Abstract
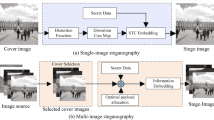
In this paper, we present a universal embedding strategy for batch adaptive steganography in both spatial and JPEG domain. This strategy can make up for the problem when applying batch steganography to adaptive steganography in JPEG domain meanwhile improve the secure performance in spatial domain. When embedding, the strategy are employed to determine the sub-batch of cover images to carry the total message. To evaluate the feasibility of images selected as sub-batch, we calculate the histogram equilibrium for each image and the images with larger “size” and more equilibrated histogram are set a high priority when determining the sub-batch. The histogram equilibrium of images is the combination of entropy and standard deviation for the probability of histogram coefficients. We keep the repetitive information of using entropy and standard deviation to measure the histogram equilibrium. Experimental results show that histogram equilibriums vary according to images and employing images with larger “size” and more equilibrated histogram to carry the total message is a universal embedding strategy for both spatial and JPEG domain. Batch adaptive steganography with this embedding strategy can improve the secure performance effectively.







Similar content being viewed by others
References
Denemark T, Sedighi V, Holub V, Cogranne R, Fridrich J (2014) Selection-channel-aware rich model for steganalysis of digital images. In: Proceedings of the IEEE international workshop on information forensic and security. Atlanta, pp 48–53
Filler T, Judas J, Fridrich J (2011) Minimizing additive distortion in steganography using syndrome-trellis codes. IEEE Trans Inf Forensics Secur 6:920–935
Filler T, Pevný T, Bas P (2011) Break our steganographic system: the ins and outs of organizing BOSS. In: Filler T, Pevný T, Craver S, Ker A (eds) IH. LNCS, vol 6958, pp 59–70
Fridrich J, Kodovský J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur 7:868–882
Fridrich J, Goljan M, Lisonek P, Soukal D (2005) Writing on wet paper. IEEE Trans Signal Process 53:3923–3935
Guo L, Ni j Shi Y (2012) An efficient JPEG steganographic scheme using uniform embedding. In: IEEE International workshop on information forensic and security (WIFS). Tenerife, pp 169–174
Holub V, Fridrich J (2012) Designing steganographic distortion using directional filters. In: Proceedings of the IEEE international workshop on information forensic and security. Tenerife, pp 234–239
Holub V, Fridrich J (2013) Random projections of residuals for digital image steganalysis. IEEE Trans Inf Forensics Secur 8:1996–2006
Holub V, Fridrich J (2013) Digital image steganography using universal distortion. In: Proceedings of the 1st ACM workshop information hiding multimedia security. ACM, New York, pp 59–68
Holub V, Fridrich J (2015) Low-complexity features for JPEG steganalysis using undecimated DCT. IEEE Trans Inf Forensics Secur 10:219–228
Ker A, Pevný T (2012) Batch steganography in the real world. In: ACM Proceeding of the on multimedia and security. ACM, New York, pp 1–10
Ker A, Pevný T, Kodovský J, Fridrich J (2008) The square root law of steganographic capacity. In: Proceedings of the 10th ACM workshop on multimedia and security. ACM, New York, pp 107–116
Kodovský J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inf Forensics Secur 7:432–444
Li B, Wang M, Huang J, Li X (2014) A new cost function for spatial image steganography. In: Proceedings of the IEEE International conference on image processing. Paris, pp 4206–4210
Pevny T, Filler T, Bas P (2010) Using high-dimensional image models to perform highly undetectable steganography. In: Information hiding (Lecture Notes in Computer Science). Springer-Verlag, Berlin, pp 161–177
Sallee P (2003) Model-based steganography. In: Digital watermarking (Lecture Notes in Computer Science), vol 2939, pp 154–167
Shllee P Matlab JPEG Toolbox [Online]. Available: http://www.philsallee.com/jpegtbx/index.html
Song X, Liu F, Yang C, Luo X, Zhang Y (2015) Steganalysis of adaptive JPEG steganography using 2D gabor filters. In: Proceedings of the 3th ACM workshop information on hiding multimedia security. ACM, New York, pp 15–23
Westfeld A (2001) F5-A steganographic algorithm. In: Information hiding (Lecture Notes in Computer Science), vol 2137, pp 289–302
Zhao Z, Guan Q, Zhao X (2016) Constructing near-optimal double-layered syndrome-trellis codes for spatial steganography. In: Proceedings on the 4th ACM workshop information on hiding multimedia security. ACM, New York, pp 139–148
Zhao Z, Guan Q, Zhao X, Yu H, liu C (2016) Embedding strategy for batch adaptive steganography. In: The 15th international workshop on digital-forensics and watermarking (IWDW2016), accepted
Acknowledgments
This work was supported by the Natural Science Foundation of China under U1536105 and U1636102, and National Key Technology R&D Program under 2014BAH41B01, 2016YFB0801003 and 2016QY15Z2500.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhao, Z., Guan, Q., Zhao, X. et al. Universal embedding strategy for batch adaptive steganography in both spatial and JPEG domain. Multimed Tools Appl 77, 14093–14113 (2018). https://doi.org/10.1007/s11042-017-5016-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5016-z