Abstract
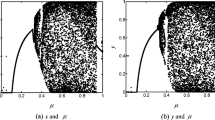
In this paper, an image encryption algorithm based on 3-D DNA level permutation and substitution scheme is proposed. In order to improve the security level of the image encryption, a 3-D DNA level hybrid permutation scheme using chaotic sequence sorting and 3-D cat map is presented to effectively shuffle the element positions, a novel 3-D DNA level substitution method based on random number is given to directly change the elements of the 3-D DNA matrix, and dynamic and random DNA encoding rules and DNA decoding rules are designed to upgrade the randomness of the encryption results. Moreover, a 6-D hyperchaotic system is used to generate the chaotic sequence for all the encryption processes, and SHA 256 hash value of the plain image is utilized to compute the initial values of chaotic system and system parameters of the 3-D cat map. Simulation results and performance analyses demonstrate that the proposed encryption scheme has large key space, high key sensitivity and may resist against some typical attacks, and it may effectively secure the secret image information.










Similar content being viewed by others
References
Algredo-Badillo I, Feregrino-Uribe C, Cumplido R, Morales-Sandoval M (2013) FPGA-based implementation alternatives for the inner loop of the secure hash algorithm SHA-256. Microprocess Microsyst 37:750–757
Al-Sharif S, Iqbal F, Baker T, Khattack A (2016) White-hat hacking framework for promoting security awareness. 8th IFIP Int Conf New Technol Mobil Sec (NTMS) 2016:21–23
Alvarez G, Li SJ (2006) Some basic cryptographic requirements for chaos-based cryptosystem. Int J Bifurcat Chaos 16:2129–2151
Babaei M (2013) A novel text and image encryption method based on chaos theory and DNA computing. Nat Comput 12:101–107
Chai XL, Gan ZH, Chen YR, Zhang YS (2017) A visually secure image encryption scheme based on compressive sensing. Signal Process 134:35–51
Chai XL, Chen YR, Lucie B (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Chai XL, Yang K, Gan ZH (2017) A new chaos-based image encryption algorithm with dynamic key selection mechanisms. Multimed Tools Appl 76:9907–9927
Chai XL, Gan ZH, Lu Y, Chen YR, Han DJ (2017) A novel image encryption algorithm based on the chaotic system and DNA computing. Int J Mod Phys C 28:1750069
Chai XL, Fu XL, Gan ZH, Lu Y, Chen YR (2019) A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process 155:44–62
Chai XL, Gan ZH, Yuan K, Chen YR, Liu XX (2019) A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput Appl 31:219–237
Chen GR, Mao YB, Charles K (2004) Chui. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Soliton Fract 21:749–761
Chen TH, Zhang M, Wu JH, Yuen C, Tong Y (2016) Image encryption and compression based on kronecker compressed sensing and elementary cellular automata scrambling. Opt Laser Technol 84:118–133
Chen JX, Zhang Y, Qi L et al (2018) Exploiting chaos-based compressed sensing and cryptographic algorithm for image encryption and compression. Opt Laser Technol 99:238–248
Chen JX, Zhu ZL, Zhang LB, Zhang YS, Yang BQ (2018) Exploiting self-adaptive permutation-diffusion and DNA random encoding for secure and efficient image encryption. Signal Process 142:340–353
Dalhoum ALA, Mahafzah BA, Awwad AA, Aldhamari I, Ortega A, Alfonseca M (2012) Digital image scrambling using 2D cellular automata. IEEE Multimedia 19(4):28–36
Federal Information Processing Standards Publication 180-2 (2002) Announcing the secure hash standard, U.S.Doc/NIST
Gan ZH, Chai XL, Han DJ, Chen YR (2018) A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput Appl. https://doi.org/10.1007/s00521-018-3541-y
Ghafir I, Saleem J, Hammoudeh M, Faour H, Prenosil V, Jaf S, Jabbar S, Baker T (2018) Security threats to critical infrastructure: the human factor. J Supercomput 74:4986–5002
Guesmi R, Farah MAB, Kachouri A, Samet M (2016) A novel chaos-based image encryption using DNA sequence operation and secure hash algorithm SHA-2. Nonlinear Dyn 83:1123–1136
Hu T, Liu Y, Gong LH, Guo SF, Yuan HM (2017) Chaotic image cryptosystem using DNA deletion and DNA insertion. Signal Process 134:234–243
Hu T, Liu Y, Gong LH, Ouyang CJ (2017) An image encryption scheme combining chaos with cycle operation for DNA sequences. Nonlinear Dyn 87:51–66
Hua ZY, Zhou YC (2017) Design of image cipher using block-based scrambling and image filtering. Inf Sci 396:97–113
Hua ZY, Jin F, Xu BX et al (2018) 2D logistic-sine-coupling map for image encryption. Signal Process 149:148–161
Huang XL, Ye GD (2014) An image encryption algorithm based on hyper-chaos and DNA sequence. Multimed Tools Appl 72:57–70
Jain A, Rajpal N (2016) A robust image encryption algorithm resistant to attacks using DNA and chaotic logistic maps. Multimed Tools Appl 75:5455–5472
Karam Y, Bake T, Taleb-Bendiab A (2012) Security support for intention driven elastic cloud computing. 2012 Sixth UKSim/AMSS European Symposium on Computer Modeling and Simulation: 14–16
Kumar M, Iqbal A, Kumar P (2016) A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie-Hellman cryptography. Signal Process 125:187–202
Li LJ. (2013) High-dimensional chaotic system and its application on image encryption. Yanshan University
Li CQ, Lin DD, L JH (2017) Cryptanalyzing an image-scrambling encryption algorithm of pixel bits. IEEE Multimedia 24:64–71
Li CQ, Lin DD, Feng BB, Lü JH (2018) Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 6:75834–75842
Li CQ, Lin DD, Lü JH, Hao F (2018) Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimed 25:46–56
Li CQ, Feng BB, Li SJ, Kurths J, Chen GR (2019) Dynamics analysis of digital chaotic maps via state-mapping networks. IEEE T Circ-I. https://doi.org/10.1109/TCSI.2018.2888688
Liu L, Zhang Q, Wei X (2012) A RGB image encryption algorithm based on DNA encoding and chaos map. Comput Electr Eng 38:1240–1248
Liu H, Xiao D, Zhang R, Bai S (2016) Roubust and hierarchical watermarking of encrypted images based on compressive sensing. Signal Process- Image 45(C):41–51
Mackay M, Baker T, Al-Yasiri A (2012) Security-oriented cloud computing platform for critical infrastructures. Comput Law Sec Rev 28:679–686
Norouzi B, Mirzakuchaki S (2017) An image encryption algorithm based on DNA sequence operations and cellular neural networ. Multimed Tools Appl 76:13681–13701
Ping P, Wu JJ, Mao YC, Xu F, Fan JY (2018) Design of image cipher using life-like cellular automata and chaotic map. Signal Process 150:233–247
Ravi K, Sheridan John T, Basanta B (2018) Nonlinear double image encryption using 2D non-separable canonical transform and phase retrieval algorithm. Opt Laser Technol 107:353–360
Rehman A u, Liao XF, Ashraf R, Ullah S, Wang HW (2018) A color image encryption technique using exclusive-OR with DNA complementary rules based on chaos theory and SHA-2. Optik 159:348–367
Tang Z, Zhang X, Lan W (2014) Efficient image encryption with block shuffling and chaotic map. Multimed Tools Appl. https://doi.org/10.1007/s11042-014-1861-1
Wang XY, Zhang YQ, Bao XM (2015) A novel chaotic image encryption scheme using DNA sequence operations. Opt Lasers Eng 73:53–61
Wang XY, Li P, Zhang YQ, Liu LY, Zhang HZ, Wang XK (2017) A novel color image encryption scheme using DNA permutation based on the Lorenz system. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-4534-z
Wang S, Deng C, Lin W et al (2017) NMF-based image quality assessment using extreme learning machine. IEEE Trans Cybern 47:232
Watson JD, Crick FHC (1953) A structure for deoxyribose nucleic acid. Nature 171:737–738
Wei X, Guo L, Zhang Q, Zhang J, Lian S (2012) A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J Syst Softw 85:290–299
Weng SW, Chen Y, Hong W, Pan JS, Chang CC, Liu YJ (2019) An improved integer transform combining with an irregular block partition. Symmetry 11(1):49
Weng SW, Chen Y, Chang CC, Zhang CY (2019) Improved k-pass pixel value ordering based data hiding. IEEE Access. https://doi.org/10.1109/ACCESS.2019.2904174
Weng SW, Shi YQ, Hong W, Yao Y (2019) Dynamic improved pixel value ordering reversible data hiding. Inf Sci 489:136–154
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber J:31–38
Wu Y, Zhou Y, Saveriades G, Agaian S, Noonan J P, Natarajan P (2013) Local Shannon entropy measure with statistical tests for image randomness. Inf Sci: 323–342
Wu Y, Zhou YC, George S, Sos A, Noonan Joseph P, Premkumar N (2013) Local Shannon entropy measure with statistical tests for image randomness. Inf Sci 222:323–342
Wu XJ, Kan HB, Kurths J (2015) A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl Soft Comput 37:24–39
Wu XJ, Wang KS, Wang XY, Kan HB (2017) Lossless chaotic color image cryptosystem based on DNA encryption and entropy. Multimed Tools Appl 90:855–875
Wu JH, Liao XF, Yang B (2018) Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process 142:292–300
Wu XJ, Wang KS, Wang XY, Kan HB, Kurths J (2018) Color image DNA encryption using NCA map-based CML and one-time keys. Signal Process 148:272–287
Ye R (2011) A novel chaos-based image encryption scheme with an efficient permutation-diffusion mechanism. J Opt Commun 284:5290–5298
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear- nonlinear coupled map lattice. Inf Sci 273:329–351
Zhang Q, Wei XP (2013) A novel couple images encryption algorithm based on DNA subsequence operation and chaotic system. Optik 124:6276–6281
Zhang YS, Xiao D (2013) Cryptanalysis of S-box-only chaotic image ciphers against chosen plaintext attack. Nonlinear Dyn 72:751–756
Zhang Q, Guo L, Wei XP (2010) Image encryption using DNA addition combining with chaotic maps. Math Comput Model 52:2028–2035
Zhang YS, Xiao D, Shu YL (2013) A novel image encryption scheme based on a linear hyperbolic chaotic system of partial differential equations. Signal Process-Image 28:292–300
Zhang Q, Liu LL, Wei XP (2014) Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEU-Int J Electron C 68:186–192
Zhang XP, Zhao ZM, Wang JY (2014) Chaotic image encryption based on circular substitution box and key stream buffer. Signal Process- Image 29:902–913
Zhang W, Yu H, Zhao YL et al (2016) Image encryption based on three-dimensional bit matrix permutation. Signal Process 118:36–50
Zhang YQ, Wang XY, Liu J, Chi ZL (2016) An image encryption scheme based on the MLNCML system using DNA sequences. Opt Lasers Eng 82:95–103
Zhang LM, Sun KH, Liu WH, He SB (2017) A novel color image encryption scheme using fractional-order hyperchaotic system and DNA sequence operations. Chin Phys B 26:100504
Zhang LY, Liu Y, Pareschi F, Zhang Y, Wong KW, Rovatti R, Setti G (2017) On the security of a class of diffusion mechanisms for image encryption. IEEE Trans Cybern 99:1–13
Zhou NR, Li HL, Wang D, Pan SM, Zhou ZH (2015) Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt Commun 343:10–21
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. J Opt Commun 285:29–37
Acknowledgements
All the authors are deeply grateful to the editors for smooth and fast handling of the manuscript. The authors would also like to thank the anonymous referees for their valuable suggestions to improve the quality of this paper. This work is supported by the National Natural Science Foundation of China (Grant No. 41571417, U1604145, 61802111, 61872125, 61871175), Science and Technology Foundation of Henan Province of China (Grant No. 182102210027, 182102410051), China Postdoctoral Science Foundation (Grant No. 2018 T110723, 2016 M602235), Key Scientific Research Projects for Colleges and Universities of Henan Province (Grant No. 19A413001), CERNET NGI Technology Innovation Project (Grant No. NGII20170902) and the Research Foundation of Henan University (Grant No. xxjc20140006).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhu, C., Gan, Z., Lu, Y. et al. An image encryption algorithm based on 3-D DNA level permutation and substitution scheme. Multimed Tools Appl 79, 7227–7258 (2020). https://doi.org/10.1007/s11042-019-08226-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08226-4