Abstract
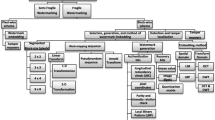
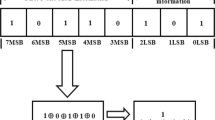
Both security and tamper localization are essential for fragile watermarking techniques. Embedded fragile watermark should be sensitive enough to cover images. But high sensitivity maybe bring inaccurate tamper localization, and both high sensitivity and accurate tamper localization seem contradictory. This paper proposes a watermark scheme based on dual fragile watermark: diffusion watermark and authentication watermark. The diffusion watermark is determined by a cover image, a secret key and two random numbers via nonlinear transformations, and the authentication watermark is generated from the cover image, the diffusion watermark and another secret key. The diffusion watermark and the authentication watermark have high sensitivity to cover images and at meantime the authentication watermark can verify the integrity of images and localize tampered area. The scrambled authentication watermark and the diffusion watermark are arbitrarily embedded into the two lowest significant bit layers of the cover image through a random sequence controlled by a secret key. The design aims to enhance the security of fragile watermarking, and the statistical results and security analysis show that this scheme can resist chosen cover-image attacks.












Similar content being viewed by others
References
Barreto PSLM, Kim HY, Rijmen V (2002) Toward a secure public-key blockwise fragile authentication watermarking. In: International conference on image processing, 2001. Proceedings, vol 2, pp 494–497
Birajdar GK, Mankar VH (2013) Digital image forgery detection using passive techniques: a survey. Digit Investig 10(3):226–245
Botta M, Cavagnino D, Pomponiu V (2015) A successful attack and revision of a chaotic system based fragile watermarking scheme for image tamper detection. AEUE - Int J Electron Commun 69(1):242–245
Caragata D, Mucarquer JA, Koscina M, Assad SE (2016) Cryptanalysis of an improved fragile watermarking scheme. AEUE - Int J Electron Commun 70(6):777–785
Chaluvadi SB, Prasad MVNK (2010) Efficient image tamper detection and recovery technique using dual watermark. In: 2009 world congress on nature & biologically inspired computing, pp 993–998
Chang CC, Hu YS, Lu TC (2006) A watermarking-based image ownership and tampering authentication scheme. Pattern Recogn Lett 27(5):439–446
Chen G, Mao Y, Chui CK (2004) A symmetric image encryption scheme based on 3d chaotic cat maps. Chaos Solitons Fractals 21(3):749–761
Chen WC, Wang MS (2009) A fuzzy c-means clustering-based fragile watermarking scheme for image authentication. Expert Syst Appl 36(2):1300–1307
Di X, Chang Y, Tao X, Bai S (2017) A watermarking algorithm in encrypted image based on compressive sensing with high quality image reconstruction and watermark performance. Multimed Tools & Appl 76(7):9265–9296
Ding W, Yi X, Wang Y (2018) Image authentication and tamper localization based on relative difference between dct coefficient and its estimated value. Multimed Tools Appl (4): 1–24
Doyoddorj M, Rhee KH (2012) Design and analysis of a fragile watermarking scheme based on block-mapping
Enayatifar R, Abdullah AH, Isnin IF, Altameem A, Lee M (2017) Image encryption using a synchronous permutation-diffusion technique. Optics & Lasers in Engineering 90:146–154
Fridrich J (2002) Security of fragile authentication watermarks with localization. Spie Proceedings 4675:691–700
Fridrich J, Goljan M, Baldoza AC (2000) New fragile authentication watermark for images. International Conference on Image Processing, 2000. Proceedings 1, 446–449
Gul E, Ozturk S (2019) A novel hash function based fragile watermarking method for image integrity. Multimed Tools Appl (10): 1–18
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Kluwer Academic Publishers
He HJ, Chen F, Tai HM, Kalker T, Zhang J (2012) Performance analysis of a block-neighborhood-based self-recovery fragile watermarking scheme. IEEE Transactions on Information Forensics & Security 7(1):185–196
Holliman M, Memon N (2000) Counterfeiting attacks on oblivious block-wise independent invisible watermarking schemes. IEEE Trans Image Process 9(3):432–441
Hsu CS, Tu SF (2016) Image tamper detection and recovery using adaptive embedding rules. Measurement 88:287–296
Hua Z, Zhou Y (2017) Design of image cipher using block-based scrambling and image filtering. Inf Sci 396:97–113
Lazarov N, Ilcheva Z (2016) A fragile watermarking algorithm for image tamper detection based on chaotic maps. In: 2016 IEEE 8th international conference on intelligent systems, pp. 723–728
Lee TY, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 41(11):3497–3506
Lin ET, Podilchuk CI, Delp EJ (2000) Detection of image alterations using semi-fragile watermarks. Proc Spie 3971:152–163
Lin PL, Hsieh CK, Huang PW (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 38(12):2519–2529
Lin T, Wang X, Wang X (2013) Cryptanalysis and improvement of a chaotic system based fragile watermarking scheme. AEUE - Int J Electron Commun 67 (6):540–547
Lisha M, Lei C, Shihong W (2019) Security analysis of a reversible watermarking algorithm for encrypted images in wavelet domain. Multimed Tools Appl 78:9827–9843
Liu SH, Yao HX, Gao W, Liu YL (2007) An image fragile watermark scheme based on chaotic image pattern and pixel-pairs. Appl Math Comput 185(2):869–882
Liu XL, Lin CC, Chang CC, Yuan SM (2016) A survey of fragile watermarking-based image authentication techniques. Journal of Information Hiding and Multimedia Signal Processing 7:1282–1292
Lo CC, Hu YC (2014) A novel reversible image authentication scheme for digital images. Signal Process 98(5):174–185
Nguyen TS, Chang CC, Yang XQ (2016) A reversible image authentication scheme based on fragile watermarking in discrete wavelet transform domain. AEUE - Int J Electronics Commun 70(8):1055–1061
Pan TG, Li DY (2011) A new algorithm of image encryption based on 3d arnold cat. Advanced Engineering Forum 1:183–187
Petitcolas FAP, Anderson RJ, Kuhn MG (1999) Information hiding-a survey. Proc IEEE 87(7):1062–1078
Phan CW (2008) Tampering with a watermarking-based image authentication scheme. Elsevier Science Inc
Ping WW (1998) A watermark for image integrity and ownership verification. In: Pics 1998: is&t’s 1998 image processing, image quality, image capture, systems conference, Portland, Oregon, USA, May, pp 374–379
Qin C, Ji P, Wang J, Chang CC (2017) Fragile image watermarking scheme based on vq index sharing and self-embedding. Multimed Tools Appl 76(2):2267–2287
Qin C, Ping J, Zhang X, Jing D, Wang J (2017) Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process 138:280–293
Qin C, Wang H, Zhang X, Sun X (2016) Self-embedding fragile watermarking based on reference-data interleaving and adaptive selection of embedding mode. Inf Sci 373:233–250
Rawat S, Raman B (2011) A chaotic system based fragile watermarking scheme for image tamper detection. AEUE - Int J Electron Commun 65(10):840–847
Schyndel RGV, Tirkel AZ, Osborne CF (2002) A digital watermark. In: IEEE international conference image processing, 1994. Proceedings. ICIP-94, vol 2, pp 86–90
Singh D, Singh SK (2015) Dct based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76(1):1–25
Sreenivas K, Prasad VK (2017) Fragile watermarking schemes for image authentication: a survey. Int J Machine Learning and Cybernetics 9(7):1193–1218
Trivedy S, Pal AK (2017) A logistic map-based fragile watermarking scheme of digital images with tamper detection. Iranian Journal of Science & Technology Transactions of Electrical Engineering 41(2):103–113
Xinhui G, Feng YXZSW Security analysis of a self-embedding fragile image watermark scheme. arXiv:1812.11735v2
Yeung MM, Mintzer F (1997) An invisible watermarking technique for image verification. In: International conference on image processing, 1997. Proceedings, vol 2, pp 680–683
Zhang X, Qian Z, Ren Y, Feng G (2011) Watermarking with flexible self-recovery quality based on compressive sensing and compositive reconstruction. IEEE Trans Inform Forensics & Secur 6(4):1223–1232
Acknowledgments
Thank anonymous reviewers for their comments on our work and constructive suggestions.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gong, X., Chen, L., Yu, F. et al. A secure image authentication scheme based on dual fragile watermark. Multimed Tools Appl 79, 18071–18088 (2020). https://doi.org/10.1007/s11042-019-08594-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08594-x