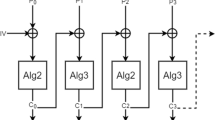
Abstract
This paper presents an efficient symmetric cryptosystem based on a non–scaled nor discretized skew tent map (STM); this system is implemented in a USB device interacting with a software module in a personal computer. The USB device uses a dedicated processor that contains a pseudorandom numbers generator (PRNG) to generate uniformly distributed chaotic sequences that satisfy the randomness tests defined in the NIST 800–22SP guide. The software module uses these sequences with substitution and rotation functions to produce cryptograms with confusion and diffusion properties, high level of security, high avalanche effect and high encryption and decryption speed. A variety of analysis and tests has been carried out to prove the security and the validity of the algorithm. Some of the evaluated characteristics are the statistical behavior, correlation, strength against differential attack, entropy, key space, key sensitivity, mutual information, encryption and decryption speed, and randomness test. Additionally, we analyze the structure of the proposed cryptosystem to find some security vulnerabilities; in this part, the analysis are based on known plaintext attack used in the literature on chaotic cryptosystems. In this way, the realized analysis shows that the performance of the proposed algorithm offers a high security level. Mutual information is calculated as evidence of this level of security.















Similar content being viewed by others
References
Al-Najjar AM, Al-Najjar HM, et al (2011) Image encryption algorithm based on logistic map and pixel mapping table. In: Proceedings of International Arab Conference on Information Technology, (ACIT 2011): 56–60
Amin M, El-Latif AAA (2010) Efficient modified rc5 based on chaos adapted to image encryption. J Electron Imaging 19(1):013012–013012
Barakat ML, Radwan AG, Salama KN (2011) Hardware realization of chaos based block cipher for image encryption. In: 2011 international conference on microelectronics (ICM). IEEE, pp 1–5
Barakat ML, Mansingka AS, Radwan AG, Salama KN (2014) Hardware stream cipher with controllable chaos generator for colour image encryption. IET Image Process 8(1):33–43
Birkhoff GD (1931) Proof of the ergodic theorem. Proc Natl Acad Sci 17 (12):656–660
Boriga R, Dăscălescu A C, Priescu I (2014) A new hyperchaotic map and its application in an image encryption scheme. Signal Process Image Commun 29(8):887–901
Chakraborty R (2011) Fpga based cipher design & implementation of recursive oriented block arithmetic and substitution technique (robast). IJACSA Editorial
Chattopadhyay D, Mandal MK, Nandi D (2011) Symmetric key chaotic image encryption using circle map. Indian J Sci Technol 4(5):593–599
Chen H-C, Yen J-C (2003) A new cryptography system and its vlsi realization. J Syst Archit 49(7):355–367
Devaney RL, Devaney L, Devaney L (1989) An introduction to chaotic dynamical systems, vol 13046. Addison-Wesley Reading
François M, Grosges T, Barchiesi D, Erra R (2012) A new image encryption scheme based on a chaotic function. Signal Process Image Commun 27(3):249–259
Fu C, Chen J-J, Zou H, Meng W-H, Zhan Y-F, Yu Y-W (2012) A chaos-based digital image encryption scheme with an improved diffusion strategy. Opt Express 20(3):2363–2378
Fu C, Huang J-B, Wang N-N, Hou Q-B, Lei W-M (2014) A symmetric chaos-based image cipher with an improved bit-level permutation strategy. Entropy 16 (2):770–788
Ghosal P, Biswas M, Biswas M (2010) A compact fpga implementation of triple-des encryption system with ip core generation and on-chip verification. In: Proceeding of the 2010 international conference on industrial engineering and operation management, Dhaka, Bangladesh
He D, He C, Jiang L-G, Zhu H-W, Hu G-R (2001) Chaotic characteristics of a one-dimensional iterative map with infinite collapses. IEEE Trans Circuits Syst I, Fundam Theory Appl 48(7):900–906
Janssens S, Thomas J, Borremans W, Gijsels P, Verbauwhede I, Vercauteren F, Preneel B, Vandewalle J (2001) Hardware/software co-design of an elliptic curve public-key cryptosystem. In: 2001 IEEE workshop on signal processing systems. IEEE, pp 209–216
Kadir A, Hamdulla A, Guo W-Q (2014) Color image encryption using skew tent map and hyper chaotic system of 6th-order cnn. Optik-Int J Light Electron Opt 125(5):1671–1675
Kartalopoulos SV (2008) Annulling traps & fixed traps in chaos cryptography. In: 2008 new technologies mobility and security. IEEE, pp 1–4
Khan M, Shah T (2015) An efficient chaotic image encryption scheme. Neural Comput Applic 26(5):1137–1148
Khan MK, Zhang J, Tian L (2007) Chaotic secure content-based hidden transmission of biometric templates. Chaos, Solitons Fractals 32(5):1749–1759
Khan MK, Alghathbar K, Zhang J (2011) Privacy-preserving and tokenless chaotic revocable face authentication scheme. Telecommun Syst 47(3-4):227–234
Lasota A, Mackey MC (2013) Chaos, fractals, and noise: stochastic aspects of dynamics, vol 97. Springer Science & Business Media
Li J, Liu H (2013) Colour image encryption based on advanced encryption standard algorithm with two-dimensional chaotic map. IET Inf Secur 7(4):265–270
Li C, Li S, Alvarez G, Chen G, Lo K-T (2007) Cryptanalysis of two chaotic encryption schemes based on circular bit shift and xor operations. Phys Lett A 369(1):23–30
Li S, Li C, Chen G, Bourbakis NG, Lo K-T (2008) A general quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process Image Commun 23(3):212–223
Li C, Zhang LY, Ou R, Wong K-W, Shu S (2012) Breaking a novel colour image encryption algorithm based on chaos. Nonlinear Dyn 70(4):2383–2388
Liu S, Sun J, Xu Z, Cai Z (2008) An improved chaos-based stream cipher algorithm and its vlsi implementation. In: 4th international conference on networked computing and advanced information management, 2008. NCM’08, vol 2. IEEE, pp 191–197
Ott E (2002) Chaos in dynamical systems. Cambridge University Press
Ou S-C, Chung H-Y, Sung W-T (2006) Improving the compression and encryption of images using fpga-based cryptosystems. Multimedia Tools Appl 28(1):5–22
Pande A, Zambreno J (2010) Design and hardware implementation of a chaotic encryption scheme for real-time embedded systems. In: International conference on signal processing and communications (SPCOM), pp 1–5
Pande A, Zambreno J (2013) A chaotic encryption scheme for real-time embedded systems: design and implementation. Telecommun Syst 52(2):551–561
Pisarchik AN, Zanin M (2012) Chaotic map cryptography and security. Int J Comput Res 19(1):49
Rhouma R, Meherzi S, Belghith S (2009) Ocml-based colour image encryption. Chaos, Solitons Fractals 40(1):309–318
Rukhin A, Soto J, Nechvatal J, Barker E, Leigh S, Levenson M, Banks D, Heckert A, Dray J, Vo S, et al (2010) Statistical test suite for random and pseudorandom number generators for cryptographic applications, nist special publication
Sakthidasan K, Santhosh Krishna BV (2011) A new chaotic algorithm for image encryption and decryption of digital color images. Int J Inf Educ Technol 1(2):137
Scheicher K, Sirvent VF, Surer P (2016) Dynamical properties of the tent map. J Lond Math Soc:jdv071
Shannon CE (1949) Communication theory of secrecy systems. Bell Syst Tech J 28(4):656–715
Stoyanov B, Kordov K (2015) Image encryption using chebyshev map and rotation equation. Entropy 17(4):2117–2139
Sushko I, Avrutin V, Gardini L (2016) Bifurcation structure in the skew tent map and its application as a border collision normal form. J Differ Equ Appl 22(4):582–629
Usama M, Khan MK, Alghathbar K, Lee C (2010) Chaos-based secure satellite imagery cryptosystem. Comput Math Appl 60(2):326–337
Van Tilborg HCA, Jajodia S (2014) Encyclopedia of cryptography and security. Springer Science & Business Media
Wheeler DD (1989) Problems with chaotic cryptosystems. Cryptologia 13(3):243–250
Wheeler DD, Matthews RAJ (1991) Supercomputer investigations of a chaotic encryption algorithm. Cryptologia 15(2):140–152
Wei J, Liao X, Wong K-W, Xiang T (2006) A new chaotic cryptosystem. Chaos, Solitons Fractals 30(5):1143–1152
Wen W (2016) Security analysis of a color image encryption scheme based on skew tent map and hyper chaotic system of 6th-order cnn against chosen-plaintext attack. Multimedia Tools Appl 75(6):3553–3560
Wong K-W, Kwok BS-H, Law W-S (2008) A fast image encryption scheme based on chaotic standard map. Phys Lett A 372(15):2645–2652
Wu X, Li Y, Kurths J (2015) A new color image encryption scheme using cml and a fractional-order chaotic system. PLoS ONE 10(3):e0119660
Yang D, Liu Z, Zhou J (2014) Chaos optimization algorithms based on chaotic maps with different probability distribution and search speed for global optimization. Commun Nonlinear Sci Numer Simul 19(4):1229–1246
Yap W-S, Phan R C-W, Yau W-C, Heng S-H (2015) Cryptanalysis of a new image alternate encryption algorithm based on chaotic map. Nonlinear Dyn 80 (3):1483–1491
Yavuz E, Yazıcı R, Kasapbaşı MC, Yamaç E (2015) A chaos-based image encryption algorithm with simple logical functions. Comput Electr Eng
Ye R, Guo W (2013) A chaos-based image encryption scheme using multi modal skew tent maps. J Emerg Trends Comput Inf Sci 4(10):800–810
Ye R, Ma Y (2013) A secure and robust image encryption scheme based on mixture of multiple generalized bernoulli shift maps and arnold maps. Int J Comput Netw Inf Secur 5(7):21
Zhang G, Liu Q (2011) A novel image encryption method based on total shuffling scheme. Opt Commun 284(12):2775–2780
Zhang L, Liao X, Wang X (2005) An image encryption approach based on chaotic maps. Chaos, Solitons Fractals 24(3):759–765
Zhang Y, Xiao D (2013) Cryptanalysis of s-box-only chaotic image ciphers against chosen plaintext attack. Nonlinear Dyn 72(4):751–756
Zhang W, Wong K-W, Yu H, Zhu Z-L (2013) An image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Commun Nonlinear Sci Numer Simul 18(8):2066–2080
Acknowledgments
The authors thank the financial support of the TecNM 393.15PD and SIP IPN 20160213 projects. G. Delgado–Gutiérrez (CVU–372164) thanks for the scholarship provided by CONACYT. Technical and computational support from F. Rodríguez–Santos and J. L. Pichardo–Méndez (IPN) is gratefully acknowledged.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Palacios-Luengas, L., Delgado-Gutiérrez, G., Díaz-Méndez, J.A. et al. Symmetric cryptosystem based on skew tent map. Multimed Tools Appl 77, 2739–2770 (2018). https://doi.org/10.1007/s11042-017-4375-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4375-9