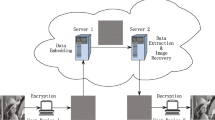
Abstract
This paper proposes a novel reversible data hiding (RDH) algorithm with differential compression (DC) in encrypted image, which has high embedding capacity. The key contributions are two sides. (1) An efficient block-based encryption scheme is developed for encrypting image. It can transfer spatial correlation between neighboring pixels of plaintext image into encrypted image. (2) The DC scheme is proposed to conduct compression of encrypted image. It can efficiently compress encrypted image by exploiting pixel correlation and vacate a large room for data embedding. Many experiments are conducted to evaluate the performance of our RDH algorithm. Comparisons illustrate that our RDH algorithm outperforms some state-of-the-art algorithms in embedding capacity and computational time.










Similar content being viewed by others
References
Agrawal S, Kumar M (2017) Mean value based reversible data hiding in encrypted images. Optik - International Journal for Light and Electron Optics 30:922–934
Arithmetic Coding and Huffman Coding in MATLAB, Available: http://www.ux.uis.no/~karlsk/proj99/index.html
Celik MU, Sharma G, Tekalp AM, Saber E (2005) Lossless generalized-LSB data embedding. IEEE Trans Image Process 14(2):253–266
CVG (UGR) Image database. Available: http://decsai.ugr.es/cvg/dbimagenes/index.php
Fridrich J, Goljan M, Du R (2002) Lossless data embedding–New paradigm in digital watermarking. EURASIP Journal on Advances in Signal Processing 2002(2):185–196
Hong W, Chen T, Wu H (2012) An improved reversible data hiding in encrypted images using side match. IEEE Signal Processing Letters 19(4):199–202
Huang J, Shi YQ (1998) An adaptive image watermarking scheme based on visual masking. Electron Lett 34(8):748–750
Huang F, Huang J, Shi YQ (2016) New framework for reversible data hiding in encrypted domain. IEEE Transactions on Information Forensics & Security 11(12):2777–2789
Image database of BOWS-2. Available: http://bows2.ec-lille.fr/
Li M, Li Y (2017) Histogram shifting in encrypted images with public key cryptosystem for reversible data hiding. Signal Process 130:190–196
Li X, Zhang W, Gui X, Yang B (2017) Efficient reversible data hiding based on multiple histograms modification. IEEE Transactions on Information Forensics & Security 10(9):2016–2027
Liao X, Shu C (2015) Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J Vis Commun Image Represent 28:21–27
Liu Y, Nie L, Han L, Zhang L and Rosenblum DS (2015) Action2Activity: Recognizing complex activities from sensor data, In: Proc. of the Twenty-Fourth International Joint Conference on Artificial Intelligence, pp.1617–1623
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: sensor-based activity recognition. Neurocomputing 181:108–115
Liu Y, Zhang L, Nie L, Yan Y, and Rosenblum DS (2016) Fortune teller: Predicting your career path, In: Proc. of the Thirtieth AAAI Conference on Artificial Intelligence, pp. 201–207
Liu Y, Zheng Y, Liang Y, Liu S, and Rosenblum DS (2016) Urban water quality prediction based on multi-task multi-view learning, In: Proc. of the Twenty-Fifth International Joint Conference on Artificial Intelligence, pp.2576–2582
Ma K, Zhang W, Zhao X, Yu N, Li F (2013) Reversible data hiding in encrypted images by reserving room before encryption. IEEE Transactions on Information Forensics and Security 8(3):553–562
Ma Y, Luo X, Li X, Bao Z, Zhang Y (2018) Selection of rich model steganalysis features based on decision rough set α-positive region reduction. IEEE Transactions on Circuits and Systems for Video Technology. https://doi.org/10.1109/TCSVT.2018.2799243
Ni Z, Shi YQ, Ansari N, and Su W (2003) Reversible data hiding, In: Proc. of IEEE International Symposium on Circuits and Systems, pp.912–915
Qian Z, Xu H, Luo X, Zhang X (2018) New framework of reversible data hiding in encrypted JPEG bitstreams. IEEE Transactions on Circuits and Systems for Video Technology. https://doi.org/10.1109/TCSVT.2018.2797897
Qin C, Zhang X (2015) Effective reversible data hiding in encrypted image with privacy protection for image content. J Vis Commun Image Represent 31:154–164
Qin C, Chang CC, Hsu T (2013) Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimedia Tools and Applications 74(15):5861–5872
Qin C, Chang CC, Huang Y, Liao L (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Transactions on Circuits and Systems for Video Technology 23(7):1109–1118
Qin C, He Z, Yao H, Cao F, Gao L (2018) Visible watermark removal scheme based on reversible data hiding and image inpainting. Signal Process Image Commun 60:160–172
Rivest RL (1992) The RC4 Encryption Algorithm, RSA Data Security Inc
Shi YQ, Ni Z, Zou D, Liang C, and Xuan G (2004) Lossless data hiding: fundamentals, algorithms and applications, In: Proc. of IEEE International Symposium on Circuits and Systems, vol.2, pp.33–36
Shi YQ, Li X, Zhang X, Wu HT, Ma B (2016) Reversible data hiding: advances in the past two decades. IEEE Access 4:3210–3237
Shiu C, Chen Y, Hong W (2015) Encrypted image-based reversible data hiding with public key cryptography from difference expansion. Signal Process Image Commun 39:226–233
Skretting K, Håkon Husøy J, and Aase SO (1999) Improved Huffman coding using recursive splitting, In: Proc. of NORSIG 1999 conference, pp.9–11
Tang Z, Zhang X, Zhang S (2014) Robust perceptual image hashing based on ring partition and NMF. IEEE Trans Knowl Data Eng 26(3):711–724
Tang Z, Zhang X, Lan W (2015) Efficient image encryption with block shuffling and chaotic map. Multimedia Tools and Applications 74(15):5429–5448
Tang Z, Zhang X, Li X, Zhang S (2016) Robust image hashing with ring partition and invariant vector distance. IEEE Transactions on Information Forensics and Security 11(1):200–214
Tang Z, Wang F, Zhang X (2017) Image encryption based on random projection partition and chaotic system. Multimedia Tools and Applications 76(6):8257–8283
Tang Z, Lu Q, Lao H, Yu C, Zhang X (2018) Error-free reversible data hiding with high capacity in encrypted image. Optik-International Journal for Light and Electron Optics 157:750–760
Tian J (2002) Reversible watermarking by difference expansion, In: Proc. of Workshop on Multimedia and Security, pp. 19–22
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Transactions on Circuits and Systems for Video Technology 13(8):890–896
van Leest A, van der Veen M, and Bruekers F (2003) Reversible image watermarking, In: Proc. of International Conference on Image Processing, vol.2, pp.731–734
Weng S, Zhao Y, Pan JS, Ni R (2008) Reversible watermarking based on invariability and adjustment on pixel pairs. IEEE Signal Processing Letters 15:721–724
Weng S, Pan JS, Li L (2016) Reversible data hiding based on an adaptive pixel-embedding strategy and two-layer embedding. Inf Sci 369:144–159
Weng S, Liu Y, Pan JS, Cai N (2016) Reversible data hiding based on flexible block-partition and adaptive block-modification strategy. J Vis Commun Image Represent 41:185–199
Xuan G, Zhu J, Chen J, Shi YQ, Ni Z, Su W (2002) Distortionless data hiding based on integer wavelet transform. Electron Lett 38(25):1646–1648
Xuan G, Shi YQ, Chai P, Cui X, Ni Z, and Tong X (2007) Optimum histogram pair based image lossless data embedding, In: Proc. of International Workshop on Digital Watermarking, vol.5041, pp. 264–278
Zhang X (2011) Reversible data hiding in encrypted image. IEEE Signal Processing Letters 18(4):255–258
Zhang X, Tang Z, Liang T, Zhang S, Zhu Y, Sun Y (2012) Data hiding method based on local image feature. Lect Notes Comput Sci 7669:247–256
Zhang W, Ma K, Yu N (2014) Reversibility improved data hiding in encrypted images. Signal Process 94(1):118–127
Zhang X, Sun Z, Tang Z, Yu C, Wang X (2017) High capacity data hiding based on interpolated image. Multimedia Tools and Applications 76(7):9195–9218
Zhang Y, Qin C, Zhang W, Liu F, Luo X (2018) On the fault-tolerant performance for a class of robust image steganography. Signal Process 146:99–111
Zheng S, Li D, Hu D, Ye D, Wang L, Wang J (2016) Lossless data hiding algorithm for encrypted images with high capacity. Multimedia Tools & Applications 75(21):13765–13778
Acknowledgements
This work is partially supported by the National Natural Science Foundation of China (61562007, 61762017, 61702332, 61672354), Guangxi “Bagui Scholar” Teams for Innovation and Research, the Guangxi Natural Science Foundation (2017GXNSFAA198222, 2015GXNSFDA139040), the Project of Guangxi Science and Technology (GuiKeAD17195062), the Project of the Guangxi Key Lab of Multi-source Information Mining & Security (16-A-02-02, 15-A-02-02), and the Innovation Project of Guangxi Graduate Education (XYCSZ 2018076). The authors would like to thank the anonymous referees for their valuable comments and suggestions.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tang, Z., Xu, S., Yao, H. et al. Reversible data hiding with differential compression in encrypted image. Multimed Tools Appl 78, 9691–9715 (2019). https://doi.org/10.1007/s11042-018-6567-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6567-3