Abstract
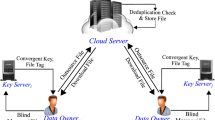
Increment of multimedia data motivates users to utilize cloud storage (CS) to exploit its massive size. For this extensible storage system, there are two desirable requirements: (1) the users should be able to ensure that their outsourced data is securely protected and (2) the cloud service provider should be able to eliminate redundant copies of data for improvement of storage utilization. Conventional encryption scheme does not satisfy the deduplication on ciphertext as it destroys message equality. Recent study, DupLESS, has enhanced Convergent Encryption (CE) and provided strong privacy. However, CE-based scheme allows the users to possibly decrypt cloud data even if the user loses his ownership to the data. In order to solve this problem, we propose a secure deduplication scheme with user revocation. Our scheme leverages oblivious pseudo-random function to generate encryption key. The CS enforces data access policy using privilege-based encryption to provide user revocation. The security analysis proves that the proposed scheme is secure against unauthorized decryption by revoked users or the cloud server, and brute-force attack on predictable set of data.






Similar content being viewed by others
References
Abadi M, Boneh D, Mironov I, Raghunathan A, Segev G (2013) Message-locked encryption for lock-dependent messages. Adv Cryptol - CRYPTO 8042:374–391. doi:10.1007/978-3-642-40041-4_21
Bellare M, Keelveedhi S (2013) DupLESS: Server-aided encryption for deduplicated storage. In: Proceedings of the 22nd USENIX conference on security, pp 179-194
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attributed-based encryption. IEEE Symp Secur Pri:321–334. doi:10.1109/SP.2007.11
Bellare M, Keelveedhi S, Ristenpart T (2013) Message-locked encryption and secure deduplication. Adv Crypto- EUROCRYPT 7881:296–312. doi:10.1007/978-3-642-38348-9_18
Bellare M, Namprempre C, Pontcheval D, Semanko M (2003) The one-more-RSA-inversion problems and the security of Chaum’s blind signature scheme. J Cryptol 16(3):185–215. doi:10.1007/s00145-002-0120-1
Boneh D, Franklin M (2001) Identity-based encryption from the Weil pairing. Adv Cryptol- CRYPTO 2139:213–229. doi:10.1007/3-540-44647-8_13
Bolosky WJ, Douceur JR, Ely D, Theimer M (2000) Feasibility of a serverless distributed file system deployed on an existing set of desktop PCs. In: Proceedings of the ACM SIGMETRICS international conference on Measurement and modeling of computer systems, pp 34–43
Clements AT, Ahmad I, Vilayannur M, Li J (2009) Decentralized deduplication in SAN cluster file systems. In: USENIX annual technical conference, pp 8–8
Douceur JR, Adya A, Bolosky WJ, Simon D, Theimer M (2002) Reclaiming space from duplicate files in a serverless distributed file system. In: Proceedings 22nd international conference on distributed computing systems, pp 617–624, doi:10.1109/ICDCS.2002.1022312, (to appear in print)
Dropbox (2014) http://www.dropbox.com. Accessed 20 December 2014
ECM (2014) http://www.emc.com/data-protection/avamar.htm. Accessed 20 December 2014
Fiat A, Naor M (1993) Broadcast encryption. Adv Cryptol - CRYPTO 773:480–491. doi:10.1007/3-540-48329-2_40
googledrive (2014) http://drive.google.com. Accessed 20 December 2014
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM conference on computer and communications security, pp 89–98. doi:10.1145/1180405.1180418
Halevi S, Harnik D, Pinkas B, Shulman-Peleg A (2011) Proofs of ownership in remote storage systems. In: Proceedings of the 18th ACM conference on computer and communications security, pp 491–500, doi:10.1145/2046707.2046765, (to appear in print)
Intel IT Center (2014) Planning guide: getting started with Hadoop. Steps IT managers can take to move forward with big data analytics. http://www.intel.com/content/dam/www/public/us/en/documents/guides/getting-started-with-hadoop-planning-guide.pdf Accessed 20 December
Java Pairing-Based Cryptography Library (JPBC) (2014) http://gas.dia.unisa.it/projects/jpbc. Accessed 20 December 2014
Li J, Chen X, Li M, Li J, Lee P P C, Lou W (2014) Secure deduplication with efficient and reliable convergent key management. IEEE IEEE Trans Parallel Distrib Syst 25(6):1615–1625. doi:10.1109/TPDS.2013.284
Open source project ciphertext-policy attribute based encryption (CP-ABE) (2014) http://github.com/junwei-wang/cpabe. Accessed 20 December 2014
Russell A, Wang H (2002) How to fool an unbounded adversary with a short key. Adv Crypto- EUROCRYPT 2332:133–148. doi:10.1007/3-540-46035-7_9
Sahai A, Waters B (2005) Fuzzy identity-based encryption. Adv Cryptol- EUROCRYPT 3497:457–473. doi:10.1007/11426639_27
Sagiroglu S, SINANC D (2013) Big data : a review. In: International conference on collaboration technologies and systems, pp 42–47. doi:10.1109/CTS.2013.6567202
Santis A D, Masucci B (1999) Multiple ramp schemes. IEEE Trans Inf Theory 45(5):1720–1728. doi:10.1109/18.771255
Acknowledgements
This work was supported by the National Research Foundation of Korea(NRF) grant funded by the Korea government(MSIP) (No.2013R1A2A2A01005559). This research was also supported by the Chung-Ang University Excellent Student Scholarship.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kwon, H., Hahn, C., Kim, D. et al. Secure deduplication for multimedia data with user revocation in cloud storage. Multimed Tools Appl 76, 5889–5903 (2017). https://doi.org/10.1007/s11042-015-2595-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2595-4