Abstract
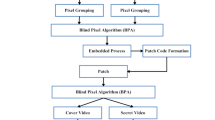
In recent days, providing security to data is a crucial and critical task in many image processing applications. Specifically, video security is an important and demanding concept. For this purpose, some of the embedding, encoding and decoding techniques are mentioned in existing works, but it has some drawbacks such as increased time complexity, computational complexity and memory consumption. Moreover, it does not provide high security during video transmission. To overcome all these issues, a new technique, namely, Zero Level Binary Mapping (ZLBM) is proposed in this paper for video embedding scheme. The motivation of this paper is to provide high security during video transformation by using the video steganography technique. At first, the cover and stego videos are given as the inputs and it will be converted into the video frames for further processing. Here, the Fuzzy Adaptive Median Filtering (FAMF) technique is employed to remove the impulse noise in the video frames. Then, the pixels in the filtered frames are grouped by using the block wise pixel grouping technique. After that, the frames are embedded with the help of ZLBM technique and encoded based on the patch wise code formation technique. On the receiver side, the inverse ZLBM and block wise pixel regrouping techniques are applied to get the original cover and stego videos. The novel concept of this paper is the use of ZLBM and patch wise code formation techniques for video embedding and compression. The main advantages of the proposed system are high security, good quality and reduced complexity. The experimental results evaluate the performance of the proposed video embedding technique in terms of Peak Signal-to-Noise Ratio (PSNR), Mean Squared Error (MSE), Compression Ratio (CR), Bits Per Pixel (BPP) and Signal-to-Noise Ratio (SNR).









Similar content being viewed by others
References
Abd-El-Hafiz SK, Radwan AG, Abdel Haleem SH, Barakat ML (2014) A fractal-based image encryption system. IET Image Process 8(12):742–752
Anjum F, Yadav S, Aafreen R, Hasan T (2016) A survey: secure data transmission using video steganography. Imperial Journal of Interdisciplinary Research (2.5)
Boho A, Van Wallendael G, Dooms A, De Cock J, Braeckman G, Schelkens P, Preneel B, Van de Walle R (2013) End-to-end security for video distribution: the combination of encryption, watermarking, and video adaptation. IEEE Signal Process Mag 30(2):97–107
Cui J, Liu Y, Xu Y, Zhao H, Zha H (2013) Tracking generic human motion via fusion of low-and high-dimensional approaches. IEEE Trans Syst Man Cybern Syst 43(4):996–1002. doi:10.1109/TSMCA.2012.2223670
Dasgupta K, Mondal JK, Dutta P (2013) Optimized video steganography using genetic algorithm (GA). Procedia Technol 10:131–137. doi:10.1016/j.protcy.2013.12.345
Dixit S, Gaikwad A, Gaikwad S, Shanwad SA, Scholar U (2016) Public key cryptography based lossless and reversible data hiding in encrypted images. Int J Eng Sci 3550
Gao X, Zhang K, Tao D, Li X (2012) Image super-resolution with sparse neighbor embedding. IEEE Trans Image Process 21(7):3194–3205
Gupta H, Chaturvedi S (2014) Video steganography through LSB based hybrid approach. (IJCSNS) Int J Comput Sci Netw Secur 14(3):99
Hsieh M-H, Cheng F-C, Shie M-C, Ruan S-J (2013) Fast and efficient median filter for removing 1–99% levels of salt-and-pepper noise in images. Eng Appl Artif Intell 26(4):1333–1338
Karim MSA, Wong K (2014) Universal data embedding in encrypted domain. Signal Process 94:174–182. doi:10.1016/j.sigpro.2013.06.014
Kashyap N, Sinha G (2012) Image watermarking using 3-level discrete wavelet transform (DWT). Int J Mod Educ Comput Sci 4(3):50
Khare R, Raghuwanshi K (2014) A review of video steganography methods. Int J Res Advent Technolohu 2(1)
Kokkonis G, Psannis KE, Roumeliotis M, Ishibashi Y (2016) Efficient algorithm for transferring a real-time HEVC stream with haptic data through the internet. J Real-Time Image Proc 12(2):343–355
Kokkonis G, Psannis KE, Roumeliotis M, Schonfeld D (2016) Real-time wireless multisensory smart surveillance with 3D-HEVC streams for internet-of-things (IoT). J Supercomput:1–19
Liu Y, Zhang X, Cui J, Wu C, Aghajan H, Zha H (2010) Visual analysis of child-adult interactive behaviors in video sequences. In: 2010 16th International Conference on virtual systems and multimedia (VSMM). IEEE, pp 26–33
Liu Y, Cui J, Zhao H, Zha H (2012) Fusion of low-and high-dimensional approaches by trackers sampling for generic human motion tracking. In: 2012 21st International Conference on pattern recognition (ICPR). IEEE, pp 898–901
Liu Y, Nie L, Han L, Zhang L, Rosenblum DS (2015) Action2activity: recognizing complex activities from sensor data. arXiv preprint arXiv:161101872, in twenty-fourth International joint Conference on Artificial Intelligence (IJCAI 2015)
Liu Y, Zheng Y, Liang Y, Liu S, Rosenblum DS IJCAI (2016) Urban water quality prediction based on multi-task multi-view learning. In: Proceedings of the International Joint Conference on Artificial Intelligence
Liu Y, Liang Y, Liu S, Rosenblum DS, Zheng Y (2016) Predicting urban water quality with ubiquitous data. arXiv preprint arXiv:1610.09462
Liu Y, Zhang L, Nie L, Yan Y, Rosenblum DS (2016) Fortune teller: predicting your career path. In: Proceedings of the thirtieth AAAI Conference on Artificial Intelligence, pp 201–207
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: sensor-based activity recognition. Neurocomputing 181:108–115
Liu L, Cheng L, Liu Y, Jia Y, Rosenblum DS (2016) Recognizing complex activities by a probabilistic interval-based model. In: AAAI, pp 1266–1272
Liu Y, Ju L, Hu M, Zhao H, Jia S, Jia Z (2016) A new data hiding method for H.264 based on secret sharing. Neurocomputing 188:113–119. doi:10.1016/j.neucom.2015.02.102
Liu Y, Chen L, Hu M, Jia Z, Jia S, Zhao H (2016) A reversible data hiding method for H.264 with Shamir’s (t, n)-threshold secret sharing. Neurocomputing 188:63–70. doi:10.1016/j.neucom.2014.10.109
Lu Y, Wei Y, Liu L, Zhong J, Sun L, Liu Y (2016) Towards unsupervised physical activity recognition using smartphone accelerometers. Multimed Tools Appl 1–19
Maggiani L, Bourrasset C, Petracca M, Berry F, Pagano P, Salvadori C (2015) HOG-dot: a parallel kernel-based gradient extraction for embedded image processing. IEEE Signal Process Lett 22(11):2132–2136. doi:10.1109/lsp.2015.2463092
Memos VA, Psannis KE (2016) Encryption algorithm for efficient transmission of HEVC media. J Real-Time Image Proc 12(2):473–482. doi:10.1007/s11554-015-0509-3
Ohm J-R, Sullivan GJ (2013) High efficiency video coding: the next frontier in video compression [standards in a nutshell]. IEEE Signal Process Mag 30(1):152–158
Papadopoulos NA, Psannis KE. Sequential multiple LSB methods and real-time data hiding: variations for visual cryptography ciphers. J Real-Time Image Proc 1–12
Pourazad MT, Doutre C, Azimi M, Nasiopoulos P (2012) HEVC: the new gold standard for video compression: how does HEVC compare with H. 264/AVC? IEEE Consum Electron Mag 1(3):36–46. doi:10.1109/MCE.2012.2192754
Preoţiuc-Pietro D, Liu Y, Hopkins DJ, Ungar L (2017) Beyond binary labels: political ideology prediction of twitter users. In: ACL
Psannis K (2009) Efficient redundant frames encoding algorithm for streaming video over error prone wireless channels. IEICE Electron Express 6(21):1497–1502
Psannis KE (2016) HEVC in wireless environments. J Real-Time Image Proc 12(2):509–516
Psannis KE, Ishibashi Y (2006) Impact of video coding on delay and jitter in 3G wireless video multicast services. EURASIP J Wirel Commun Netw 2006(2):51–51
Psannis K, Ishibashi Y (2008) Enhanced H. 264/AVC stream switching over varying bandwidth networks. IEICE Electron Express 5(19):827–832
Psannis K, Ishibashi Y (2008) Efficient flexible macroblock ordering technique. IEICE Trans Commun 91(8):2692–2701
Psannis KE, Ishibashi Y (2009) Efficient error resilient algorithm for H. 264/AVC: mobility management in wireless video streaming. Telecommun Syst 41(2):65–76
Psannis KE, Hadjinicolaou MG, Krikelis A (2006) MPEG-2 streaming of full interactive content. IEEE Trans Circuits Syst Video Technol 16(2):280–285
Qian Z, Zhang X, Wang S (2014) Reversible data hiding in encrypted JPEG bitstream. IEEE Trans Multimedia 16(5):1486–1491
Ramalingam M, Isa NAM (2015) A steganography approach over video images to improve security. Indian J Sci Technol 8(1):79
Ramanjaneyulu K, Rajarajeswari K (2012) Wavelet-based oblivious image watermarking scheme using genetic algorithm. IET Image Process 6(4):364–373. doi:10.1049/iet-ipr.2010.0347
Roy P, Nath A (2014) New steganography approach using encrypted secret message inside audio and video media. Int J Adv Res Comput Sci Manag Stud 2(12):46–59
Sadek MM, Khalifa AS, Mostafa MG (2015) Video steganography: a comprehensive review. Multimed Tools Appl 74(17):7063–7094
Satpute S, Shahane S, Singh S, Sharma M (2015) An approach towards video steganography using FZDH (forbidden zone data hiding). (IJIACS0) Int J Innov Adv Comput Sci 4(1):100–105
Shrestha S (2014) Image denoising using new adaptive based median filters. arXiv preprint arXiv:14102175
Singh P, Chadha R (2013) A survey of digital watermarking techniques, applications and attacks. (IJEIT) Int J Eng Innov Technol 2(9):165–175
Teoh SH, Koik BT, Ibrahim H (2013) Exploration of current trend on median filtering methods utilized in digital grayscale image processing. Int J Mater Mech Manuf 1(1)
Venugopala P, Sarojadevi H, Chiplunkar NN, Bhat V (2014) Video watermarking by adjusting the pixel values and using scene change detection. In: 2014 Fifth International Conference on Signal and Image Processing (ICSIP). IEEE, pp 259–264
Viral MG, Rishishwar A, Trivedi M (2015) A real time approach for secure image transmission using video steganography. (IJECSCSE) Int J Electron Commun Soft Comput Sci Eng 4(2):1
Wajgade VM, Kumar DS (2013) Enhancing data security using video steganography. Int J Emerg Technol Adv Eng 3(4):549–552
Wang W-J, Huang C-T, Liu C-M, Su P-C, Wang S-J (2013) Data embedding for vector quantization image processing on the basis of adjoining state-codebook mapping. Inf Sci 246:69–82
YUV video sequences (2016) http://trace.eas.asu.edu/yuv/
Zhang L, Dong W, Zhang D, Shi G (2010) Two-stage image denoising by principal component analysis with local pixel grouping. Pattern Recogn 43(4):1531–1549
Zong T, Xiang Y, Natgunanathan I, Guo S, Zhou W, Beliakov G (2015) Robust histogram shape-based method for image watermarking. IEEE Trans Circuits Syst Video Technol 25(5):717–729. doi:10.1109/tcsvt.2014.2363743
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Rajalakshmi, K., Mahesh, K. ZLBM: zero level binary mapping technique for video security. Multimed Tools Appl 77, 13225–13247 (2018). https://doi.org/10.1007/s11042-017-4942-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4942-0