Abstract
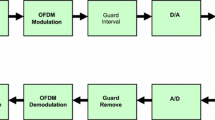
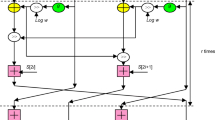
In this paper, a novel hybrid 3D Video (3DV) encryption framework based on the Rubik's cube is suggested to attain simultaneous encryption of a group of 3DV frames. The suggested hybrid encryption framework begins with chaotic Baker map permutation, Advanced Encryption Standard (AES), or Ron's Code (RC6) technique implemented in Cipher Feedback (CFB) mode of operation as a first step for encrypting the multiple 3DV frames, separately. Then, the resulting encrypted 3DV frames are further encrypted in a second stage with Rubik's cube technique. The chaotic, RC6, or AES encrypted 3DV frames are utilized as the faces of the Rubik's cube. The RC6 and the AES techniques introduce a degree of diffusion from the concepts of image encryption, while the chaotic Baker map adds a degree of permutation. Moreover, the Rubik's cube technique simultaneously adds more permutations to the encrypted 3DV frames. The encrypted 3DV frames are further transmitted over a wireless channel with different Orthogonal Frequency Division Multiplexing (OFDM) versions and decrypted at the receiver side. The quality evaluation of the decrypted 3DV frames at the receiver side reveals good performance. The simulation results prove that the suggested hybrid encryption framework is reliable and it presents recommended security and robustness levels.




















Similar content being viewed by others
References
Abreu, A., Frossard, P., & Pereira, F. (2015). Optimizing multiview video plus depth prediction structures for interactive multiview video streaming. IEEE Journal of Selected Topics in Signal Processing, 9(3), 487–500.
Alpar, O. (2017). A new chaotic map with three isolated chaotic regions. Nonlinear Dynamics, 87(2), 903–912.
Alsisi, R. H., & Rao, R. K. (2017). BER comparison of constant envelope DCT and FFT based OFDM with phase modulation. In International conference on network-based information systems (pp. 959–968). Springer.
Cagri, O., Erhan, E., Janko, C., & Ahmet, K. (2016). Adaptive delivery of immersive 3D multi-view video over the Internet. Multimedia Tools Appl, 75(20), 12431–12461.
Chai, X., Gan, Z., & Zhang, M. (2017). A fast chaos-based image encryption scheme with a novel plain image-related swapping block permutation and block diffusion. Multimedia Tools and Applications, 76(14), 15561–15585.
Dhote, K., & Asutkar, G. M. (2016). Enhancement in the performance of routing protocols for wireless communication using clustering, encryption, and cryptography. In Artificial intelligence and evolutionary computations in engineering systems (pp. 547–558). Springer.
Durdi, V. B., Kulkarni, P. T., & Sudha, K. L. (2017). Selective encryption framework for secure multimedia transmission over wireless multimedia sensor networks. In Proceedings of the international conference on data engineering and communication technology (pp. 469–480). Springer.
Eldokany, I., El-Rabaie, E., Elhalafawy, S., Eldin, M., Shahieen, M., Soliman, N., & El-Samie, F. (2015). Efficient transmission of encrypted images with OFDM in the presence of carrier frequency offset. Wireless Personal Communications, 84(1), 475–521.
El-Shafai, W., El-Rabaie, S., El-Halawany, M. M., & El-Samie, F. E. A. (2017a). Encoder-independent decoder-dependent depth-assisted error concealment algorithm for wireless 3D video communication. Multimedia Tools and Applications, 77, 1–28.
El-Shafai, W., El-Rabaie, S., El-Halawany, M. M., & El-Samie, F. E. A. (2017b). Enhancement of wireless 3D video communication using color-plus-depth error restoration algorithms and bayesian Kalman filtering. Wireless Personal Communications, 97(1), 245–268.
El-Shafai, W., El-Rabaie, S., El-Halawany, M. M., & El-Samie, F. E. A. (2018). Performance evaluation of enhanced error correction algorithms for efficient wireless 3D video communication systems. International Journal of Communication Systems, 31(1), e3396.
Enerstvedt, O. M. (2017). Analysis of privacy and data protection principles. In Aviation security, privacy, data protection and other human rights: Technologies and legal principles (pp. 307–394). Springer.
Faragallah, O., El-Samie, F., Ahmed, H., Elashry, I., Shahieen, M., El-Rabaie, E., & Alshebeili, S. (2013). Image encryption: A communication perspective. CRC Press.
H.264/AVC codec, 28/09/2016. http://iphome.hhi.de/suehring/tml/
Hamid, A., Samir, M., El-atty, A., El-Hennawy, E., El Shenawy, H., Alshebeili, A., & El-Samie, F. (2014). On the performance of FFT/DWT/DCT-based OFDM systems with chaotic interleaving and channel estimation algorithms. Wireless Personal Communications, 78(2), 1495–1510.
Helmy, M., El-Rabaie, E., Eldokany, I., & El-Samie, F. (2017). 3-D image encryption based on Rubik’s cube and RC6 algorithm. 3D Research, 8(4), 38.
Helmy, M., El-Rabaie, E., Eldokany, I., & El-Samie, F. (2018). Chaotic encryption with different modes of operation based on Rubik’s cube for efficient wireless communication. Multimedia Tools and Applications, 77, 1–25.
Hewage, C. T. E. R., & Martini, M. G. (2013). Quality of experience for 3D video streaming. IEEE Communications Magazine, 51(5), 101–107.
Hilmey, M., Elhalafwy, S., & Eldin, M. (2009). Efficient transmission of chaotic and AES encrypted images with OFDM over an AWGN channel. In Proceedings of the IEEE international conference of computer engineering and systems (pp. 353–358).
Hu, L., Li, Y., Li, T., Li, H., & Chu, J. (2016). The efficiency improved scheme for secure access control of digital video distribution. Multimedia Tools and Applications, 75(20), 12645–12662.
Huanqiang, Z., Xiaolan, W., Canhui, C., Jing, C., & Yan, Z. (2014). Fast multiview video coding using adaptive prediction structure and hierarchical mode decision. IEEE Transactions on Circuits and Systems for Video Technology, 24(9), 1566–1578.
ISO/IEC JTC1/SC29/WG11. (2006). Common test conditions for multiview video coding. JVT-U207.
Lian, S. (2009). Efficient image or video encryption based on spatiotemporal chaos system. Chaos, Solitons & Fractals, 40(5), 2509–2519.
Liu, L., & Miao, S. (2018). A new simple one-dimensional chaotic map and its application for image encryption. Multimedia Tools and Applications, 77, 1–18.
Liu, Y., Zhang, L. Y., Wang, J., Zhang, Y., & Wong, K. W. (2016). Chosen-plaintext attack of an image encryption scheme based on modified permutation–diffusion structure. Nonlinear Dynamics, 84(4), 2241–2250.
Liu, Z., Cheung, G., & Ji, Y. (2013). Optimizing distributed source coding for interactive multiview video streaming over lossy networks. IEEE Transactions on Circuits and Systems for Video Technology, 23(10), 1781–1794.
Madaan, V., Sethi, D., Agrawal, P., Jain, L., & Kaur, R. (2017). Public network security by bluffing the intruders through encryption over encryption using public key cryptography method. In Advanced informatics for computing research (pp. 249–257). Springer.
Naik, B. V., Sai, N. L. K., & Kumar, C. M. (2017). Efficient transmission of encrypted images with OFDM system. In IEEE international conference on power, control, signals and instrumentation engineering (ICPCSI).
Rajpoot, Q. M., & Jensen, C. D. (2014). Security and privacy in video surveillance: requirements and challenges. In IFIP international information security conference (pp. 169–184). Springer.
Reference software for multiview video coding (mvc). Retrieved October 25, 2016, from http://wftp3.itu.int/av-arch/jvt-site/2009_01_Geneva/JVT-AD207.zip
Retrieved May, 2015, from http://www.puzzles9.com/p/introduction-puzzle-isproblem-or.html
Sharma, D., & Srivastava, P. (2013). OFDM simulator using MATLAB. International Journal of Emerging Technology and Advanced Engineering, 3(9), 493–496.
Souyah, A., & Faraoun, K. M. (2016). A review on different image encryption approaches. In Modelling and implementation of complex systems (pp. 3–18). Springer International Publishing.
Varshney, N., & Raghuwanshi, K. (2016). RC6 based data security and attack detection. In Proceedings of first international conference on information and communication technology for intelligent systems (pp. 3–10). Springer International Publishing.
Volte, E., Patarin, J., & Nachef, V. (2013). Zero knowledge with Rubik's cubes and non-abelian groups. In International conference on cryptology and network security (pp. 74–91). Springer.
Winkler, P. (2003). Mathematical puzzles: A connoisseur’s collection. AK Peters/CRC Press.
Wu, J., Zhu, Z., & Guo, S. (2017). A quality model for evaluating encryption-as-a-service. In International conference on security, privacy and anonymity in computation, communication and storage (pp. 557–569). Springer.
Xiang, W., Gao, P., & Peng, Q. (2015). Robust multiview three-dimensional video communications based on distributed video coding. IEEE Systems Journal, PP(99), 1–11.
Yan, C., Li, L., Zhang, C., Liu, B., Zhang, Y., & Dai, Q. (2019a). Cross-modality bridging and knowledge transferring for image understanding. IEEE Transactions on Multimedia, 21, 2675–2685.
Yan, C., Tu, Y., Wang, X., Zhang, Y., Hao, X., Zhang, Y., & Dai, Q. (2019b). STAT: Spatial-temporal attention mechanism for video captioning. IEEE Transactions on Multimedia, 22, 229–241.
Yan, C., Xie, H., Chen, J., Zha, Z., Hao, X., Zhang, Y., & Dai, Q. (2018). A fast Uyghur text detector for complex background images. IEEE Transactions on Multimedia, 20(12), 3389–3398.
Zhang, X., Seo, S., & Wang, C. (2018). A lightweight encryption method for privacy protection in surveillance videos. IEEE Access, 6, 18074–18087.
Zheng, X. (2017). The application of information security encryption technology in military data system management. In International conference on man-machine-environment system engineering (pp. 423–428). Springer.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Helmy, M., El-Shafai, W., El-Rabaie, S. et al. Efficient security framework for reliable wireless 3D video transmission. Multidim Syst Sign Process 33, 181–221 (2022). https://doi.org/10.1007/s11045-021-00796-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11045-021-00796-7