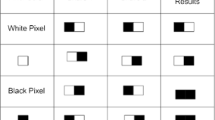
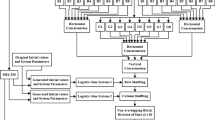
Abstract
In the modern years, multimedia security has become a prime agenda for secure transmission over unsecured channels due to the increase in digitalization of media. Cryptography is one of the techniques, which can be used for security of exchanged data. The visual cryptographic scheme generates numerous unreasonable shares of the image with specific information. The secret information hidden in the image can be retrieved by accumulating all the shares. The basic idea behind this cryptographic scheme is the encryption of image which hides the secret into m several image shares. By this process, it turns to be complex for the hackers to retrieve the original data of the image. Furthermore, to increase the confidentiality and privacy of the original image, there is in demand to make use of the efficient encryption algorithm. According to this, a new image encryption and decryption is developed using diffusion method with a combination of chaotic maps. Overall, the proposed visual cryptographic method is divided into three phases namely, i) Separation of color bands, ii) Generation of several shares and iii) Encryption & Decryption. Firstly, the color image is divided into three bands (R, G and B) and then various shares of the image are generated based on the pixel measures. After that, the encryption and decryption are done by using diffusion process associated with chaotic map. Experimental results of various analysis and computer simulation confirm that the new algorithm offers high security and is suitable for practical image encryption.










Similar content being viewed by others
References
Ateniese G, Blundo C, Santis AD, Stinson DR (1996) Visual cryptography for general access structures. Inf Comput 129(2):86–106
Ateniese G, Blundo C, Santis AD, Stinson DR Extended capabilities for visual cryptography. Theor Comput Sci 250(1):143–161
Bal SN, Nayak MR, Sarkar SK (2018) On the implementation of a secured watermarking mechanism based on cryptography and bit pairs matching. Journal of King Saud University-Computer and Information Sciences
Barik RC, Changder S, Sahu SS (2017) Image Texture-Based New Cryptography Scheme Using Advanced Encryption Standard. Computational Intelligence in Data Mining, Springer, Singapore, pp 449–458
Chang C, Tsai C, Chen T (2000) A new scheme for sharing secret color images in computer network. International Conference on Parallel and Distributed Systems, pp. 21–27
Chang C-C, Yu T-X (2002) Sharing a secret gray image in multiple images. Proceedings of the First International Symposium on Cyber Worlds (CW.02)
Chavan PV, Atique M (2012) Design of hierarchical visual cryptography. International Conference on Engineering
Chen L, Zhao D (2006) Optical color image encryption by wavelength multiplexing and lensless Fresnel transform holograms. J Opt Commun 14(8):552–560
Chen L, Zhao D (2009) Color image encoding in dual fractional Fourier-wavelet domain with random phases. J Opt Commun 282:3433–3438
Dhiman K, Kasana SS (2018) Extended visual cryptography techniques for true color images. Comput Electr Eng 70:647–658
Eberhart R, Kennedy J (1995) A new optimizer using particle swarm theory. In: Proceedings of the Sixth International Symposium on Micro Machine and Human Science, MHS 1995, pp. 39–43. IEEE, New York
Fang W, Lin J (2006) Progressive viewing and sharing of sensitive images. Pattern Recognition and Image Analysis 16(4):632–636
Geetha P, Jayanthi VS, Jayanthi AN (2018) Optimal visual cryptographic scheme with multiple share creation for multimedia applications. Comput Secur 78:pp.301–320
Hamza R (2017) A novel pseudo random sequence generator for image-cryptographic applications. Journal of Information Security and Applications 35:119–127
Hou YC, Wei SC, Lin CY (2014) Random-grid-based visual cryptography schemes. IEEE Transactions on Circuits and Systems for Video Technology 24(5):733–744
Kalai Selvi R, Kavitha V (2012) Crypto System based Authentication using CSTA in Grid. Int J Comput Appl 48(22)
Kamath M, Parab A, Salyankar A, Dholay S (2012) Extended Visual Cryptography for Color Images Using Coding Tables. International Conference on Communication, Information & Computing Technology (ICCICT), pp. 19–20
Khoirom MS, Laiphrakpam DS, Themrichon T (2018) Cryptanalysis of multimedia encryption using elliptic curve cryptography. Optik 168:370–375
Kumar S, Kumar M, Budhiraja R, Das MK, Singh S (2018) A cryptographic model for better information security. Journal of Information Security and Applications 43:123–138
Liu Z, Dai J, Sun X, Liu S (2010) Color image encryption by using the rotation of color vector in Hartley transform domains. Journal on Optical Lasers 48(5)
Liu S, Fujiyoshi M, Kiya H (2011) A Leakage Suppressed Two-level Security Visual Secret Sharing Scheme, Journal on Intelligent Signal Processing and Communication Systems (ISPACS), pp. 7–9
Loukhaoukha K, Chouinard J-Y, Berdai A (2012) A secure image encryption algorithm based on Rubik’s cube principle. J Electr Comput Eng:1–14
Lukac R, Plataniotis KN (2004) Colour image secret sharing. IEEE Electronics Letters 40(9)
Mirjalili S, Mirjalili SM, Lewis A (2014) Grey Wolf Optimizer. Adv Eng Softw 69:46–61
Mohanty M, Gehrmann C, Atrey PK (2014) Avoiding Weak Parameters in Secret Image Sharing. IEEE
Naor M, Shamir A (1995) Visual cryptography. Springer Berlin Heidelberg, Berlin, Heidelberg, pp. 1–12
Nautiyal I, Sharma M (2014) Encryption using elliptic curve cryptography using java as implementation tool. J Adv Res Comput Sci Softw Eng 4(1):620–625
Padma B, Chandravathi D, Prapoorna Roja P (2010) Encoding and decoding of a message in the Implementation of elliptic curve cryptography using Koblitz’s method. Int J Comput Sci Eng 2(5):1904–1907
Pandey LN, Shukla N (2013) Visual Cryptography Schemes using Compressed Random Shares. Journal of Advance Research in Computer Science and Management Studies 1(4):62–66
Patidar V, Pareek NK, Purohit G, Sud KK (2011) A robust and secure chaotic standard map based pseudo-random permutation substitution scheme for image encryption. Opt Commun 284:4331–4339
Popescu C (2011) A secure e-cash transfer system based on the elliptic curve discrete logarithm problem. Journal on Informatica 3(22):395–409
Rijmen V, Preneel B (1996) Efficient color visual encryption for shared colors of Benetton, Eurocrypto’96. Rump Session, Berlin
Roy PK, Mandal D (2013) Oppositional biogeography-based optimization for optimal power flow. Int J Electr Power Energy Syst 53:123–134
Roy PK, Paul C, Sultana S (2014) Oppositional teaching learning based optimization approach for combined heat and power dispatch. Int J Electr Power Energy Syst 57:392–403
Shao Z, Shang Y, Zeng R, Shu H, Coatrieux G, Wu J (2016) Robust watermarking scheme for color image based on quaternion-type moment invariants and visual cryptography. Signal Process Image Commun 48:12–21
Singh P, Raman B, Misra M (2017) A (n, n) Threshold Non-expansible XOR based Visual Cryptography with Unique Meaningful Shares. Signal Processing
Soni A, Agrawal S (2012) Using genetic algorithm for symmetric key generation in image Encryption. Int J Adv Res Comput Eng Technol (IJARCET) 1(10):137–140
Soni A, Agrawal S (2012) Using genetic algorithm for symmetric key generation in image encryption. Int J Adv Res Comput Eng Technol (IJARCET) 1(10):137–140
Srinivas M, Patnaik LM (1994) Genetic algorithms: a survey. Computer (Long Beach Calif) 27(17–26)
Sujatha K, Shalini Punithavathani D (2018). Optimized ensemble decision-based multi-focus imagefusion using binary genetic Grey-Wolf optimizer in camera sensor networks. Multimed Tools Appl 77(2):1735–1759
Sundararaj V, (2016) An Efficient Threshold Prediction Scheme for Wavelet Based ECG Signal Noise Reduction Using Variable Step Size Firefly Algorithm. International Journal of Intelligent Engineering and Systems 9(3):117–126
Sundararaj V, Muthukumar S, Kumar RS (2018) An optimal cluster formation based energy efficient dynamic scheduling hybrid MAC protocol for heavy traffic load in wireless sensor networks. Comput Secur 77:277–288
Vinu Sundararaj, (2019) Optimal task assignment in mobile cloud computing by queue based Ant-Bee algorithm. Wireless Personal Communications 104(1):173–197
Tao R, Xiang-Yi M, Wang Y (2010) Image encryption with multi orders of fractional Fourier transforms. IEEE Trans Inf Forensics Security 5:734–738
Tedmori S, Al-Najdawi N (2014) Image cryptographic algorithm based on the Haar wavelet transform. Inf Sci 269:21–34
USC-SIPI Image Database. http://sipi.usc.edu/database/database.php
Vinod Kumar Y, Malviya AK, Gupta DL, Satyendra S, Ganesh C (2012) Public key cryptosystem Technique for elliptic curve cryptography with generator g for image encryption. Int J Comput Appl 3(3):298–302
Wang S, Gu K, Ma S, Lin W, Liu X, Gao W Guided image contrast enhancement based on retrieved images in cloud. IEEE Transactions on Multimedia 18(2):219–232
Wu X, Ou D, Dai L, Sun W (2013) XOR-based meaningful visual secret sharing by generalized random grids. In: Proceedings of the First ACM Workshop on Information Hiding and Multimedia Security
Yang X-S (2010b) A new metaheuristic bat-inspired algorithm. In: González JR, Pelta DA, Cruz C, Terrazas G, Krasnogor N (eds) Nature inspired cooperative strategies for optimization (NICSO 2010). Springer Berlin Heidelberg, Berlin, pp 65–74
Yi K, Leihong Z, Dawei Z (2018) Optical encryption based on ghost imaging and public key cryptography. Opt Lasers Eng 111:58–64
You X, Li Q, Tao D et al (2014) Local metric learning for exemplar-based object detection. IEEE Transactions on Circuits and Systems for Video Technology 24(8):1265–1276
Youmaran R, Adler A, Miri A (2006) An Improved Visual Cryptography Scheme For Secret Hiding. J Commun:340–343
Zhu Z et al (2015) An adaptive hybrid pattern for noise-robust texture analysis. Pattern Recogn 48(8):2592–2608
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Geetha, P., Jayanthi, V.S. & Jayanthi, A.N. Multiple share creation based visual cryptographic scheme using diffusion method with a combination of chaotic maps for multimedia applications. Multimed Tools Appl 78, 18503–18530 (2019). https://doi.org/10.1007/s11042-019-7163-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-7163-x