Abstract
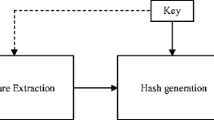
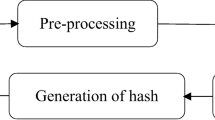
A new Discrete Cosine Transform (DCT) domain Perceptual Image Hashing (PIH) scheme is proposed in this paper. PIH schemes are designed to extract a set of features from an image to form a compact representation that can be used for image integrity verification. A PIH scheme takes an image as the input, extracts its invariant features and constructs a fixed length output, which is called a hash value. The hash value generated by a PIH scheme is then used for image integrity verification. The basic requirement for any PIH scheme is its robustness to non-malicious distortions and discriminative ability to detect minute level of tampering. The feature extraction phase plays a major role in guaranteeing robustness and tamper detection ability of a PIH scheme. The proposed scheme fuses together the DCT and Noise Resistant Local Binary Pattern (NRLBP) to compute image hash. In this scheme, an input image is divided into non-overlapping blocks. Then, DCT of each non-overlapping block is computed to form a DCT based transformed image block. Subsequently, NRLBP is applied to calculate NRLBP histogram. Histograms of all the blocks are concatenated together to get a hash vector for a single image. It is observed that low frequency DCT coefficients inherently have quite high robustness against non-malicious distortions, hence the NRLBP features extracted from the low frequency DCT coefficients provide high robustness. Computational results exhibit that the proposed hashing scheme outperforms some of the existing hashing schemes as well as can detect localized tamper detection as small as 3% of the original image size and at the same time resilient against non-malicious distortions.












Similar content being viewed by others
References
Abbas SQ, Ahmed F, Živić N, Ur-Rehman O (2016) Perceptual image hashing using SVD based noise resistant local binary pattern, in 2016 8th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), pp. 401–407: IEEE
Ahmed F, Siyal MY, Abbas VUJSP (2010) A secure and robust hash-based scheme for image authentication. Signal Processing, Elsevier 90(5):1456–1470
Armas Vega E, Sandoval Orozco A, García Villalba L, Hernandez-Castro J (2018) Digital Images Authentication Technique Based on DWT, DCT and Local Binary Patterns. Sensors 18(10):3372
Birajdar GK, Mankar VH (2013) Digital image forgery detection using passive techniques: a survey. Digit Investig 10(3):226–245
Chang J-D, Chen B-H, Tsai C-S (2013) LBP-based fragile watermarking scheme for image tamper detection and recovery, in 2013 International Symposium on Next-Generation Electronics, pp. 173–176: IEEE
Chaudhary C, Goyal P, Prasad DN, Chen Y-PP (2019) Enhancing the quality of image tagging using a Visio-textual Knowledge Base. IEEE Transactions on Multimedia 22(4):897–911
Chaudhary C, Goyal P, Goyal N, Chen Y-PP (2020) Image retrieval for complex queries using knowledge embedding. ACM Transactions on Multimedia Computing, Communications, Applications 16(1):1–23
Chen X, Qin C, Ji P (2015) Perceptual image hashing using block truncation coding and local binary pattern, in 2015 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA), pp. 856–859: IEEE
Davarzani R, Mozaffari S, Yaghmaie K (2015) Image authentication using LBP-based perceptual image hashing. Journal of AI and Data Mining 3(1):21–30
Davarzani R, Mozaffari S, Yaghmaie K (2016) Perceptual image hashing using center-symmetric local binary patterns. Multimed Tools Appl 75(8):4639–4667
Dong C, Loy CC, Tang X (2016) Accelerating the Super-Resolution Convolutional Neural Network, in European Conference on Computer Vision, Cham, pp. 391–407: Springer International Publishing
Du L, Chen Z, Ho AT (2020) Binary multi-view perceptual hashing for image authentication, Multimed Tools Appl, pp. 1–23
Eskenazi S, Bodin B, Gomez-Krämer P, Ogier J-M (2017) A perceptual image hashing algorithm for hybrid document security, in 2017 14th IAPR International Conference on Document Analysis and Recognition (ICDAR), vol. 1, pp. 741–746: IEEE
Gonzalez R Woods R (2017) Digital image processing, 4th edn. ISBN: 9780133356724, ed: Pearson
Hassan AM, Hasan YM, Wahab MA (2012) Robust visual hashing for image authentication, in International Conference on Communications and Information Technology Computing, pp. 763–767
Hernandez RAP, Miyatake MN, Kurkoski BM (2011) Robust image hashing using image normalization and SVD decomposition, in 2011 IEEE 54th International Midwest Symposium on Circuits and Systems (MWSCAS), pp. 1–4: IEEE
Holmgren J, Lombardi A (2018) Cryptographic hashing from strong one-way functions (or: One-way product functions and their applications), in 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS), pp. 850–858: IEEE
Karsh RK, Saikia A, Laskar RH (2018) Image authentication based on robust image hashing with geometric correction. Multimed Tools Appl 77(19):25409–25429
Khelaifi F, He H (2020) Perceptual image hashing based on structural fractal features of image coding and ring partition, Multimed Tools Appl, pp. 1–20
Lee H, Chen Y-PP (2014) Cell morphology based classification for red cells in blood smear images. Pattern Recogn Lett 49:155–161
Lee H, Chen Y-PP (2015) Image based computer aided diagnosis system for cancer detection. Expert Syst Appl 42(12):5356–5365
Lei Y, Wang Y, Huang J (2011) Robust image hash in radon transform domain for authentication. Signal Process Image Commun 26(6):280–288
Li Y, Wan L, Fu T, Hu W (2019) Piecewise supervised deep hashing for image retrieval. Multimed Tools Appl 78(17):24431–24451
Liu Y, Xiao Y (2013) A robust image hashing algorithm resistant against geometrical attacks. Radioengineering 22(4):1072–1082
Liu X, Sun C, Yang LT (2015) DCT-based objective quality assessment metric of 2D/3D image. Multimed Tools Appl 74(8):2803–2820
Liu H, Kadir A, Liu J (2019) Keyed hash function using hyper chaotic system with time-varying parameters perturbation. IEEE Access 7:37211–37219
Monga V, Evans BL (2006) Perceptual image hashing via feature points: performance evaluation and tradeoffs. IEEE Trans Image Process 15(11):3452–3465
Niu Y, Liu F, Li X, Gleicher M (2012) Image resizing via non-homogeneous warping. Multimedia Tools Applications 56(3):485–508
Ojala T, Pietikäinen M, Harwood D (1996) A comparative study of texture measures with classification based on featured distributions. Pattern Recogn 29(1):51–59
Paul M, Karsh RK, Talukdar FA (2019) Image Hashing based on Shape Context and Speeded Up Robust Features (SURF), in 2019 International Conference on Automation, Computational and Technology Management (ICACTM), pp. 464–468: IEEE
Pietikäinen M, Hadid A, Zhao G, Ahonen T (2011) Computer vision using local binary patterns. Springer Science & Business Media
Qin C, Hu Y, Yao H, Duan X, Gao LJIA (2019) Perceptual image hashing based on weber local binary pattern and color angle representation. IEEE Access 7:45460–45471
Ren J, Jiang X, Yuan J (2016) Face and facial expressions recognition and analysis, in Context Aware Human-Robot and Human-Agent Interaction: Springer, pp. 3–29
Roweis ST, Saul LK (2000) Nonlinear dimensionality reduction by locally linear embedding. Science 290(5500):2323–2326
Sajjad M, Haq IU, Lloret J, Ding W, Muhammad K (2019) Robust image hashing based efficient authentication for smart industrial environment. IEEE Transactions on Industrial Informatics 15:6541–6550
Sebastian LS, Varghese A, Manesh T (2015) Image authentication by content preserving robust image hashing using local and global features. Procedia Computer Science 46:1554–1560
Stallings W (2017) Cryptography and network security: principles and practice. Pearson Upper Saddle River
Swaminathan A, Mao Y, Wu M, security (2006) Robust and secure image hashing. IEEE Transactions on Information Forensics and Security 1(2):215–230
Tang Z, Dai Y, Zhang X, Zhang S (2012) Perceptual image hashing with histogram of color vector angles, in International Conference on Active Media Technology, pp. 237–246: Springer
Tang Z, Zhang X, Zhang S (2013) Robust perceptual image hashing based on ring partition and NMF. IEEE Trans Knowl Data Eng 26(3):711–724
Tang Z, Yu Y, Zhang H, Yu M, Yu C, Zhang X (2019) Robust image hashing via visual attention model and ring partition. Math Biosci Eng 16:6103–6120
Venkatesan R, Koon S-M, Jakubowski MH, Moulin P (2000) Robust image hashing, in Proceedings 2000 International Conference on Image Processing (Cat. No. 00CH37101), vol. 3, pp. 664–666: IEEE
Wu M, Mao Y, Swaminathan A (2007) A signal processing and randomization perspective of robust and secure image hashing, in 2007 IEEE/SP 14th Workshop on Statistical Signal Processing, pp. 166–170: IEEE
Yang H, Yin J, Yang Y (2019) Robust image hashing scheme based on low-rank decomposition and path integral LBP. IEEE Access 7:51656–51664
Zhao Y, Wang S, Zhang X, Yao H, security (2012) Robust hashing for image authentication using Zernike moments and local features. IEEE Transactions on Information Forensics and Security 8(1):55–63
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Abbas, S.Q., Ahmed, F. & Chen, YP.P. Perceptual image hashing using transform domain noise resistant local binary pattern. Multimed Tools Appl 80, 9849–9875 (2021). https://doi.org/10.1007/s11042-020-10135-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10135-w