Abstract
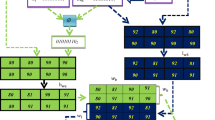
Protection of intellectual property rights has become one of the focuses of social concerning. To reduce those disputations, the watermark is implanted into the media by the content owner to declare original copyright. Among which, the high payload can achieve the accurate tampering localization, but maybe bring low visual quality watermarked image. Both accurate tampering localization and high watermarked image quality seem contradictory. For this, this paper proposes a hybrid-Sudoku based fragile watermarking scheme for digital image tampering detection. The hybrid-Sudoku based scheme provides a double perspective mechanism to embed the watermark. In the first perspective of the Sudoku, the watermark is virtually embedded into each pixel pair, resulting in the temporary coordinate information. Then, the temporary coordinate information is concealed into cover image based on the second perspective of the Sudoku. Finally, several common attacks are utilized to evaluate the tampering detection performance of the proposed method. Experimental results show that the proposed scheme can achieve a considerable accuracy in tampering localization and provide the satisfactory visual quality of watermarked image, with PSNR of 47.80 dB. Additionally, the design enhances the security and imperceptive of the hidden watermark.












Similar content being viewed by others
References
Ahmed F, Siyal MY, Abbas VU (2010) A Secure and Robust Hash-Based Scheme for Image Authentication. Signal Process 90(5):1456–1470
Chan CS, Chang CC (2007) An Efficient Image Authentication Method Based on Hamming Code. Pattern Recognition 40(2):681–690
Chang CC, Chou YC, Kieu TD (2008) An Information Hiding Scheme Using Sudoku. In: Proceedings of the 3rd International Conference on Innovative Computing Information and Control. IEEE, Liaoning, pp 17–22
Chen YL, Yau HT, Yang GJ (2013) A Maximum Entropy-Based Chaotic Time-Variant Fragile Watermarking Scheme for Image Tampering Detection. Entropy 15(8):3170–3185
Ding W, Xie Y, Wang Y (2019) Image Authentication and Tamper Localization Based on Relative Difference between DCT Coefficient and Its Estimated Value. Multimed Tools Appl 78(5):5305–5328
Ghosal SK, Mandal JK (2013) Stirling Transform Based Color Image Authentication. Procedia Technol 1st International Conference on Computational Intelligence: Modeling Techniques and Applications 10:95–104
Ghosal SK, Mandal JK (2014) Binomial Transform Based Fragile Watermarking for Image Authentication. J Information Secur Appl 19(4–5):272–281
Gong X, Chen L, Yu F, Zhao X, Wang S (2020) A Secure Image Authentication Scheme Based on Dual Fragile Watermark. Multimed Tools Appl. https://doi.org/10.1007/s11042-019-08594-x
Gul E, Ozturk S (2019) A Novel Hash Function Based Fragile Watermarking Method for Image Integrity. Multimed Tools Appl 78(13):17701–17718
Gupta A, Jha RK (2015) A Survey of 5G Network: Architecture and Emerging Technologies. IEEE Access 3:1206–1232
Ho ATS, Zhu X, Guan YL (2004) Image Content Authentication Using Pinned Sine Transform. EURASIP J Advances Signal Process 14:2174–2184
Hong W, Chen TS, Shiu CW (2008) Steganography Using Sudoku Revisited. In: Proceedings of 2008 Second International Symposium on Intelligent Information Technology Application, Shanghai, China, 935–939
Hong W, Chen TS, Shiu CW (2008) A Minimal Euclidean Distance Searching Technique for Sudoku Steganography. In: Proceedings of 2008 International Symposium on Information Science and Engineering, Shanghai, China, 1: 515–518
Hore, A. and Ziou, D., “Image Quality Metrics: PSNR vs. SSIM,” In Proceedings of 2010 20th International Conference on Pattern Recognition. IEEE, Istanbul, Aug. 2010: 2366–2369.
Hu YC, Lo CC, Wu CM, Chen WL, Wen CH (2013) Probability-Based Tamper Detection Scheme for BTC-Compressed Images Based on Quantization Levels Modification. Int J Secur Appl 7(3):11–32
Kang, X. B. and Wei, S. M., “Identifying Tampered Regions Using Singular Value Decomposition in Digital Image Forensics,” In Proceedings of 2008 International Conference on Computer Science and Software Engineering. IEEE, Hubei, Dec. 2008, 3: 926–930.
Lin CC, Huang Y, Tai WL (2017) A Novel Hybrid Image Authentication Scheme Based on Absolute Moment Block Truncation Coding. Multimed Tools Appl 76(1):463–488
Lu H, Shen R, Chung FL (2003) Fragile Watermarking Scheme for Image Authentication. Electronics Lett 39(12):898–900
Mandal JK, Ghosal SK (2013) Separable Discrete Hartley Transform Based Invisible Watermarking for Color Image Authentication (SDHTIWCIA). In: Advances in Computing and Information Technology. Springer, Berlin, pp 767–776
Memon NA, Alzahrani A (2020) Prediction-Based Reversible Watermarking of CT Scan Images for Content Authentication and Copyright Protection. IEEE Access 8:75448–75462
Prasad S, Pal AK (2020) A Tamper Detection Suitable Fragile Watermarking Scheme Based on Novel Payload Embedding Strategy. Multimed Tools Appl 79(3):1673–1705
Rawat S, Raman B (2011) A Chaotic System Based Fragile Watermarking Scheme for Image Tamper Detection. AEU-Int J Electron Commun 65(10):840–847
Schaefer, G. and Stich, M., “UCID: An Uncompressed Color Image 807 Database,” in Proc SPIE, Dec. 2003, 5307: 472–480.
Simonis H (2005) Sudoku as A Constraint Problem. CP Workshop Model Reformulat Constraint Satisfact Prob 12:13–27
Su GD, Liu Y, Chang CC (2019) A Square Lattice Oriented Reversible Information Hiding Scheme with Reversibility and Adaptivity for Dual Images. J Visual Commun Image Represent 64:102618
Su GD, Chang CC, Lin CC (2019) High-Precision Authentication Scheme Based on Matrix Encoding for AMBTC-Compressed Images. Symmetry in Engineering Sciences II 11(8):996
Tong X, Liu Y, Zhang M, Chen Y (2013) A Novel Chaos-Based Fragile Watermarking for Image Tampering Detection and Self-Recovery. Signal Process: Image Commun 28(3):301–308
Walton S (1995) Image Authentication for A Slippery New Age. Dr Dobb’s J 20(4):18–26
Wang Z, Bovik AC (2002) A Universal Image Quality Index. IEEE Signal Process Lett 9(3):81–84
Wong PW (1998) A Watermark for Image Integrity and Ownership Verification. In: Proceedings of PICS, Portland, 374–379
Yeung, M. M. and Mintzer, F., “An Invisible Watermarking Technique for Image Verification,” In Proceedings of International Conference on Image Processing, Santa Barbara, Oct. 1997, 2: 680–683.
Yi F, Kim Y, Moon I (2018) Secure Image-Authentication Schemes with Hidden Double Random-Phase Encoding. IEEE Access 6(1):70113–70121
Zahariadis T (2003) Trends in the Path to 4G. Commun Engineer 1(1):12–15
Acknowledgements
This work was supported by the Open Fund of Engineering Research Center for ICH Digitalization and Multi-Source Information Fusion of Fujian Province (FJ-ICH201901), the Education-Scientific Research Project for Middle-Aged and Young of Fujian Province (JT180621, JAT190488 and JAT201368).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Su, GD., Chang, CC. & Chen, CC. A hybrid-Sudoku based fragile watermarking scheme for image tampering detection. Multimed Tools Appl 80, 12881–12903 (2021). https://doi.org/10.1007/s11042-020-10451-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10451-1