Abstract
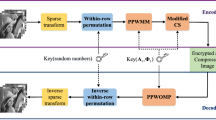
In this paper, a novel scheme is proposed for multi-sourced signal fusion and secure processing. Within a distributed compressed sensing (DCS) framework, traditional sampling, compression and encryption for signal acquisition are unified under the secure multiparty computation protocol. In the proposed scheme, generation of the pseudo-random sensing matrix offers a natural method for data encryption in DCS, allowing for joint recovery of multiparty data at legal users’ side. Experimental analysis and results indicate that the secure signal processing and recovery in DCS domain is feasible, and requires fewer measurements than the achievable approach of separate CS and Nyquist processing. The proposed scheme can be also extended to other cloud-based collaborative secure signal processing and data-mining applications.









Similar content being viewed by others
References
Akshay, J. (2011). Enhancing security in cloud computing. Information and Knowledge Management, 1(1), 40–43.
Baron, D., Duarte, M. F., Sarvotham, S. et al. (2005). An information-theoretic approach to distributed compressed sensing. In Proceedings of the 43rd Allerton conference communication, control, and computing, Monticello, IL.
Behl, A. (2011) Emerging security challenges in cloud computing. In Proceedings of the world congress on information and communication technology, pp. 217–218.
Candès, E. J. (2008). The restricted isometry property and its implications for compressed sensing. Comptes Rendus - Mathématique, 346(9), 589–592.
Candes, E., Romberg, J., & Tao, T. (2006). Robust uncertainty principles: Exact signal reconstruction from highly incomplete frequency information. IEEE Transactions on Information Theory, 52(2), 489–509.
Chen, W., Rodrigues, M., & Wassell, I. (2011) Distributed compressive sensing reconstruction via common support discovery. In Proceedings of the IEEE international conference on communications.
Dan, W., & Wang, R. H. (2014). Robustness of orthogonal matching pursuit under restricted isometry property. Science China Mathematics, 57(3), 627–634.
Donoho, D., & Tsai, Y. (2006). Extensions of compressed sensing. Signal Processing, 86(3), 533–548.
Duarte, M. F., Sarvotham, S., Baron, D. et al. (2008). Performance limits for jointly sparse signals via graphical models. In Workshop on sensor, signal and information processing (SENSIP), Sedona, AZ.
Fingerprint verification competition. http://biometrics.cse.msu.edu/fvc04db/index.html.
Han, J., He, S., Qian, X., Wang, D., Guo, L., & Liu, T. (2013). An object-oriented visual saliency detection framework based on sparse coding representations. IEEE Transactions on Circuits and Systems for Video Technology, 23(12), 2009–2021.
Han, J., Zhang, D., Cheng, G., Guo, L., & Ren, J. (2015). Object detection in optical remote sensing images based on weakly supervised learning and high-level feature learning. IEEE Transactions on Geoscience and Remote Sensing, 53(6), 3325–3337.
Han, J., Zhang, D., Hu, X., Guo, L., Ren, J., & Wu, F. (2015). Background prior based salient object detection via deep reconstruction residual. IEEE Transactions on Circuits and Systems for Video Technology, 25(8), 1309–1321.
Han, J., Zhou, P., Zhang, D., Cheng, G., Guo, L., Liu, Z., et al. (2014). Efficient, simultaneous detection of multi-class geospatial targets based on visual saliency modeling and discriminative learning of sparse coding. ISPRS Journal of Photogrammetry and Remote Sensing, 89, 37–48.
Hou, X., Yang, J., Jiang, G., & Qian, X. (2013). Complex SAR image compression based on directional lifting wavelet transform with high clustering capability. IEEE Transactions on Geoscience and Remote Sensing, 51(1), 527–538.
Hou, X., Zhang, L., Gong, C., Xiao, L., Sun, J., & Qian, X. (2014). SAR image Bayesian compressive sensing exploiting the interscale and intrascale dependencies in directional lifting wavelet transform domain. Neurocomputing, 133, 358–368.
Jiang, J., et al. (2011). Live: an integrated production and feedback system for intelligent and interactive tv broadcasting. IEEE Transactions on Broadcasting, 57(3), 646–661.
Liu, Y., Ma, Y., Zhang, H., et al. (2011). A method for trust management in cloud computing: Data coloring by cloud watermarking. International Journal Automation and Computing, 8(3), 280–285.
Lu, W., Varna, A., & Wu, M. (2010). Security analysis for private preserving search for multimedia. In Proceedings of the IEEE 17th international conference on image processing.
Masoum, A., Merana, N., & Havinga, P. (2013). A distributed compressive sensing technique for data gathering in wireless sensor network. Procedia Computer Science, 21, 207–216.
Mishra, D., Koria, N., Kapoor, N., et al. (2009). A secure multi-party computation protocol for malicious computation prevention for preserving privacy during data mining. International Journal of Computer Science & Information Security, 3(1), 1–6.
Orsdemir, A., Altun, H. O., Sharma, G., & Bocko, M. F. (2008). On the security and robustness of encryption via compressed sensing. In IEEE military communications conference, pp. 1040–1046.
Rachlin, Y., & Baron, D. (2008). The secrecy of compressed sensing measurements. In: Proceedings of the 46th annual Allerton conference on communication, control and computing, IEEE, Illinois, USA, pp. 813–817.
Ren, J., & Jiang, J. (2009). Hierarchical modelling and adaptive clustering for real-time summarization of rush videos. IEEE Transactions on Multimedia, 11(5), 906–917.
Rong, C., Nguyen, S. T., & Jaatun, M. G. (2013). Beyond lightning: A survey on security challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47–54.
Shiraki, Y., & Kabashima, Y. (2015). Typical reconstruction limits for distributed compressed sensing based on \(\ell _{2,1}\)-norm minimization and Bayesian optimal reconstruction. Journal of Statistical Mechanics: Theory and Experiment, 2015, P05029. doi:10.1088/1742-5468/2015/05/P05029.
Sun, M., Zhang, D., Wang, Z., Ren, J., & Jin, J. S. (2016). Monte Carlo convex hull models for classification of traditional Chinese paintings. Neurocomputing 171(1), 788–797.
Sundman, D., Chatterjee, S., & Skoglund, M. (2014). Methods for distributed compressed sensing. Journal of Sensor and Actuator Networks, 3, 1–25.
Wang, C., Zhang, B., Ren, K., et al. (2013). Privacy-assured outsourcing of image reconstruction service in cloud. IEEE Transactions on Emerging Topics in Computing, 1(1), 166–177.
Yang, X., Qian, X., & Mei, T. (2015). Learning salient visual word for scalable mobile image retrieval. Pattern Recognition, 48(10), 3093–3101.
Yang, X., Qian, X., & Xue, Y. (2015). Scalable mobile image retrieval by exploring contextual saliency. IEEE Transactions on Image Processing, 24(6), 1709–1721.
Yin, H., Li, J., Chai, Y., et al. (2014). A survey on distributed compressed sensing: Theory and applications. Frontiers of Computer Science, 8(6), 893–904.
Zhang, Y., Niu, X., & Zhao, D. (2005). A method of protecting relational databases copyright with cloud watermarking (pp. 68–72). Istanbul: World Academy of Science, Engineering and Technology.
Zhao, H., & Fang, Y. (2015). On the security and robustness with fingerprint watermarking signal via compressed sensing. International Journal of Security and Its Applications, 9(1), 221–236.
Zhao, C., Li, X., Ren, J., & Marshall, S. (2013). Improved sparse representation using adaptive spatial support for effective target detection in hyperspectral imagery. International Journal of Remote Sensing, 34(24), 8669–8684.
Acknowledgments
The authors would greatly thank the anonymous reviewers and the editors for their constructive comments to further improve this paper. This work was supported by the National Natural Science Foundation of China (61272381, 61571141), Science and Technology Major Project of Education Department of Guangdong Province (2014KZDXM060), and the Natural Science Foundation of Guangdong (2015A030313672), and Science and Technology Project of Guangzhou City (2014J4100078).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhao, H., Wei, W., Cai, J. et al. Distributed compressed sensing for multi-sourced fusion and secure signal processing in private cloud. Multidim Syst Sign Process 27, 891–908 (2016). https://doi.org/10.1007/s11045-015-0371-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11045-015-0371-2