowing third-party access to potentially sensitive volume data raises security and privacy concerns. In this paper, we address these concerns for cloud-based pre-classification volume ray-casting by using Shamir’s (k, n) secret sharing and its variant (l, k, n) ramp secret sharing, which are homomorphic to addition and scalar multiplication operations, to hide color information of volume data/images in datacenters. To address the incompatibility issue of the modular prime operation used in secret sharing technique with the floating point operations of ray-casting, we consider excluding modular prime operation from secret sharing or converting the floating number operations of ray-casting to fixed point operations – the earlier technique degrades security and the later degrades image quality. Both these techniques, however, result in significant data overhead. To lessen the overhead at the cost of high security, we propose a modified ramp secret sharing scheme that uses the three color components in one secret sharing polynomial and replaces the shares in floating point with smaller integers.










Similar content being viewed by others
References
AlZain MA, Pardede E, Soh B, Thom JA (2012) Cloud computing security: From single to multi-clouds. In: Proceedings of the 45th Hawaii International Conference on System Sciences Hawaii, pp 5490–5499
Benaloh JC (1987) Secret sharing homomorphisms: Keeping shares of a secret secret. In: Proceedings of the Advances in Cryptology–CRYPTO’87, Sanata Barbara, pp 31–36
Catrina O, Saxena A (2010) Secure computation with fixed-point numbers. In: Proceedings of the 14th international conference on financial cryptography and data security, Tenerife, pp 35–50
Chor B, Kushilevitz E (1993) Secret sharing over infinite domains. J Cryptol 6:87–95
Cooper J, Donovan D, Seberry J (1994) Secret sharing schemes arising from Latin sqaures. Bull Inst Comb Appl 12:33–43
Dorn K, Ukis V, Friese T (2011) A cloud-deployed 3D medical imaging system with dynamically optimized scalability and cloud costs. In: Proceedings of the 37th EUROMICRO conference on software engineering and advanced applications, Oulu, pp 155–158
Fellgiebel A, Müller MJ, Wille P et al (2005) Color-coded diffusion-tensor-imaging of posterior cingulate fiber tracts in mild cognitive impairment. Neurobiol Aging 6:1193–1198
Finamore T (2012) Shamir’s secret sharing scheme using floating point arithmetic. Master Thesis, Florida Atlantic University
Harn L, Changlu L (2010) Authenticated group key transfer protocol based on secret sharing. IEEE Trans Comput 59:842–846
Henry K (2008) The theory and applications of homomorphic cryptography. Master Thesis
Kamara S, Lauter K (2010) Cryptographic cloud storage. In: Proceedings of the 14th international conference of financial cryptography and data security: Workshop on Real-Life Cryptographic Protocols and Standardization Canary Islands, pp 136–149
KDDI Inc. (2012) Medical real-time 3d imaging solution. Online Report. http://www.kddia.com/en/sites/default/files/file/KDDI_America_Newsletter_August_2012.pdf
Lathey A, Atrey PK, Joshi N (2013) Homomorphic low pass filtering on encrypted multimedia over cloud. In: Proceedings of the 7th IEEE international conference on the semantic computing, Irvine, pp 310–313
Levoy M (1988) Display of surfaces from volume data. IEEE Comput Graph Appl 8:29–37
Mather T, Kumaraswamy S, Latif S (2009) Cloud security and privacy: An enterprise perspective on risks and compliance. O’Reilly Media Inc.
Mohanty M (2013) Secret sharing approach for securing cloud-based image processing. PhD Thesis
Mohanty M, Atrey PK, Tsang Ooi W (2012) Secure cloud-based medical data visualization. In: Proceedings of the 20th ACM international conference on Multimedia, Nara, pp 1105–1108
Mohanty M, Tsang Ooi W, Atrey PK (2013) Secure cloud-based volume ray-casting. In: Proceedings of the IEEE international conference on cloud computing technology and services, Bristol
Naehrig M, Lauter K, Vaikuntanathan V (2011) Can homomorphic encryption be practical?. In: Proceedings of the 3rd ACM workshop on cloud computing security workshop, Chicago, pp 113–124
NICE (2011) Desktop cloud visualization. Online Report. http://www.nice-software.com/products/dcv
NVIDIA (2009) Realityserver 3.0 white paper. Online Report. http://www.mentalimages.com/fileadmin/user_upload/PDF/RealityServer_White_Paper1212.pdf
Parsonson L, Grimm S, Bajwa A, Bourn L, Bai L (2012) A cloud computing medical image analysis and collaboration platform. In: Cloud Computing and Services Science. Springer, New York, pp 207–224
SaghaianNejadEsfahani SM, Luo Y, Cheung SCS (2012) Privacy protected image denoising with secret shares. In: Proceedings of the 19th IEEE international conference on image processing, Orlando, pp 253–256
Shamir A (1979) How to share a secret. Commun ACM:612–613
Sinha System (2012) Cloud based medical image management and visualization platform. Online Report. http://www.shina-sys.com/assets/brochures/3Di.pdf
Smelyanskiy M, Holmes D, Chhugani J (2009) Mapping high-fidelity volume rendering for medical imaging to CPU, GPU and many-core architectures. IEEE Trans Vis Comput Graph 15:1563–1570
Tharaud J, Wohlgemuth S, Echizen I et al (2010) Privacy by data provenance with digital watermarking. In: Proceedings of the 6th international conference on intelligent information hiding and multimedia signal processing, Darmstadt, pp 510–513
Vazhenin D (2012) Cloud-based web-service for health 2.0. In: Proceedings on joint international conference on human-centered computer environments, Hamamatsu, pp 240–243
Zissis D, Lekkas D (2012) Addressing cloud computing security issues. Future Gener Comput Syst 28:583–592
Acknowledgment
This research was supported by Singapore Ministry of Education Academic Research Fund Tier 1 No: T1251R E S1213 (Secure and Efficient Remote 3D Rendering). Majority of this work was done when the first author, Manoranjan Mohanty, was a PhD student in Department of Computer Science, School of Computing, National University of Singapore. Dr. Atrey’s contribution was supported in parts by the NSERC Canada discovery grant number 371714 and the University at Albany grant number 640075.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Example of conventional pre-classification ray-casting and SR-MPVR
In this section, we will show the working of conventional ray-casting and SR-MPVR with a simple example. Since SR-MSSS and SR-RSS are similar to SR-MPVR, we do not provide examples for these two schemes.
In our example, we will first run through the conventional pre-classification ray-casting, and then will discuss SR-MPVR. We will show that the colors rendered by SR-MPVR is almost equal to the colors rendered by the conventional algorithm
1.1 Conventional pre-classification volume ray-casting
As explained in Section 4.1 and shown in Fig. 1, the conventional volume ray-casting algorithm steps can be divided into the following steps: pre ray-projection, ray-projection, sampling, interpolation, and composition. We discuss these steps with an 8 × 8 × 8 input volume data V.
1.1.1 Pre ray-projection
This step finds the shaded colors and opacities of the voxel values, and stores them in a look up table. For our example, let us assume that the colors and opacities of the voxels are stored in Table 3.
1.1.2 Ray-projection
In this step, a number of rays are projected to V from the image space. In the image space, the colors and opacity of a pixel are the colors and opacity rendered along the ray originated from it. Since the rendering along a ray is similar to the rendering along other rays, we discuss about the rendering along one ray X.
1.1.3 Sampling
In our example, let us assume that the projected ray X is sampled at two sample points s 1 and s 2.
1.1.4 Interpolation
The colors and opacities along s 1 and s 2 are found by trilinear interpolation of the colors and opacities of the neighbouring voxels.
In our example, let us assume that the voxels (3, 3, 3)…(4, 4, 4) are the neighbouring voxels of s 1 and the voxels (5, 5, 5)…(6, 6, 6) are the neighboring voxels of s 2. If the interpolating factors of voxels (3, 3, 3)…(4, 4, 4) and (5, 5, 5)…(6, 6, 6) are given as D 3, 3, 3 = 0.125, D 3,3,4 = 0.125, D 3,4,3 = 0.125, D 3,4,4 = 0.125, D 4,3,3 = 0.125, D 4,3,4 = 0.125, D 4,4,3 = 0.125, D 4, 4, 4=0.125 and D 5, 5, 5 = 0.125, D 5,5,6 = 0.125, D 5,6,5 = 0, D 5,6,6 = 0.25, D 6,5,5 = 0.25, D 6,5,6 = 0, D 6,6,5 = 0.125, D 6, 6, 6 = 0.125respectively, the interpolated colors and opacities of s 1 and s 2 can be calculated as \(R_{s_{1}} = 42.875, G_{s_{1}} = 70.375, B_{s_{1}} = 142.25, A_{s_{1}} = 0.406\) and \(R_{s_{2}} = 104.375, G_{s_{2}} = 48.875, B_{s_{2}}= 93.25, A_{s_{2}} = 0.3\) respectively.
1.1.5 Composition
In this step, the colors and opacity along the ray are found by compositing the colors and opacities of the sample points. The composited colors are then truncated to get the rendered color.
Therefore, in our example, the rendered colors and opacity are calculated as R = 43, G = 34, B = 68, and A = 0.5842.
1.2 SR-MPVR
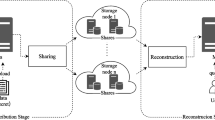
As discussed in Section 6, our scheme, such as SR-MPVR, is targeted to cloud-based pre-classification rendering. Figure 2 shows the architecture of our scheme. In our scheme, the server performs the pre ray-projection step of ray-casting and then creates shares of output color in data preparation step. A color share and a copy of opacities represents a share volume, which is sent to a datacenter. The datacenters perform post ray-projection operation, such as sampling, interpolation, and classification, on their share volumes and send the rendered share images to the client. Finally, the client recovers the secret image from the shared images by reconstructing the secret colors from the share colors.
1.2.1 Data preparation
In this step, the server first performs pre ray-projection operations on V, and then creates three shares of V using Shamir’s secret sharing.
Without loss of generality, let us assume that the server uses (2,3) Shamir’s secret sharing. Therefore, three datacenters performing rendering operations, but shared rendered images from at least two datacentres are required to get the secret image.
Suppose we decide to round off the floating point number in interpolation step by 4 decimal places (i.e., d = 4) and the float in composition step by 6 decimal places (i.e., f = 6). Then, the server uses the secret sharing polynomial F(x) = (C + 100x) mod 2570000000011, where C is the color. Using this polynomial, three shares of colors are created. The color shares along with copies of opacities are given in Tables 4, 5, and 6, those represent the share volumes V 1, V 2, and V 3 respectively.
1.3 Ray-projection
The client projects the same rays those it could have projected to the conventional ray-casting, to the data volumes presented by share tables in the datacenters.
1.3.1 Post ray-projection rendering
Post ray-projection steps are as follows.
Sampling: A ray is sampled at the same sample points where it could have been sampled in the conventional ray-casting. Thus, our discussed ray X is sampled at the sample points s 1(3.5,3.5,3.5) and s 2(5.5,5,6) for all three datacenters.
Interpolation: In this step, each datacenter finds the color and opacity of the sample points by interpolating the color shares and opacities given in its share table. Since we convert the interpolating factors by rounding off them by 4 decimal places, the interpolating factors of voxels (3, 3, 3)…(4, 4, 4) and (5, 5, 5)…(6, 6, 6) are calculated as \(D^{(4)}_{3, 3, 3} = 1250, D^{(4)}_{3,3,4} = 1250, D^{(4)}_{3,4,3} = 1250, D^{(4)}_{3,4,4} = 1250, D^{(4)}_{4,3,3} = 1250, D^{(4)}_{4,3,4} = 1250, D^{(4)}_{4,4,3} = 1250, D^{(4)}_{4, 4, 4} = 1250\), and \(D^{(4)}_{5, 5, 5} = 1250, D^{(4)}_{5,5,6} = 1250, D^{(4)}_{5,6,5} = 0, D^{(4)}_{5,6,6} = 2500, D^{(4)}_{6,5,5} = 2500, D^{(4)}_{6,5,6} = 0, D^{(4)}_{6,6,5 = 1250}, D^{(4)}_{6, 6, 6} = 1250\)respectively. Using these interpolating factors, the first datacenter, second datacenter, and third datacenter calculate the colors of s 1 and s 2 as (R 1,1 = 1428750, G 1,1 = 1703750, B 1,1 = 2422500, R 2,1 = 2043750, G 2,1 = 1488750, B 2,1 = 1932500), (R 1,2 = 2428750, G 1,2 = 2703750, B 1,2 = 3422500, R 2,2 = 3043750, G 2,2 = 2488750, B 2,2 = 2932500), and (R 1,3 = 3428750, G 1,3 = 3703750, B 1,3 = 4422500, R 2,3 = 4043750, G 2,3 = 3488750, B 2,3 = 3932500) respectively.
Interpolation: In this step, the colors and opacity along the ray are found by compositing colors and opacities of the sample points. Each datacenter composites its colors and opacities from the interpolated colors and opacities available to it. In our example, f = 6. Using this value, the first datacenter, the second datacenter, and the third datacenter calculate their composite colors as \((R^{\prime }_{1} = 1019175750000, G^{\prime }_{1} = 930830750000, B^{\prime }_{1} = 1268224500000)\), \((R^{\prime }_{2} = 1603375750000, G^{\prime }_{2} = 1515030750000, B^{\prime }_{2} = 1852424500000)\), and \((R^{\prime }_{3} = 2187575750000, G^{\prime }_{3} = 2099230750000, B^{\prime }_{3} = 2436624500000)\) respectively. For all datacenters, the composited opacity is 0.5842.
1.4 Image recovery
In this step, the client obtains the secret colors and opacities from the share colors and opacities obtained from three datacenters. Since each datacenter has a copy of the secret rendered opacity, the opacity of a pixel is the rendered opacity along that ray at any datacenter. Therefore, for Ray X, the opacity is 0.5842, which is equal to the rendered opacity along that ray by the conventional pre-classification ray-casting.
The secret colors, however, are found by first reconstructing (using Lagrange interpolation) a value from the share colors, and then dividing the value by 10000000000. Since we use (2,3) secret sharing, we need at least two shares to obtain the secret. Without any loss of generality, we choose the shares of first and second datacenters, and find the rendered color as R = 43, G = 34, and B = 68.
Appendix B: List of symbols
Rights and permissions
About this article
Cite this article
Mohanty, M., Ooi, W.T. & Atrey, P.K. Secret sharing approach for securing cloud-based pre-classification volume ray-casting. Multimed Tools Appl 75, 6207–6235 (2016). https://doi.org/10.1007/s11042-015-2567-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2567-8