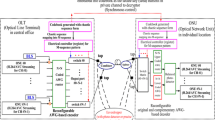
Abstract
Traditional chaos-based encryption techniques use pseudorandom codes to implement encryption (e.g., XOR; exclusive or operation) directly, resulting in the violation of requirements for media compression formats for image transmission. In this study, a programmable spatial light modulator (SLM)-based optical wavelength filter was investigated for implementing a scrambling-based cryptographic scheme in WDM networks. A new chaotic tent/hologram mapping algorithm (THmA) and advanced THmA are proposed for triggering the programmable SLM-based filter array. Similarly, an approximately symmetric scheme was used to configure a scrambling SLM-based decryption scheme for performing decryption operations when the initial value and control parameters of the chaotic sequence as individual secret keys are communicated in advance over a private channel. The proposed scheme was evaluated using video application-layer experiments. The results revealed that compared with conventional reconfigurable schemes involving triggered registers and switches behind an AWG router, the number of code space sizes involved in the proposed cryptographic scheme increased by more than 1.31E + 89 times, thereby avoiding eavesdropping attacks in the physical layer. Furthermore, on the basis of the reduced peak signal-to-noise ratio of the encrypted videos and the unidentifiability of the videos to unauthorized users, the scrambling efficiency of the proposed scheme was sufficiently high.














Similar content being viewed by others
References
Ahadpour S, Sadra Y, ArastehFrad Z (2012) A novel chaotic image encryption using generalized threshold function. Int J Comput Appl 42(18):25–31
Ahadpour S, Sadra Y, ArastehFrad Z (2012) A novel chaotic encryption scheme based on pseudorandom bit padding. IJCSI Int J Comput Sci Issues 9(1):449–456
Baugher M, McGrew D, Naslund M, Carrara E, Norrman K (2004) The Secure Real-Time Transport Protocol (SRTP). IETF RFC 3711
Chang Y-T, Chuan-Ching S, Jen-Fa H (2007) Robust design for reconfigurable coder/decoders to protect against eavesdropping in spectral amplitude coding optical CDMA networks. IEEE J Lightwave Technol 25(8):1931–1948
Chang Y-T, Lin Y-C (2015) Dynamic reconfigurable encryption and decryption with chaos/M-sequence mapping algorithm for secure H.264/AVC video streaming over OCDMA passive optical network. Multimedia Tools Appl 75(16):9837–9859
Chang YT, Tsailin CW (2015) Dynamic scrambling scheme of arrayed-waveguide grating-based encryptors and decryptors for protection against eavesdropping. Comput Electr Eng
Chang Y-T, Lin Y-C, Chen Y-C, Liou Y-T (2017) Scrambling cryptography using programmable SLM-Based filter for video streaming over a WDM network. In: Barneva RP, Brimkov VE, Tavares JMR (eds) Computational modeling of objects presented in images fundamentals, methods, and applications, LNCS, vol. 10149. Springer International Publishing, Cham
Cheng H, Li X (2000) Partial encryption of compressed images and videos. IEEE Trans Signal Process 48(8):2439–2451
Chiaraluce F, Ciccarelli L, Gambi E, Pierleoni P, Reginelli M (2002) A new chaotic algorithm for video encryption. IEEE Trans Consum Electron 48(4):838–844
Devaney R (1989) An introduction to chaotic dynamical systems, 2nd edn. Addison-Wesley, Redwood City
Dixit S (2003) IP over WDM: building the next-generation optical internet. John Wiley and Sons, Inc., New Jersey
Dufaux F, Ebrahimi T (2008) Scrambling for privacy protection in video surveillance systems. IEEE Trans Circ Syst Video Technol 18(8):1168–1174
Etemadi Borujeni S, Ehsani MS (2015) Modified logistic maps for cryptographic application. Appl Math 6:773–782
Huang J-F, Meng S-H, Lin Y-C, Chen K-S, Huang A-C (2014) Using wavelength/time signature scrambling to realize cryptographic coded-WDM data network. Procedia Comput Sci 34:39–46
Huang J-F, Meng S-H, Lin Y-C (2014) Securing optical code-division multiple-access networks with a postswitching coding scheme of signature reconfiguration. Opt Eng 53(11):115101
Karafolas N, Uttamchandani D (1996) Optical fiber code division multiple access networks: a review. Opt Fiber Technol 2(2):149–168
Kavehrad M, Zaccarin D (1995) Optical code-division-multiplexed systems based on spectral encoding of noncoherent sources. IEEE J Lightwave Technol 13:534–545
Kim KS (2003) On the evolution of PON-based FTTH solutions. Inf Sci 149:21–30
Kitayama K, Wang X, Wada N (2006) OCDMA over WDM PON—solution path to gigabit-symmetric FTTH. J Lightwave Technol 24(4):1654–1662
Kocarev L, Lian S (eds) (2011) Chaos-based cryptography-theory, algorithm and application. Springer, Heidelberg
Kramer G, Pesavento G (2002) Ethernet passive optical network (EPON): building a next-generation optical access network. IEEE Commun Mag 40:66–73
Li TY, Yorke JA (1975) Period three implies chaos. Am Math Mon 82(10):985–992
Marhic SV, Kostic ZI, Titlebaum EL (1993) A new family of optical code sequences for use in spread spectrum fiber-optic local area networks. IEEE Trans Commun 41(8):1217–1221
Massoudi A, Lefebvre F, De Vleeschouwer C, Macq B, Quisquater J-J (2008) Overview on selective encryption of image and video: challenges and perspectives. EURASIP J Inf Sec, Article ID 179290, 18 pages
May RM (1976) Simple mathematical models with very complicated dynamics. Nature 261(5560):459–467
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vision Comput 24:926–934
Parker MC, Cohen AD, Mears RJ (1998) Dynamic digital holographic wavelength filtering. J Lightwave Technol 16(7)
Petzold C (1998) Programming Windows®, 5th edn. Microsoft Press
Sakthidasan@Sankaran K, Santhosh Krishna BV (2011) A new chaotic algorithm for image encryption and decryption of digital color images. Int J Inf Educ Technol 1(2):137–141
Salehi JA (1989) Code division multiple-access techniques in optical fiber networks—part I: fundamental principles. IEEE Trans Commun 37(8):824–833
Shake TH (2005) Security performance of optical CDMA Against eavesdropping. J IEEE J Lightwave Technol 23(2):655–670
Shake TH (2005) Confidentiality performance of spectral-phase-encoded optical CDMA. IEEE J Lightwave Technol 23(4):1652–1663
Sühring K (2009) H.264/AVC reference software group [On-line]. Available: http://iphome.hhi.de/suehring/tml/ Joint Model 12.2 (JM12.2)
Tseng SP, Wu J (2011) The SAC OCDMA PON with super perfect difference code. IEEE Int Conf Commun
Wiegand T, Sullivan GJ, Bjontegaard G, Luthra A (2003) Overview of the H.264/AVC video coding standard. IEEE Trans Circuits Syst Video Technol 13(7):560,576
Wu BB, Narimanov EE (2006) A method for secure communications over a public fiber-optical network. Opt Express 14(9):3738–3751
Acknowledgements
This study was supported under grant No. MOST 105-2221-E-244-004 from the Ministry of Science and Technology, Taiwan. We thank Prof. Jen-Fa Huang for providing invaluable suggestion.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chang, YT., Lin, YC., Chen, YC. et al. Scrambling-based cryptography with a programmable SLM-based filter-triggered chaotic tent/hologram mapping algorithm for secure H.264/AVC video streaming over a WDM network. Multimed Tools Appl 76, 25421–25453 (2017). https://doi.org/10.1007/s11042-017-4525-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4525-0